We'd like to answer one of the most common questions that we get about HIPAA-compliant email.
One of the visitors to our site asked us...
This is a fantastic question about HIPAA-compliant email, and it's one that we hear a lot.
Here's how inbound emails work, and what you need to do.
Is Your email HIPAA Compliant and Secure? Don’t Wait for a Breach, Start your cloud security journey with our comprehensive audit.. Our specialists are committed to helping your business stay safe and seamlessly achieve HIPAA compliance and encryption requirements.

If you want to send PHI via email, the easiest thing to do is to sign up for a HIPAA-compliant secure email service.
In our article HIPAA Compliant Email: 7 Ways to Email PHI, we reviewed seven secure email services. The best one we found:
Here's a fact that most people don't know -- most of the emails you send are already secure and encrypted.
Don't believe us? Check this out -- Google has built a whole site about safer, encrypted email. They call it their Safer Email Transparency Report.
It's a pretty technical site, so here are the highlights.
The major email providers have all recently adopted "Transport Layer Security" for emails. Called "TLS" for short, this applies to all emails they send or receive.
TLS has been so successful that a full 90% of emails that Google receives are encrypted with TLS.
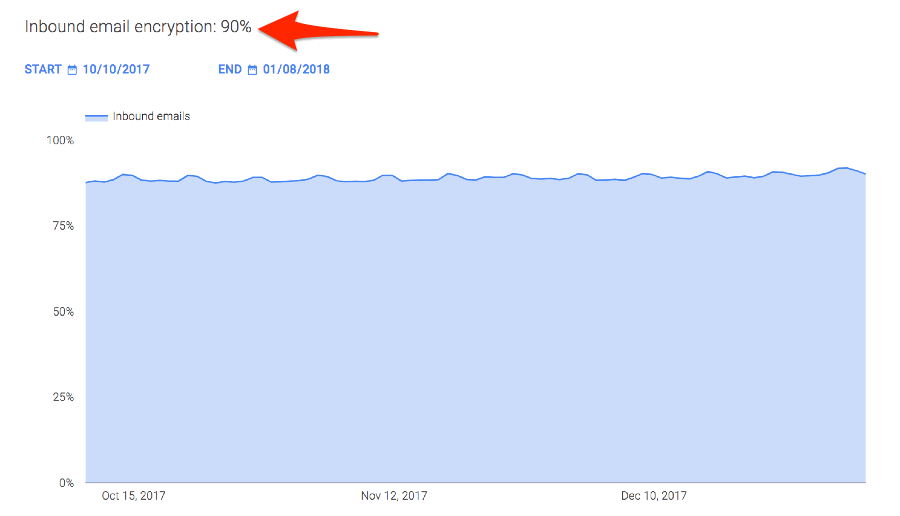
Google also "names and shames" domains that don't do a good job of managing TLS encryption:
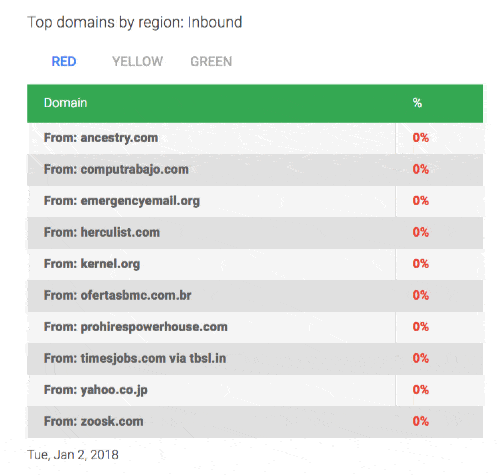
Here's the problem, though. How can you, as a medical provider, know that 10% of your emails are not sent securely?
The best HIPAA Compliant Email services are smart enough to recognize already-secure emails. There's no point in making a patient jump through hoops if the email is already being delivered securely.
When you email a patient, our favorite secure email service runs a check to see if TLS encryption is turned on.
If it is, the email just shows up in your patient's email inbox, just like every other email. And when they reply, the same encryption works the other way too. Both sides of the email (sending and replying) are encrypted with TLS. They're secure and HIPAA-compliant.
This is a MUCH better experience for your patients. Other secure email services are very inconvenient. Some force your patients to install an add-on. Others send a link for every email you send them. And others make them sign up with yet another username and password.
We've seen all of these cause problems for medical practices. Your staff has to spend valuable time on tech support for patients. And if you have older patients? Fugetaboutit!
Patients on older, insecure email servers, need to be handled a bit differently.
Our favorite secure email service manages this nicely. They've set it up so it's much more convenient for patients than other systems.
If your patient isn't on an email service that supports TLS encryption, the system is smart enough to detect it, and will send them an email like this...
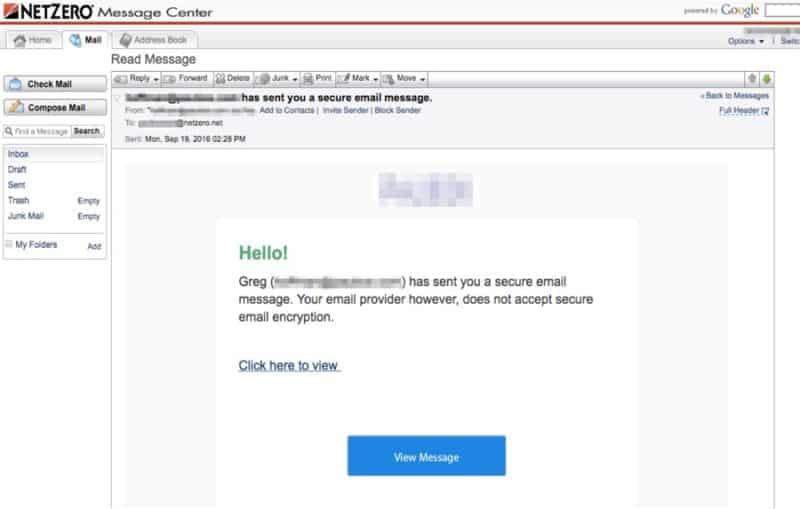
All they have to do is click on the link to view and reply to your email. All of it is secure because they'll be using a secure website (HTTPS).
Have you ever received a weird email from someone you know? Their computer was hacked and is now being used to send out phishing or virus-laden emails.
Sure, it's pretty unlikely that a patient will deliberately try to hack you. But it's VERY likely that you'll get an email from a patient that's actually a virus or phishing attack.
It's important to protect yourself against this. We typically recommend two levels of protection to our clients that will:
This is the big question. What should you do if a patient sends you an email with PHI in it, out of the blue? Are you liable or responsible if their email is breached? Is that a HIPAA-compliant email?
The Department of Health and Human Services (HHS) posted an article to answer this question called Does the HIPAA Privacy Rule permit healthcare providers to use e-mail to discuss health issues and treatment with their patients?
Here's the most important part of the article (we added the yellow emphasis):

Based on this guidance, you can assume that patients who email you are giving you consent to use email.
However, it also means that you should take steps to educate your patients on the dangers of insecure email. We cover a few ways to do this below.
Let's put this all together. Here's a clear list of what we recommend to most clients:
This is the easiest way to send and receive PHI with patients. We help practices to get set up with the best one recommended in this article.
This extra protection makes it less likely that you'll get tricked by phishing or viruses.
If you want to email patients, have them fill out a form giving explicit consent.
Here's an example of the form that we think does a really nice job of communicating the risks around email:
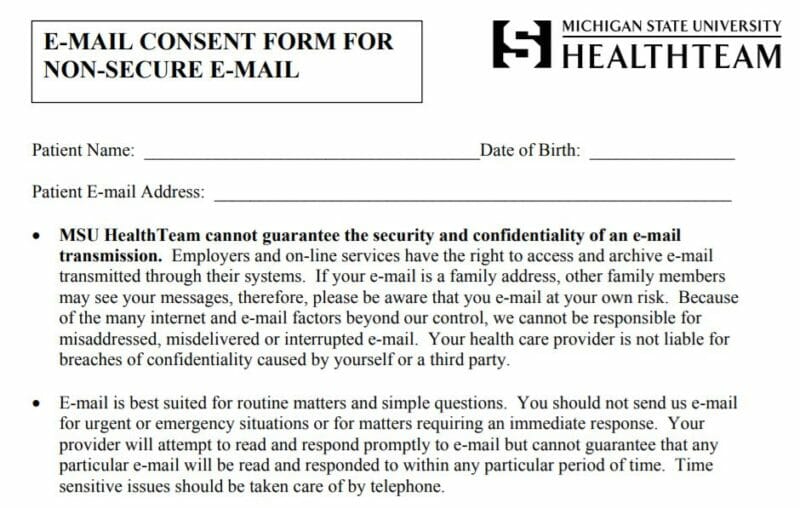
While you're at it, why not make this an online form? Using a service like IntakeQ, you can put this form on your website and have people fill it out online. It's HIPAA-compliant too.
We've seen practices use lots of different ways to remind patients about the risks of using email. These include:
Get some free help! Check out our free 42-Point Checklist for ways to make your practice HIPAA compliant.
Have questions or feedback? Please share them in the comments below.
Like this article? Share it!
