Cyberattacks involving lookalike domains can be incredibly convincing and hard to detect. Let’s explore what a lookalike domain is, how they work, and what you should do about them.
A lookalike domain is a website domain with a name very similar to real, legitimate domain names. Lookalike domains are also called cousin domains.
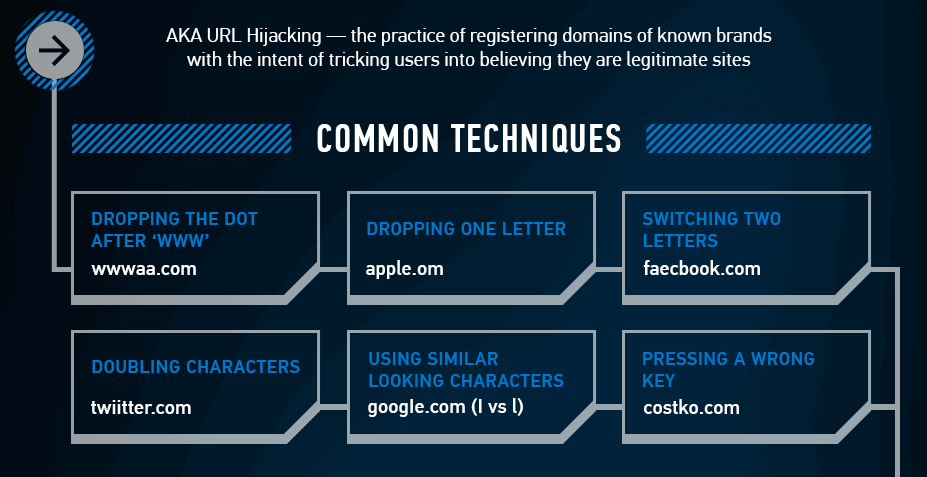
There are many tactics for creating a lookalike domain, including misspelling words (facebock.com instead of facebook.com) or using numerals in place of letters (goog1e.com instead of google.com).
Lookalike domains are used in phishing attacks to make the emails appear legitimate. This is why it’s very important to train your users on how to spot phishing emails. See the end of this article for some training tips.
Let’s look at some common domains and possible lookalike domains by adding letters, symbols, or additional words.
twitter.com – twiitter.com
google.com - goog|e.com
netflix.com - netfilx.com
amazon.com - amazonstore.com
microsoft.com - microsfot.com
It’s easy to look at this list and think you’ll be able to spot these domains – and that may be true. But please understand that these attacks do work, and can cause a lot of problems for you, your business, vendors, and clients.
Most of us have seen this text which has been circulated online for almost 20 years:
Aoccdrnig to a rscheearch at Cmabrigde Uinervtisy, it deosn't mttaer in waht oredr the ltteers in a wrod are, the olny iprmoetnt tihng is taht the frist and lsat ltteer be at the rghit pclae. The rset can be a toatl mses and you can sitll raed it wouthit porbelm. Tihs is bcuseae the huamn mnid deos not raed ervey lteter by istlef, but the wrod as a wlohe.
Obviously this is an extreme example since almost every word is misspelled - but this is why lookalike domains work. They use tricks like misspellings, switching numerals for letters and adding punctuation to trick your eye – and when you’re quickly reading an email you may not catch that it’s a lookalike domain. Scammers use slight variations from the original domain, so the chance of catching the mistake is pretty slim.
We’ve all been on the receiving end of easily-spotted phishing emails. Perhaps it’s an email from a well-established brand (like Amazon, Nintendo, or Netflix) but the sender is using a hotmail email address. Or there are tons of grammar and spelling mistakes. Sometimes phishing emails are easy to spot and block.
But lookalike domains are different. A phishing email using a lookalike domain will have a legitimate-looking sending email address (instead of a free hotmail, yahoo, or gmail address). The scammers will probably go through the trouble of setting up email security measures like SPF and DKIM authentication. This means the email may not get blocked by security systems and will therefore appear legitimate.
A phishing scam with this much complexity is not going to be sent to thousands of scraped email addresses. A phishing scam like this is typically a targeted attack called Business Email Compromise (BEC).
BEC attacks focus on social engineering to make their phishing emails more believable. They will scrape social media sites like Facebook or LinkedIn to gather information on their target.
Here’s how an example of BEC might work:
Let’s say your boss is on vacation.
You get an urgent email from a vendor asking for payment:
Hi Holly,
I know Janet is still on vacation, but she had promised that she’d pay my invoice by the end of the week. Can you please help? The invoice is attached.
Thank you,
Jim
The email appears to be coming from ABC Manufacturing, which is the name of your vendor. And Jim is your usual POC at that company. Everything seems to check out at first glance. What do you do?
Hackers know who you and your boss are thanks to LinkedIn, they know your boss is on vacation thanks to social media photos, and they know ABC is your vendor based on simple Google searches. Finding a lookalike domain was easy and now the hackers are counting on you to pay the invoice without delay.
Hopefully your company has processes in place when it comes to paying invoices, but this is the sort of scam you need to be aware of.
Our article about typosquatting (which involves lookalike domains) has some general tips to protect your business from cyberattacks in general:
If you are aware of lookalike domains, you should report the abuse directly with the domain registrar. How do you figure that out?
Check out this article from NameCheap: https://www.namecheap.com/blog/how-to-report-a-fraudulent-website-to-a-registrar/
It outlines how to find domain registrars and what information to include in your email and letters.
We recommend sending an email but, in parallel, send a mailed, registered letter from your attorney. It may require some aggressive management of GoDaddy (or whoever the domain registrar is) to get them to remove a domain that hasn’t yet been identified as doing something malicious.
Lookalike domains can make a phishing email seem legitimate. Learn about different cyberattacks so you can correctly identify and prevent them!
As part of our Virtual CISO service, we scan for lookalike domains and help you take action when needed. We specifically work with companies in highly-regulated industries like financial services, government contracting, and healthcare.
