It’s true — hackers can get around some types of multi-factor authentication (MFA). And this is scary! MFA has long been touted as the best way to protect your accounts. And this is still true.
But.
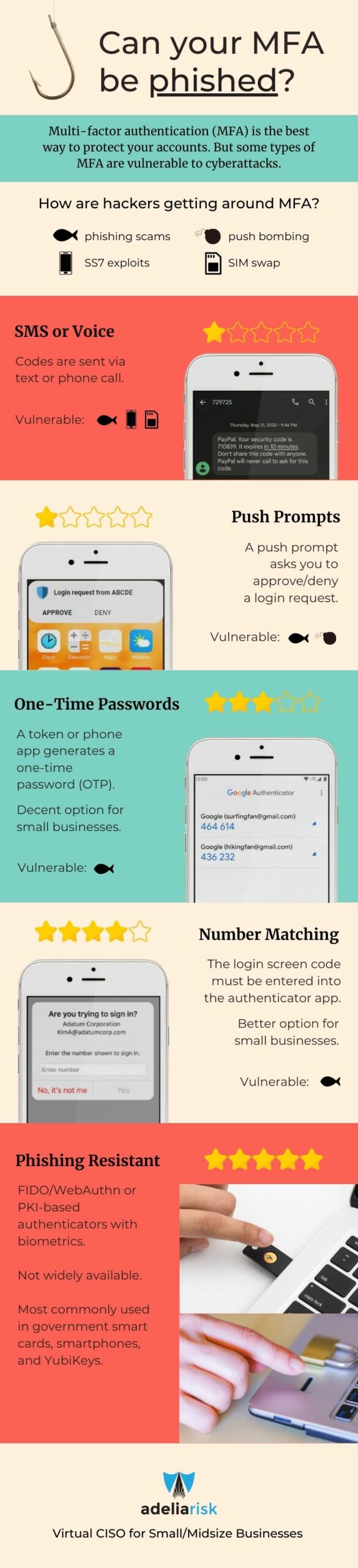
MFA is not bulletproof, and certain types of multi-factor authentication are more vulnerable than others.
The type of MFA used is so important, that the CISA recently released guidance about which types are the most secure. This guidance is helpful, and we’ve taken this information a step further. Below are screenshots of the different types of MFA. You may not have realized there are different types.
How are hackers getting around certain types of multi-factor authentication?
- Phishing – a hacker sends you an email with a link to a proxy website. You enter your username, password, and MFA code, thinking it is a legitimate login site. Now the hacker has access.
- Push bombing – a hacker repeatedly tries to log into your account, which triggers a push notification to your phone. You either approve by accident or annoyance!
- SS7 exploits – a hacker exploits SS7 protocol vulnerabilities to intercept the MFA code
- SIM swap – a hacker convinces a cell phone carrier to transfer control of a user’s phone number to the hacker’s device
These are all real situations that happen more frequently than you might imagine!
What should you takeaway from this information?
Hackers are constantly changing their tactics, and it’s important to stay ahead of them as much as possible. It’s important to use the strongest types of multi-factor authentication possible. For many, the best MFA is with app-based number matching or app-based/token-based with one-time passwords. If your email is currently protected by MFA SMS codes, we strongly recommend changing the type of MFA, or switching email programs altogether. It’s that important!
Infographic: Types of multi-factor authentication
We loved the guidance from CISA, but made it more user friendly with the infographic below. Seeing the pictures of MFA in action can help you recognize which forms you are using. If you’re using mostly SMS or Voice, it’s worth looking at stronger options.
For example, if you log into your Facebook settings, you can choose between SMS, Authentication App, or Security Key — the strongest option is the Security Key, followed by Authentication App and then SMS. Any MFA is better than no MFA, but be sure to check the options!
Share this image on your site and social media
You are welcome to share this image on your website using the embed code below:


