What is SPF, DKIM, DMARC? Three important email authentication records that you should definitely know about. It’s unfortunately incredibly easy to send an email and make it look like it came from someone else.
Hackers do it all the time.
They can even make it look like someone from within your own company is emailing you.
The good news is that there are specific steps you and your IT person/firm can take to make sure hackers can’t ‘spoof’ your email address. This article will explore all three: SPF, DKIM, DMARC.
Spoofing
First of all, what is spoofing? “Spoofed” is when a hacker sends an email and pretends it comes from your company. Sometimes spoofing involves using a domain name very close to your company name (like office@yourcompary.com instead of office@yourcompany.com).
But many times spoofing means a hacker is using your actual domain name to send an email – so it’s really tough to tell that it’s not legitimate.
Email Authentication to the Rescue
So how can you keep a hacker from sending emails that appear to be from you/your company?
There are three technologies that prevent your email from being spoofed.
Basically all three of the technologies work the same way — they say “hey Internet, if you get an email from yourcompany.com and it DOESN’T come from these approved services, consider it spam and throw it in junk.”
The three technologies are SPF, DKIM, and DMARC. Let’s look at each one:
- SPF (Sender Policy Framework)
SPF is probably the most well-known of these email authentication records. This record basically determines which IP addresses are authorized for a particular domain.
For example, if your company uses Microsoft email services, your SPF record typically will show Microsoft IP addresses as authorized to send your emails. But, depending on your set up, you may see your secondary email provider (like Barracuda, Proofpoint, Mimecast, etc) or a set of IP addresses in the record instead.
Without setting an SPF record, your outbound messages will probably land in spam.
Let’s look at an example: ikea.com
We can look up their SPF record in MX Toolbox:
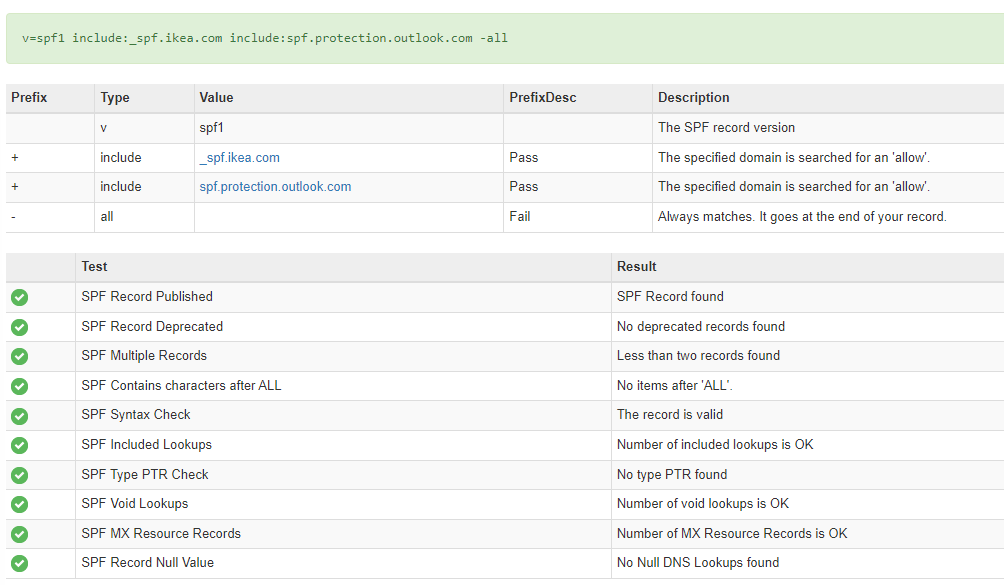
Everything is appearing valid (green) – and you can see that after ‘include’ it mentions the cloud systems allowed to send valid Ikea emails. So if someone tries to send an @ikea.com email from Google Workspace, the Internet would know this is not legitimate since it wouldn’t match the SPF record.
If your SPF record is showing errors or you don’t have one, the best place to start is by looking at your email provider’s help page.
- DKIM: Domain Keys Identified Mail
DKIM is similar to SPF in that it is a record added to your DNS to provide email authentication. But instead of checking IP addresses like SPF records, it checks the email header to make sure the message hasn’t been modified. DKIM adds a digital signature to your emails.
DKIM improves email deliverability and can protect your domain from malicious emails appearing to be sent from your domain.
Let’s look at our ikea.com example:
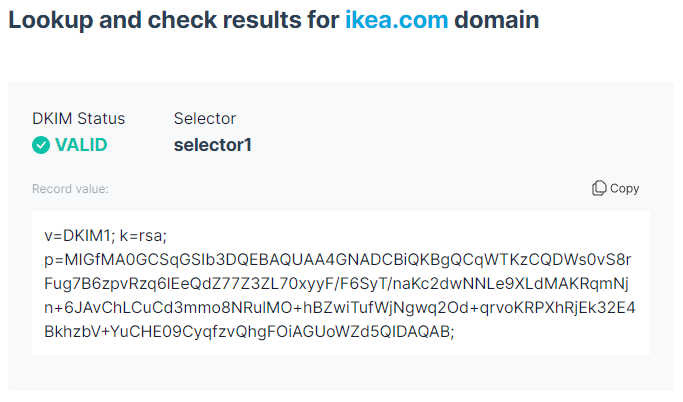
The DKIM signature is valid, and you can see how long and complicated the DKIM record is. Most email providers (like Google and Microsoft) do offer DKIM signatures, so be sure to look online for those instructions if you don’t have it set up.
- DMARC: Domain-based Message Authentication Reporting and Conformance
DMARC works a bit differently. DMARC tells recipient servers what to do if they get a message from you that doesn’t pass authentication checks (SPF and DKIM). Messages that aren’t authenticated could be spam or phishing attacks.
When you set up DMARC, you tell the Internet what to do with those unauthorized/unauthenticated messages: either monitor them, send them to a specific folder, or reject them.
Instead of trying to filter out all the bad, malicious emails, DMARC helps to only allow the good, legitimate emails.
And in our running example of ikea.com, we’re not surprised that they have a DMARC policy in place:
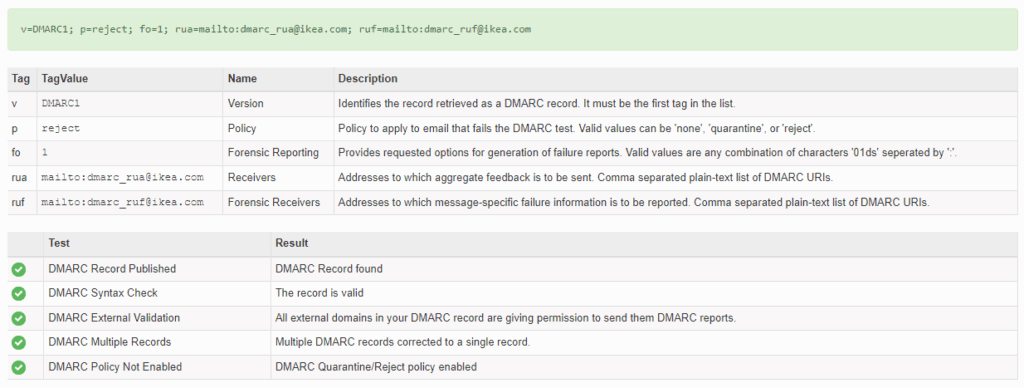
Ikea isn’t messing around, if their messages don’t pass SPF or DKIM, those messages are rejected.
How to check your SPF, DKIM, DMARC records?
You should be able to find all three of these records in your DNS records. If you’re not sure who your DNS provider is, you can search here: https://cloud.google.com/identity/docs/identify-host
There are a number of online tools you can use to check SPF, DKIM, DMARC as well.
You can use MX Toolbox to check all three, although this tool seems to be much better at finding accurate DKIM records.
Errors or uncertainty with SPF, DKIM, DMARC?
If you’re seeing errors with these records, or if you don’t have these records for your domain, we recommend reaching out to your IT firm to find out why.
Checking and fixing these records is something we do for our Virtual CISO clients. Protecting your email, ensuring deliverability, and safeguarding against spoofing are important pieces of any cybersecurity program.