Can You Spot The Signs of Ransomware? Follow This Simple Guide To Protect Yourself

The number of reported ransomware attacks exploded in 2020. This guide will give you the knowledge to identify the signs of ransomware, respond to an attack, and implement methods to protect yourself in the future. What is Ransomware and Why Should You Care? Ransomware is a form of malware that encrypts and holds hostage user […]
HIPAA Compliant Cloud Storage – The 11 Best Services To Consider

“What are my options for HIPAA-compliant cloud storage? ” In recent years, cloud storage has risen in both effectiveness and popularity. Its convenience is undeniable– the ability to access your data from anywhere is amazing. But can business associates and medical providers take advantage of these services to store PHI? What exactly does it mean […]
The 21 Most Common CMMC Technology Projects

Are you getting ready to start down the path of getting your CMMC certification? Based on our recent NIST 800-171 / CMMC projects, here are the 21 most common technology projects that we see companies needing to implement in order to comply. Windows 10 on all PCs where possible. In-support versions of all server OS […]
5 Free Mac Cybersecurity Tips
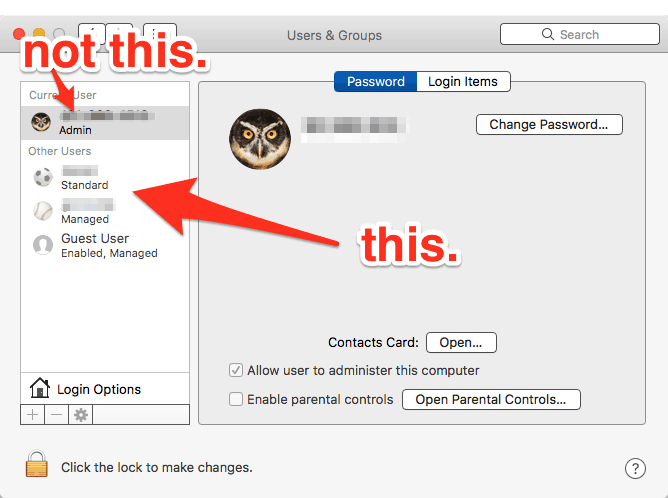
Are you a Mac user? Check out these five free Mac cybersecurity tips. They’re quick and easy, and something you should do right now. These will help you with your cybersecurity compliance and reduce the risk that you’ll be hacked. 1) Encrypt your hard drive Use FileVault, Apple’s built-in hard drive encryption utility. You can […]
HIPAA Email Encryption: We Reviewed 7 Services and Found the Best
Navigating the complexities of HIPAA-compliant email encryption service providers can be challenging for healthcare providers and other regulated businesses. Questions like “How can we securely send PHI via email while maintaining HIPAA compliance?” and “What are the best practices for encrypted email with platforms like Gmail or Microsoft 365?” are common concerns we hear from […]
Is Gmail HIPAA Compliant? (3 Useful Points)

Though Gmail is not HIPAA compliant by default, it can be configured to meet HIPAA standards in 2025. For healthcare providers, adhering to the Health Insurance Portability and Accountability Act (HIPAA) is essential to safeguard patient privacy. While Gmail is not automatically HIPAA compliant, this article will show you how you can make it HIPAA […]
Ransomware Playbook: 31 Critical Questions to Build Your Own

Are you worried about ransomware? You should be. Ransomware is hitting companies of all sizes, sometimes with disastrous results. Many companies need to put together a specific plan for ransomware, known as a “ransomware playbook.” We think even small firms should spend some time planning what they will do if they’re hit. When ransomware hits, […]
Is Gmail Encryption HIPAA-Compliant?

We’ve recently discussed whether or not Gmail is HIPAA-compliant. In short, it depends. Gmail is HIPAA-compliant when set up correctly. But what about Gmail encryption? Is Gmail encryption HIPAA compliant? Once again, it depends. Gmail encryption also has the potential to be a HIPAA-compliant email option depending on how you set it up. Feature Download: […]
Is Microsoft 365 HIPAA-Compliant? How to make it secure?

Healthcare providers must follow the Health Insurance Portability and Accountability Act (HIPAA). Is Microsoft 365 HIPAA-compliant, though? is outlook encrypted email hipaa compliant? This act protects your patient’s healthcare data (PHI). As more clinicians are electronically transmitting patient records and other personal information to specialists and medical facilities, we must ensure that information is secure […]