The number of reported ransomware attacks exploded in 2020. This guide will give you the knowledge to identify the signs of ransomware, respond to an attack, and implement methods to protect yourself in the future.
Ransomware is a form of malware that encrypts and holds hostage user data until they pay a ransom. It’s one of the more dangerous cyberthreats to businesses in 2020. An organization that falls victim to one of these attacks could face costly downtime and the loss of important data.
The frequency of ransomware attacks exploded in 2020. Cyber criminals capitalized on the effectiveness of COVID-19 related scams. A recent report from Bitdefender indicated a 715% year over year increase in these types of attacks.
Want to see for yourself? Try searching “ransomware attack” in Google News.
Ransomware's goal is to spread and gain control of as much of your data as possible. After all, the more data the cybercriminals have control over, the more they can demand in ransom. Being able to identify the signs of ransomware and quickly implementing a remediation strategy can save you a lot of time and money.
So, what do these attacks look like and what should you do if ever faced with one? Let’s find out.
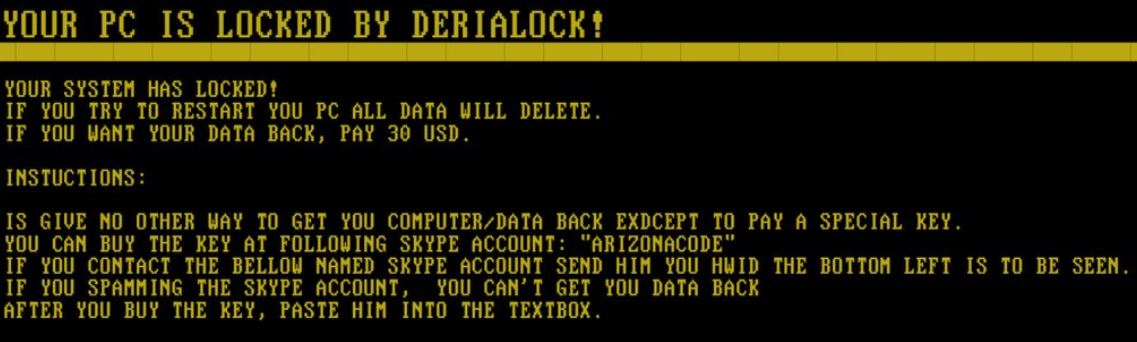
One of the most glaring signs of ransomware infection is a pop-up or a start screen that locks the user out of their computer and demands payment. These pop-ups will look similar to the image below.
The group of letters occurring after the period in a file name is the file extension. They show the format of the file and let the computer know which program to open.
Some common file extensions that you are likely familiar with are .DOC, .CSV, .PDF, and .JPG.
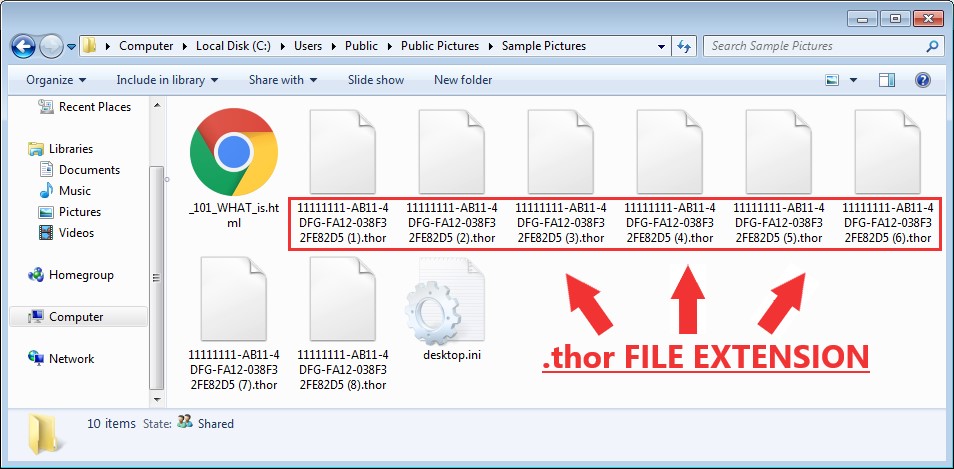
Encrypted files will often display unusual file extensions. Extensions like .MICRO, .ZEPTO, and .THOR. This list from TechViral contains most of the file extensions known to be associated with ransomware that you should look out for.
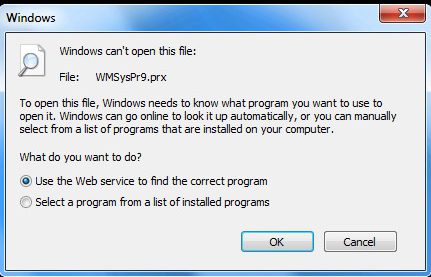
You won’t be able to open encrypted files. If you begin to notice an error message when trying to open your files, it could be due to ransomware.
A Windows user trying to open an encrypted file will usually encounter this message:
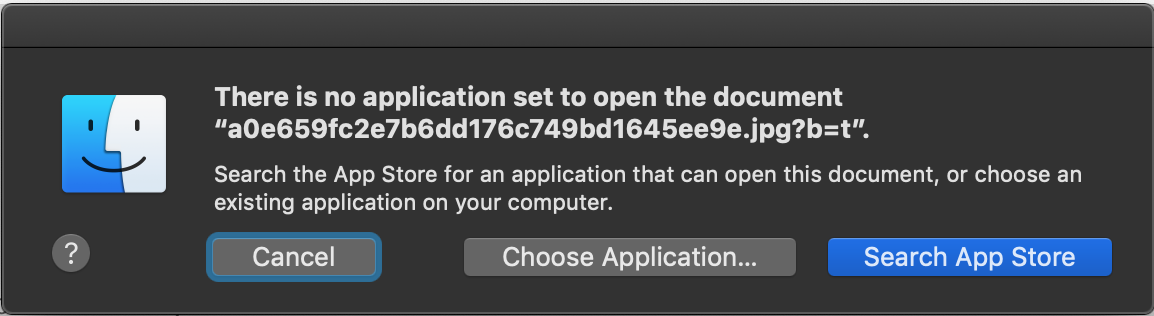
A Mac user trying to open an encrypted file will usually encounter this message:
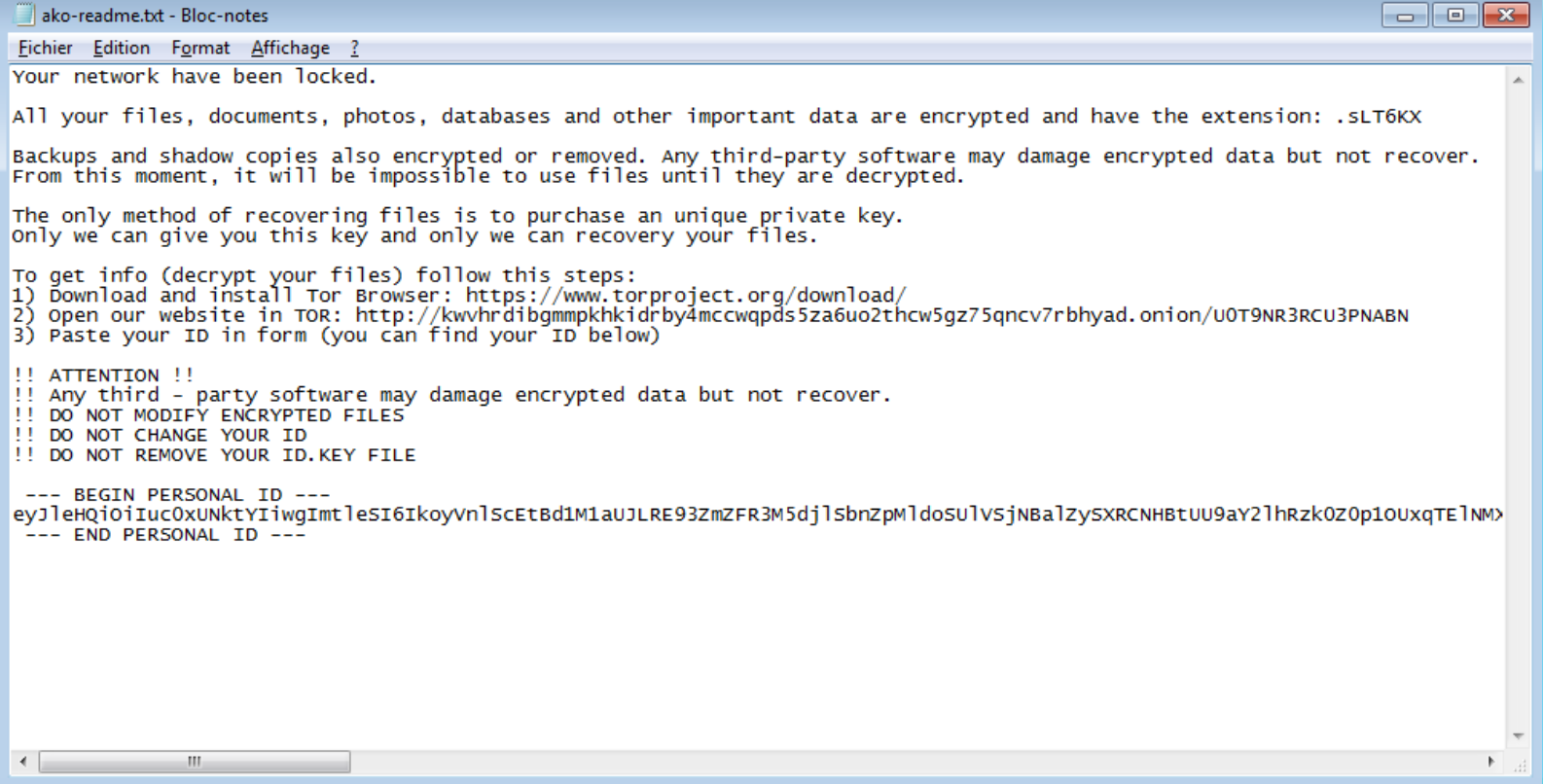
Cybercriminals using ransomware will upload their own files onto your computer. These files will usually be in TXT or HTML format, and will include instructions on how to pay the ransom.
Users should be on the lookout for files with unusual names that they did not create. Names like “_READ ME_.txt" or “_INSTRUCTIONS FOR DECRYPTION_.txt"
These files, once opened, will usually look like the image below.
The first step after detecting any of these signs of ransomware is controlling the spread of the infection.
Disconnect the infected computers from the internet and any local area networks, remove all external storage devices, unplug the network cable, and turn off the WIFI.
These steps will help isolate the infected systems.
You need to figure out which type of ransomware has infected your system. This will help you decide which decryption tool to use in the following steps. Bitdefender’s ransomware recognition tool may work here, though some ransomware is too new to show up on their list.
If you or your company are being held hostage by ransomware, your first call should be to your cybersecurity insurance breach hotline. They’ll have the technical, legal, and law enforcement contacts to help you figure out your next steps.
If you don’t have it yet, our previous article Do you Need Cybersecurity Insurance? contains helpful information on the topic.
If available, wipe the infected computers and reboot them from a recent backup.
If that is not an option, there are ransomware removal tools available online. Those available from AVG and Trend Micro are both good options for this step.
Keeping your hard drive backed up is the best defense against ransomware. Set up a schedule that automatically backs up your system on a daily basis. You will thank yourself later.
Use a non-profit site like AV-TEST.org to select an antivirus system that is best for you. Almost all modern antivirus systems include defenses against some strains of ransomware.
Cybercriminals hide ransomware in links and email attachments.
If you are unsure about an email attachment that you need to open, double check with the sender before doing so.
Always be sure that a site that you are downloading content from is trustworthy. Secure sites will usually display a lock or a shield symbol in the address bar.
Running out-of-date software exposes you to vulnerabilities that cybercriminals can take advantage of. Allowing automatic updates when installing new software will solve this problem.
