Navigating the complexities of HIPAA-compliant email encryption service providers can be challenging for healthcare providers and other regulated businesses. Questions like “How can we securely send PHI via email while maintaining HIPAA compliance?” and “What are the best practices for encrypted email with platforms like Gmail or Microsoft 365?” are common concerns we hear from organizations aiming to safeguard sensitive data.
Email is an indispensable communication tool in today's digital-first world, but for HIPAA-regulated businesses, using email to handle Protected Health Information (PHI) adds an extra layer of complexity. The good news is that sending PHI securely and in compliance with HIPAA requirements is achievable with the right tools and knowledge.
In this guide, we’ll walk you through what it takes to implement HIPAA-compliant email encryption. But first, let’s cover the essential groundwork.
If you're looking for a straightforward solution, our Secure Cloud for Healthcare provides a fast and reliable way to get started.

PHI stands for “Protected Health Information”. PHI is anything that can identify an individual and provide information about their healthcare. Think of it this way, If you are emailing ANYTHING that someone can use to figure out medical information, it's PHI.
For healthcare providers and business associates, PHI is everything. Even in places that you wouldn't think to look, like notes on a calendar or files in a “Downloads” folder. This infographic does an awesome job demonstrating all of the different places where PHI can hide.
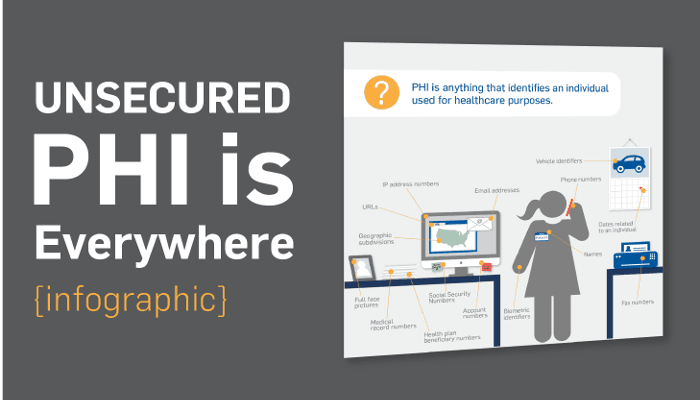
Hint: There are a lot of them.
So, you get it: PHI is important. PHI is everywhere. So what do you do?
First, you need to understand the basics of encryption.
Encryption is at the heart of many of today’s data protection tools. It’s an effective way to shield data from prying eyes.
It’s not important to understand how encryption works.
All you need to know is that you start with an ultra-important secret message:
Be sure to drink your Ovaltine.
When it gets emailed out, it looks like this to anyone who tries to intercept it:
-----BEGIN PGP MESSAGE-----
Version: BCPG C# v1.6.1.0hQIOAwfq5Jrby+ZxEAf/QOdUNAhEOSfC8FD35VYqbplUXim0t02sGEakLSgPRn5hhk8kB3e1Mcqu6WN1RGXDmb0YMZapWh0oNj0syq4InrXyZMumhrCGWJwDusCH+NEQXfC4LilogaQTxKNwaF2OjRt0I7hPBrndaKhrHVC3XftK1YKwigJuFDDgKy34/5AcfU1id+R4HJucPUzz0KBOKafMpJmjVH98qgP7DWEjb5ZOimQBi7jWJF2jnYBbceFhwpL9BwtiN0yPqaZLFrZfoGAZ8HpDNV5PRgXXe6Ajekx7Jju6sZpdX2euMzOjeRC0W0QvavFkjdVXN9x2UqlQ71S3iS/bAPQCORztWQ7LIwf+JO1q7/eHg/BSuQZkI9mRXAUaslJmqZNqMmjIt1nCC2yPXYDaHEjHfMZWZycKpBPkG6QIDjNZQXgfEoA5O+wkbBWsV/cXyYw5BPECLvcmbiG4rSJ+VS06libmdpPmdOmldNWYFk+PXbh/zAAzt1GT8eBh5o9hzBdSicFNBeSZZJW9O2mQElvKJLHHry2DK1YXpfTNeK/X02nerIqGXq3S7e05klSoIc0JoKaQNzOyJBKwOa2qmG+55HKQ3ElPYM+Y3NNzP/i1nNP/oGClR6WmcuLLYrLH69fZ5rcpPHaaASTzR2g3fzYWn4cUExHRmSYNsfCfFSrdDxawpO5jwCwMYck/ZLs7dHShx9YhQDTAOvmRN6rNadrhTLBD8VZ+7pbcWfeYSTa6K68PO7a3x604MqgveVZ3tgwCIUAweveGoWQi=yIpJ
-----END PGP MESSAGE-----
But then when your patient or customers get the email, it automatically decrypts it to deliver Ovaltine joy!
Not too complicated, right?
So, you get it: PHI is important. PHI is everywhere. So what do you do?
First, you need to understand the basics of encryption.
Encryption is at the heart of many of today’s data protection tools. It’s an effective way to shield data from prying eyes.
It’s not important to understand how encryption works.
All you need to know is that you start with an ultra-important secret message:
Be sure to drink your Ovaltine.
When it gets emailed out, it looks like this to anyone who tries to intercept it:
-----BEGIN PGP MESSAGE-----
Version: BCPG C# v1.6.1.0hQIOAwfq5Jrby+ZxEAf/QOdUNAhEOSfC8FD35VYqbplUXim0t02sGEakLSgPRn5hhk8kB3e1Mcqu6WN1RGXDmb0YMZapWh0oNj0syq4InrXyZMumhrCGWJwDusCH+NEQXfC4LilogaQTxKNwaF2OjRt0I7hPBrndaKhrHVC3XftK1YKwigJuFDDgKy34/5AcfU1id+R4HJucPUzz0KBOKafMpJmjVH98qgP7DWEjb5ZOimQBi7jWJF2jnYBbceFhwpL9BwtiN0yPqaZLFrZfoGAZ8HpDNV5PRgXXe6Ajekx7Jju6sZpdX2euMzOjeRC0W0QvavFkjdVXN9x2UqlQ71S3iS/bAPQCORztWQ7LIwf+JO1q7/eHg/BSuQZkI9mRXAUaslJmqZNqMmjIt1nCC2yPXYDaHEjHfMZWZycKpBPkG6QIDjNZQXgfEoA5O+wkbBWsV/cXyYw5BPECLvcmbiG4rSJ+VS06libmdpPmdOmldNWYFk+PXbh/zAAzt1GT8eBh5o9hzBdSicFNBeSZZJW9O2mQElvKJLHHry2DK1YXpfTNeK/X02nerIqGXq3S7e05klSoIc0JoKaQNzOyJBKwOa2qmG+55HKQ3ElPYM+Y3NNzP/i1nNP/oGClR6WmcuLLYrLH69fZ5rcpPHaaASTzR2g3fzYWn4cUExHRmSYNsfCfFSrdDxawpO5jwCwMYck/ZLs7dHShx9YhQDTAOvmRN6rNadrhTLBD8VZ+7pbcWfeYSTa6K68PO7a3x604MqgveVZ3tgwCIUAweveGoWQi=yIpJ
-----END PGP MESSAGE-----
But then when your patient or customers get the email, it automatically decrypts it to deliver Ovaltine joy!
Not too complicated, right?
Under HIPAA, there are strict rules for sending PHI over email. There are two choices:
#2 is a hassle. HIPAA-compliant email encryption is the only way to guarantee #1. Period.
If you want to send PHI over email, you need to make sure that data is encrypted.
What our clients say
Like many things in life, it isn’t as straightforward as you might think.
Also like many things in life, it’s a perpetual trade-off between cost and convenience.
When you’re choosing a solution, think about ease of use in both sending and receiving. Sure, there are encryption solutions out there that are free or low-cost.
But they aren’t worth it if they’re going to be inconvenient or disruptive.
The available solutions fall all over that spectrum. It’s up to you to decide which one will fit your needs best.
Here are a few options:
In a moment, we'll get into some more complicated encryption solutions. But first, we want to note that HIPAA does give patients autonomy over their own data.
This means that there is one way that you can send PHI to a patient in an unencrypted email.
You have to:

Be careful, though. You have to be absolutely 100% sure that you never accidentally email someone who hasn’t opted in. Because that, my friend, is a breach.
Want to explore this option? Here’s a great article that explains it in better detail.
Unfortunately, our favorite email and productivity suite (Gmail) doesn’t support sending encrypted emails. That’s a must-have when it comes to sending PHI, but it will work fine if you want to just email non-PHI.
We did find one way to send encrypted emails through Gmail, but it’s a huge pain. The tool, Secure Gmail, requires you to give the recipient a password via a non-email method.
That sort of defeats the whole purpose of using email for patient communication. It may be just fine for sporadic personal use, but it’s definitely not scalable in a business setting.
Your mileage may vary, but we don’t recommend it.
There’s only one other completely free option, and that’s to not send PHI via email at all. You can use email for things like setting up appointments, but handle PHI only through phone calls and snail mail.
Unfortunately, those are your only solutions in the $0 price range.
Search online for "secure email," and you'll inevitably see the company Virtru mentioned.
The Virtru add-on is easy to add to your account (though not very easy to use).
Once you install it, here’s how it works -- if you're using it inside of Gmail, it looks like this: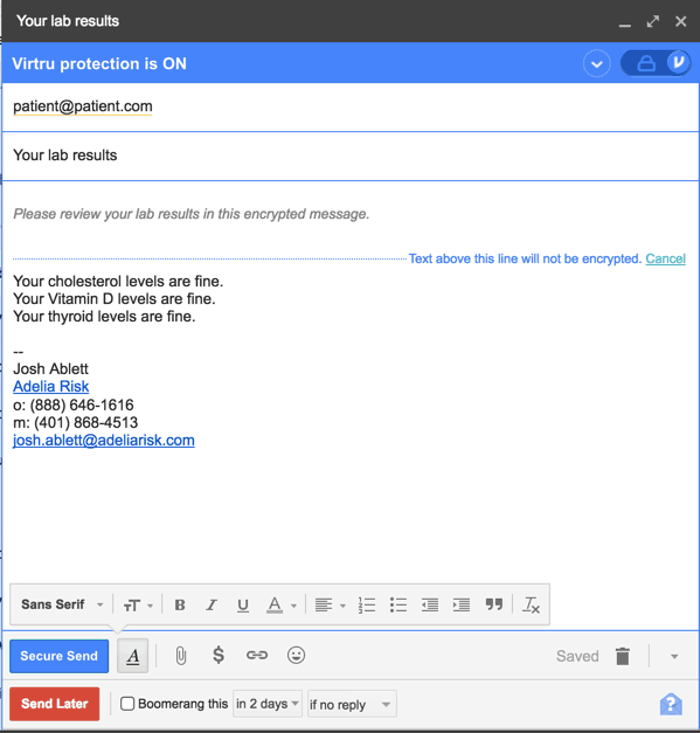
When the patient gets the email, here’s what it looks like: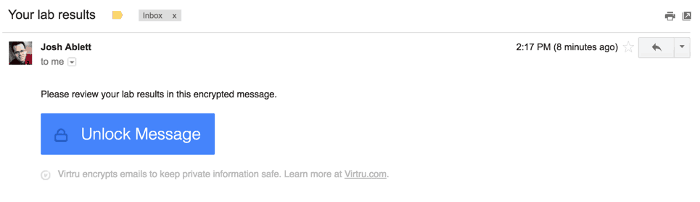
Next, the user has to click the "Unlock Message" button.
Here's where it gets a little annoying -- the user then gets another email, which supposedly verifies that this is the correct email address. Only after clicking the second email can your user access the actual message that was sent.
This double email is a double-edged sword. On the one hand, it's nice that they're not making you remember yet another username and password. On the other hand, this "double email" approach is still pretty confusing for non-technical users (especially older patients!).
On the sending side, we've also found that medical practices can find the add-ons (they also make one for Microsoft Outlook) to be pretty confusing to install. And you have to install yet another app if you want to send from your mobile phone.
Lastly, some of our customers have told us that the lowest-priced plan for which they will sign a HIPAA Business Associate agreement is over $500/year, which puts them out of the reach of some small practices. That's not a lot to pay for HIPAA compliance, but it's a lot to pay for just secure email.
If you work with an IT company, they might be giving you a HIPAA email encryption add-on. It might even be free.
Companies with names like Proofpoint, Mimecast, and Reflexion primarily focus on email security. More specifically, they protect you from phishing attacks, viruses, and ransomware emails.
All of these companies are excellent at keeping your email safe (our favorite, Proofpoint, is what we recommend to clients), but they're not that great at SENDING secure emails.
Here's how most of them work:
When you want to send someone a secure email, you'll use a keyword (like "[SECURE]") in your subject line. That's the signal to the system to encrypt the email.
Here’s an example in Gmail, though it looks the same in whatever email service you use. In fact, you can even do this on your mobile phone!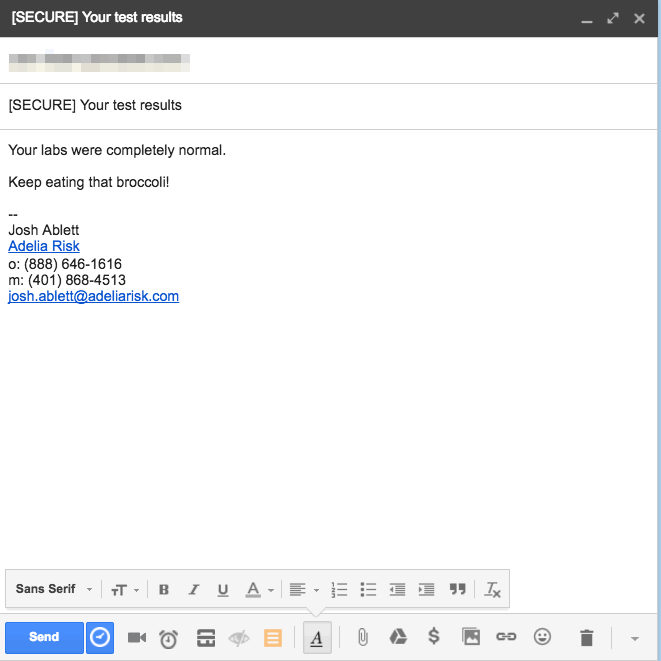
After sending it, you’ll get a nice confirmation back: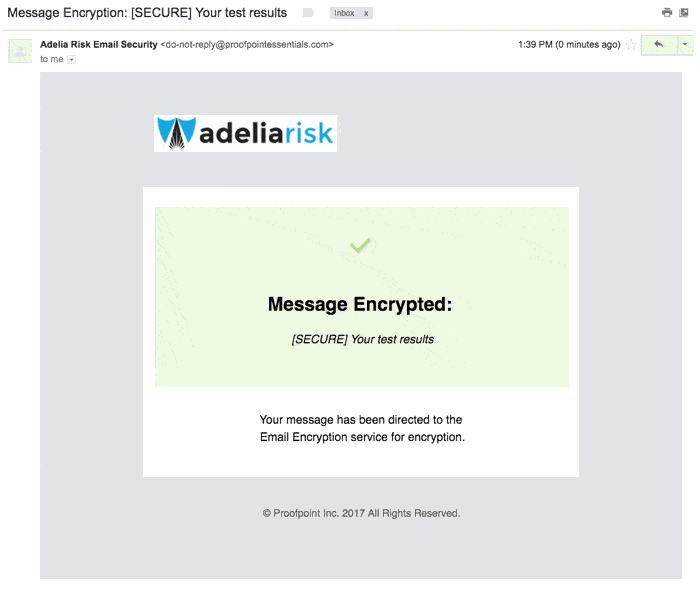
When your recipient gets the email, it will look like this: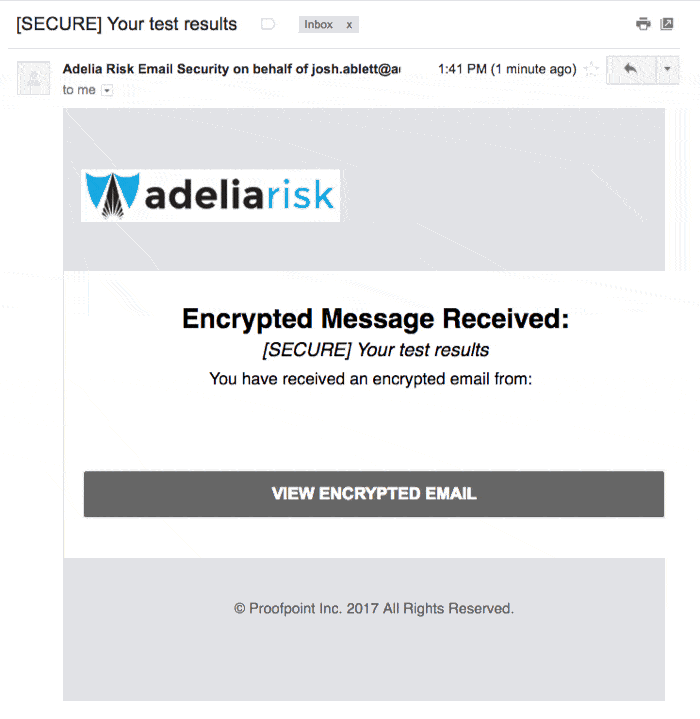
The recipient clicks on the “View Encrypted Email” button.
Sounds easy, right?
Well, not so fast. Your patient still needs to sign up for (and remember) a username and password. Patients can find this confusing.
After they log in, they will see the secure email you sent. They can also respond to it.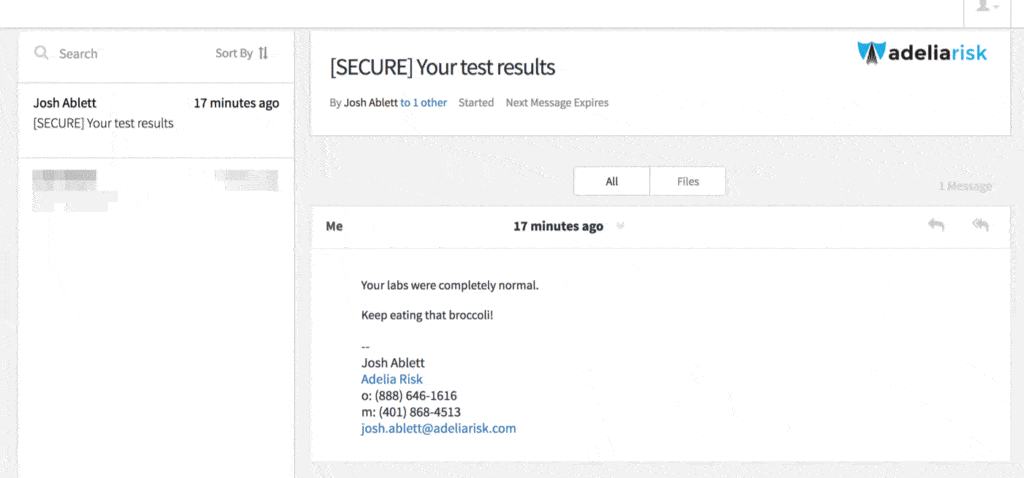
This one was near the top of our list, but when we tried it with medical practices, we had too many people complain about having to remember usernames and passwords. It can work for a really small practice that almost never sends sensitive data over email, but what if you forget to type in "secure"? It's too easy to make a mistake.
Microsoft365 can send HIPAA compliant encrypted emails but, I warn you, it's very clunky. They've made some recent improvements in early 2019 which are described below, but it's still awkward.
First, get Microsoft365.
When you send the email, it looks like this: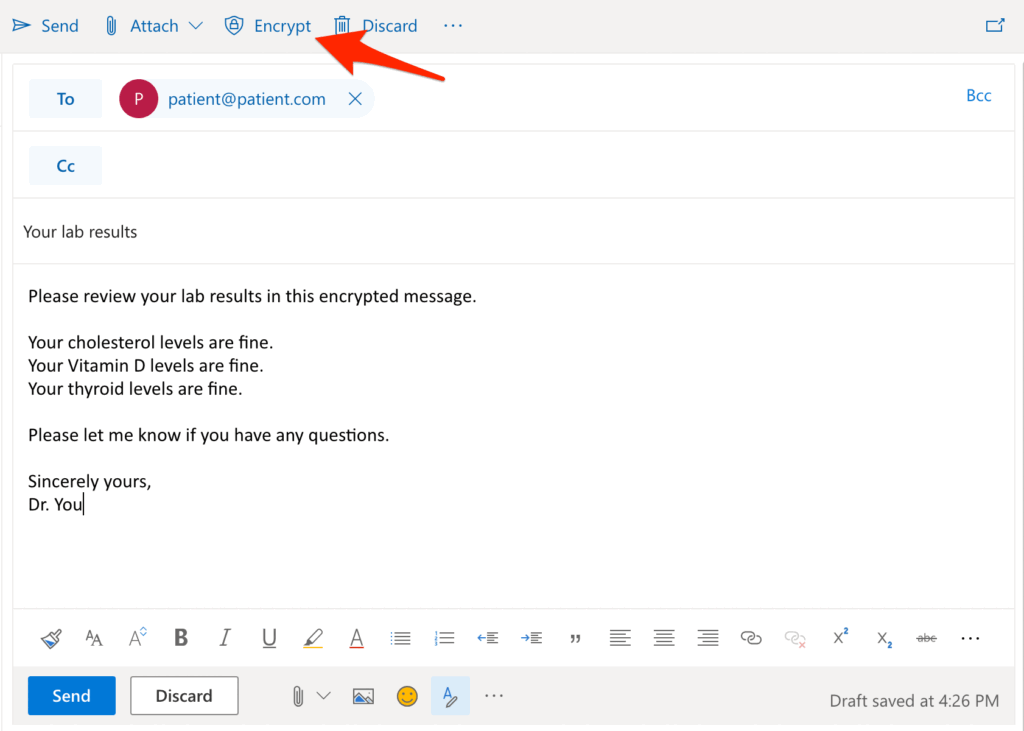
See that button that says "Encrypt"? Click that, and it's just that easy! After you click it, this little header will show up: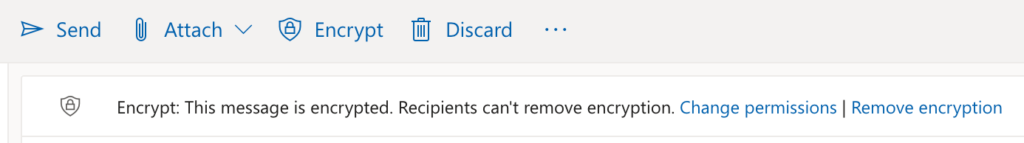
Sending a secure email on your side is pretty simple. But when it gets to your recipient, that's when it gets ugly.
Here's what shows up on the other side: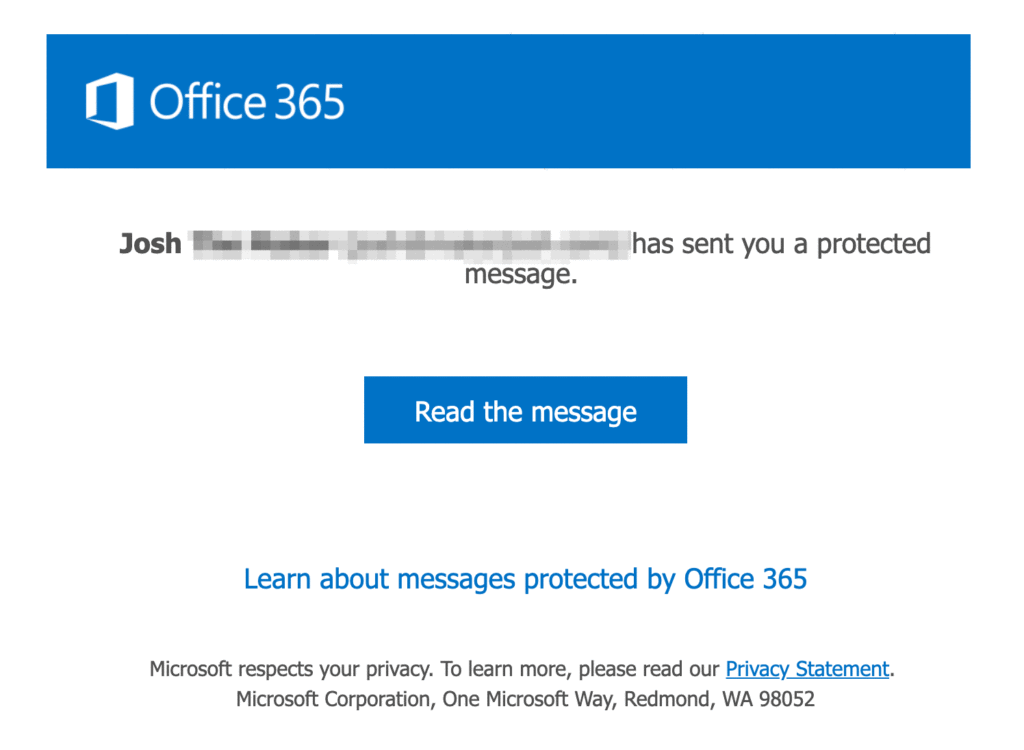
When you click on that, the patient or recipient sees this: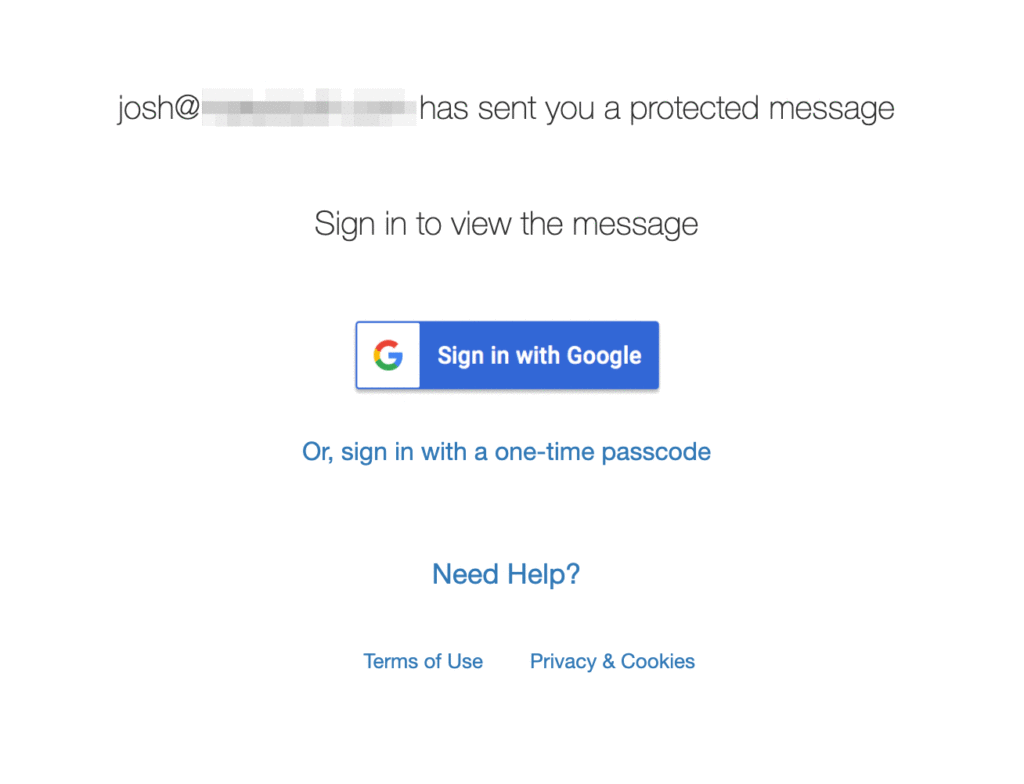
We've found that some older patients really struggle with this, and struggle to remember passwords.
You also need to remember (and train your staff) about how to tell when to send a secure email vs. a regular email. It's really easy to forget.
So while it CAN work (especially if you don't send a lot of secure messages), it's definitely not as easy to use as our favorite option below (#7).
SendSafely is another secure email service, though we wouldn't recommend it for HIPAA email encryption. It specializes in enterprise email encryption and secure file sharing. It can integrate directly with your Gmail or Microsoft 365 account.
Alternatively, you can send an email through their internal portal.
We’ll be blunt: we don’t recommend this option for healthcare providers or HIPAA-covered entities. While SendSafely mentions that they're HIPAA compliant on their website, they don't mention anything about being willing to sign a HIPAA business associate agreement.
Still, we’ll give you a tour of how it works ― in case you’re curious or if you’re looking for a solution for non-HIPAA reasons.
After you install and activate SendSafely, here's an example of what happens in the Gmail user interface: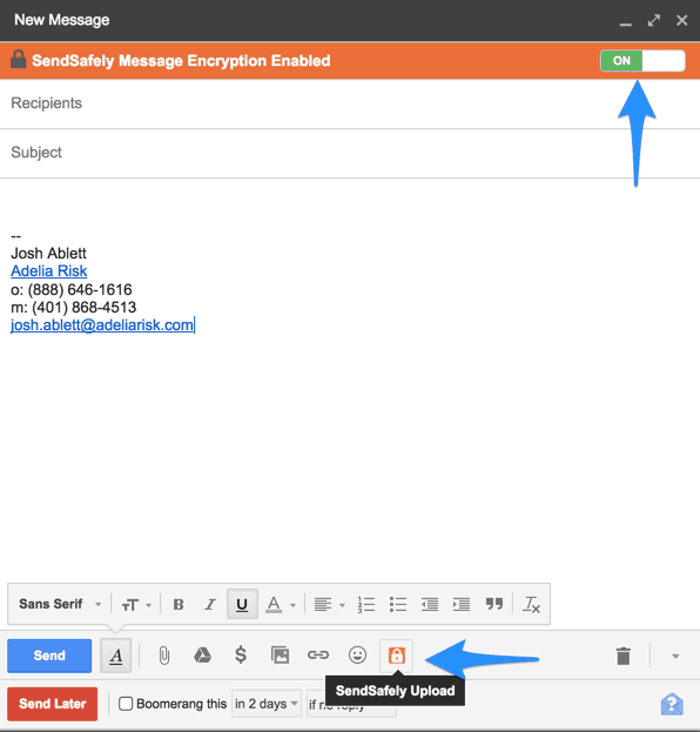
Instead of encrypting the whole email, SendSafely just encrypts the attachment: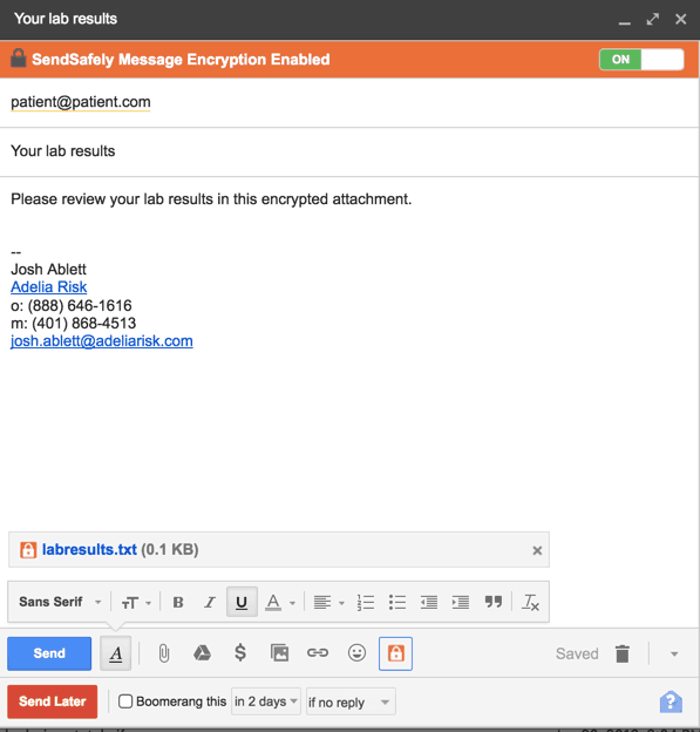
They do give you an interesting option to enable SMS verification. If you have your patient’s phone number, this could be useful. SMS verification is a great way to ensure the identity of the user.
Keep it in mind if you want to go the extra mile in your email security.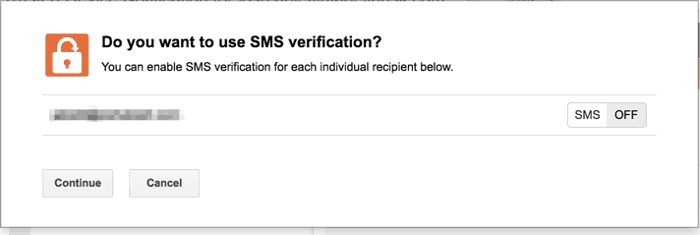
On the receiving side, here’s what it looks like: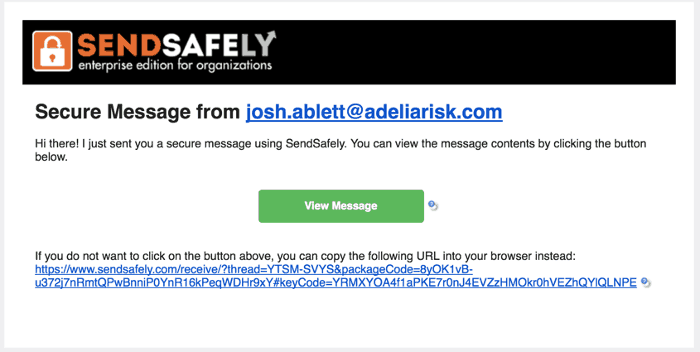
Simple, right?
As we said, we don’t recommend SendSafely for HIPAA-related purposes, because HIPAA just doesn’t seem to be a focus of theirs. There are better options for compliance-specific email.
But it’s a good one to keep in mind for comparison or for other future uses.
Paubox is an excellent service that will automatically encrypt all of your emails. It's, by far, the best option we've found for HIPAA email encryption. You’ll need a little help setting it up. But once it’s in place, it’s definitely the easiest for both you and your patients.
The best thing about Paubox is that you don't have to tell it which emails to encrypt. It automatically encrypts every email you send.
If your patient uses a modern email system like Gmail or Microsoft 365, they won't even have to click anything. The email will appear in their inbox just like any other.
Paubox uses a trick called TLS encryption to transparently encrypt every email. Actually, over 90% of the emails sent to or received from Gmail are actually encrypted already, according to Google. Paubox manages the rest.
If your patient is using an older email system or an email system that isn't set up the right way, however, they’ll either need to click a link or sign up for a username or password (your choice). But compared to the alternatives, this is still an extremely convenient option.
Bonus: it works with Google Mail or Microsoft 365, too. And mobile! Not to steal Apple's tagline, but it's our favorite because "it just works." Easy for the patient, easy for the doctor.
We also really liked this service while researching this article, and decided to make it part of the solution that we implement for practices that become our clients. We can help you implement Paubox with our Secure Cloud program.

Information around HIPAA email encryption has always been a bit murky. Lots of businesses aren’t sure whether they can safely email PHI.
As we’ve outlined above, the definitive answer is yes. It’s definitely possible to safely and securely send PHI via HIPAA email encryption.
But that’s only if you’re willing to put the time and money into finding a reliable method. Hopefully, this article has given you a clear overview of your options.
It may be a bit more complicated than sending a day-to-day personal email. And sure, it’s a bit more inconvenient. But with experimentation and research, lots of businesses have found encrypted email solutions that work wonderfully for them.
The easiest way to get HIPAA-compliant email with Paubox is through Adelia Risk's Secure Cloud for Healthcare Practices program.
Have questions or feedback? Please share them in the comments below.
Like this article? Share it!
PHI stands for “Protected Health Information”. PHI is anything that can identify an individual and provide information about their healthcare. Think of it this way, If you are emailing ANYTHING that someone can use to figure out medical information, it's PHI.
For healthcare providers and business associates, PHI is everything. Even in places that you wouldn't think to look, like notes on a calendar or files in a “Downloads” folder. This infographic does an awesome job demonstrating all of the different places where PHI can hide.
HIPAA Email Encryption ensures Protected Health Information (PHI) sent via email is secure and accessible only to intended recipients. It converts data into unreadable code during transit, meeting HIPAA rules by safeguarding sensitive medical data from unauthorized access or breaches.
To encrypt an email containing PHI: Get consent to send PHI, and use a HIPAA-compliant email encryption service like Proofpoint, Paubox, Virtru, Mimecast, Reflexion, or Microsoft 365. These services encrypt emails to ensure only the intended recipient can access the information, safeguarding sensitive data and meeting HIPAA requirements.
What our clients say

