In Q2 2023, KnowBe4's report shows a scary statistic.
A worrying 50% of phishing attacks are HR-related.
Do you know why? Because they work. Cybercriminals are smart.
They try to trick your emotions, causing fear, confusion, panic, and sometimes even excitement.
This draws unsuspecting employees and business owners into their malicious traps.
Even scarier, one in three users is likely to click on a suspicious link (source: KnowBe4's 2023 Phishing Report).
And it’s these clicks that lead to breaches, stolen accounts, stolen data, and worse.
In this article, we'll delve into some of the most common HR phishing email examples.
These are real-life examples that your team may encounter.
We'll also offer steps to help protect your organization from data breaches, malware infections, reputational damage, and more.
Here are five common types of actual HR phishing emails and tests that we’ve seen.
These examples offer a glimpse into the mind of the hacker, and the tricks they use to fool your employees.
The focus here is on the W-2 form—a document critical for proving pay history for tax purposes.
The intent for this one is clear. The hackers are exploiting fear.
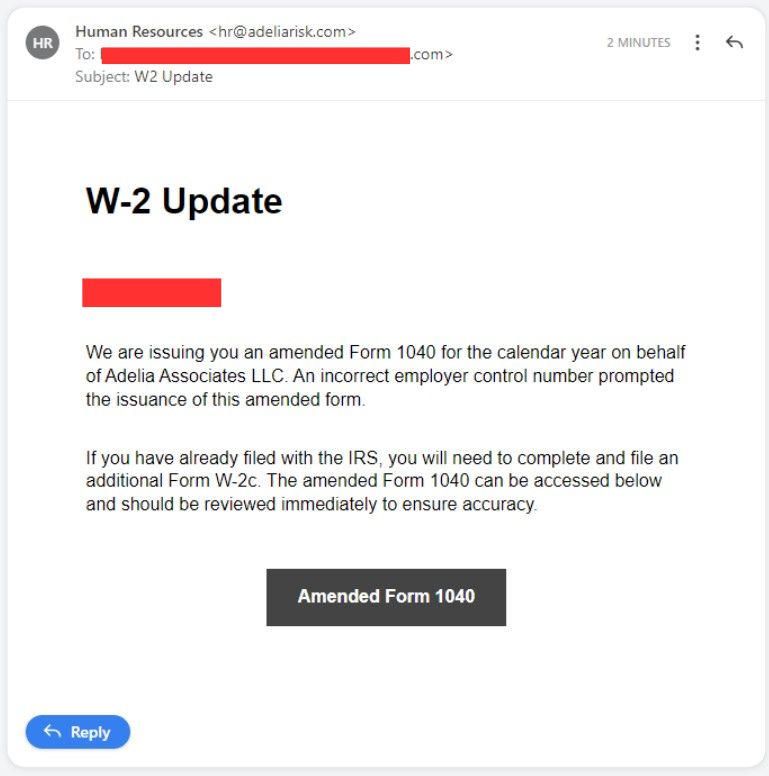
Fear of tax penalties, IRS audits, or just doing the wrong thing.
Especially in the calendar year, as it adds more urgency.
Employees who worry about their financial well-being and tax-related troubles are more vulnerable.
This raises the chances of clicking risky links or downloading files to "fix" these issues.
This strategy manipulates employees' emotions and the perceived urgency.
And a W-2 form is a clever guise for their malicious intent.
Business owners with employees who need to travel can feel anxious when they receive fake emails about travel.
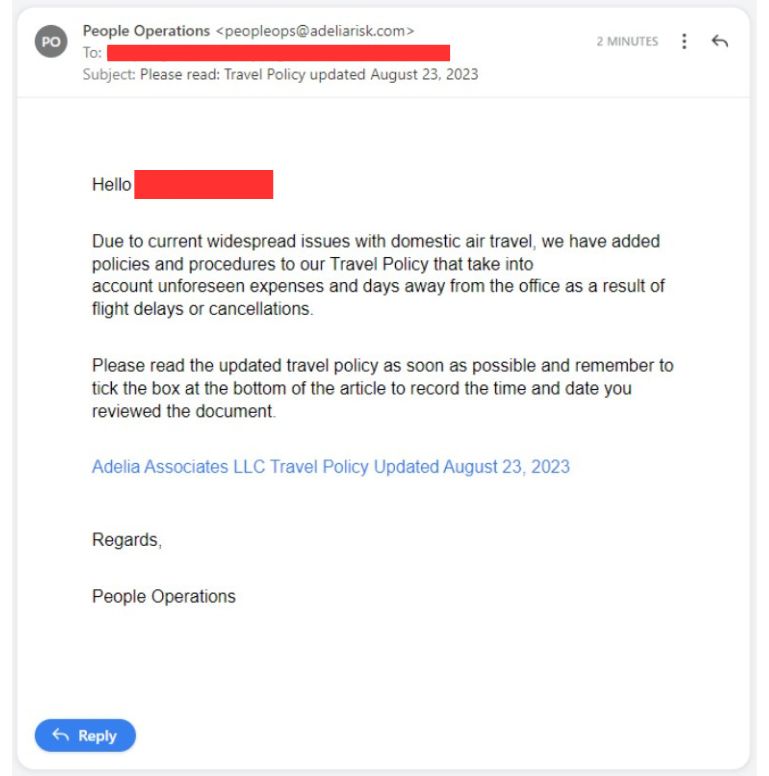
Sometimes, when companies introduce new travel rules, employees worry that they might not be following the right rules, and might have to pay for their own travel.
This crafty method also makes employees concerned about unexpected costs or having to take time off from work.
The goal of this smart strategy is to make employees curious and worried, so they become uneasy about missing out on essential information.
Hackers are really good at taking advantage of people's feelings about job insecurity.
They make you feel like you have to act fast because something bad might happen at work.
They play on your fears about not doing well at your job, missing out on opportunities, or even losing your job.
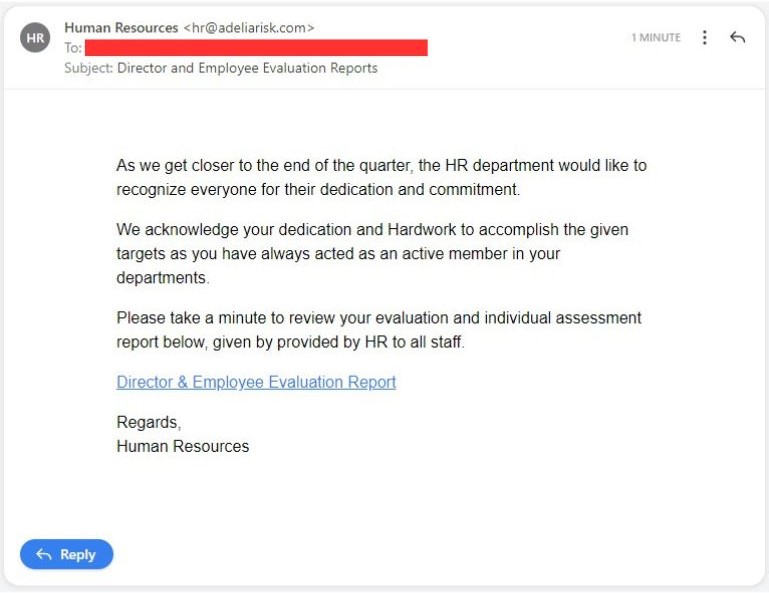
This is really effective for people who are trying hard to do their best at work.
For companies that focus a lot on goals and performance numbers, this kind of hacking can cause a lot of problems.
Even workers who really care about doing a good job can get tricked by fake emails that promise ways to do even better.
Basically, hackers use your job-related stress to trick you into making mistakes you'll regret later.
This is bad for security and also messes up the mood and workflow in the office.
This is especially true in workplaces where everyone is focused on hitting targets and goals.
This is an example of a sneaky HR phishing email that talks about changes happening in the company.
Bad actors take advantage of employees' curiosity and concerns about how these changes might affect their jobs.
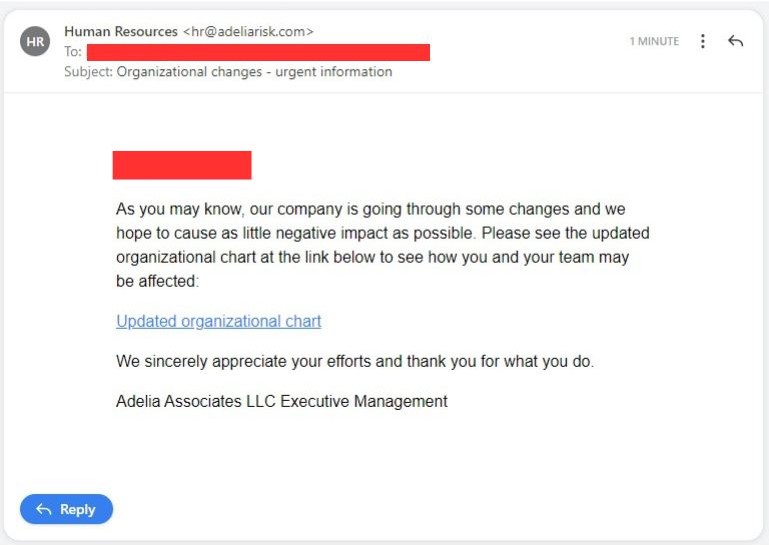
In the email, they pretend to be reassuring, saying the company wants to cut any negative effects.
But watch out for the tricky link in the email – it often looks like a real company website, but it's fake.
These fake website links are often called "Spoof Domains."
When the company is going through big changes, like getting new owners or managers, employees can get stressed.
This stress might make them more likely to click on the link, thinking it has information about what's happening.
But you need to be cautious!
Sometimes, behind those innocent-looking links, there might be bad intentions, like stealing your information or putting harmful software on your computer.
Phishing emails about paycheck issues and hackers pretending to be HR suggest problems with payments.
Alarmed employees receive encouragement to click a PDF link to fix the issue.
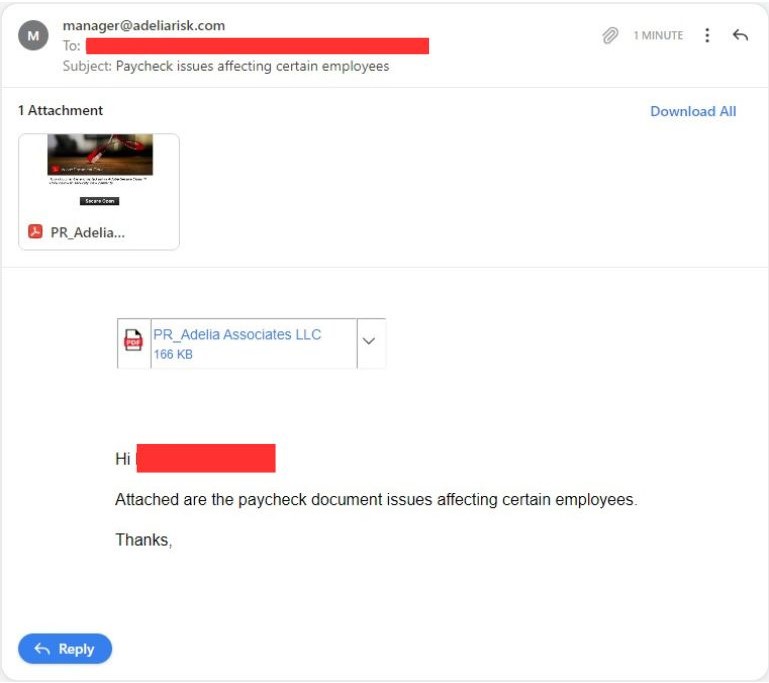
Yet, what appears to be a harmless PDF could contain harmful content.
This may cause data sharing or malware introduction in the company's network.
These emails harm trust and impact individuals and businesses.
Now that you're aware of common email tricks, let's prevent employees from falling for them.
Here are strategies that businesses can use to increase their defenses from threats.
This will protect sensitive data and help employees recognize phishing attempts.
Generic email addresses, like "[email protected]" make it easier for hackers to mimic staff. It’s trivial for a hacker to make it seem like an email comes from one of your actual email addresses.
Instead, consider implementing more specific email addresses, such as:
This simple step can reduce the risk of hackers pretending to be HR, making it a key preventive measure.
Making sure your employees are well-informed through regular security training is important.

This training should concentrate on all aspects of staying safe on the internet.
One important focus should be on "phishing awareness."
With our vCISO service, we provide these exercises.
Think of them as important tasks that teach employees how hackers try to trick them.
Employees will learn to spot phishing attempts in a safe and controlled setting.
This helps them become more aware and skilled at stopping online dangers.
It's important to have a way to report HR emails that seem suspicious. This is a crucial part of your defense plan.

Make sure to encourage employees to report these emails and give them clear instructions on how to do it. As part of our vCISO service, we offer an easy way to report them.
You can also think about using company-approved communication platforms to make reporting even simpler.
When employees can double-check HR emails, it helps them be cautious, which in turn makes the workplace safer.
Multi-factor authentication (MFA) is a must-have security step.
MFA adds extra protection by making sure employees confirm their identity when they access HR data.

Even if someone gets hold of login details, MFA stops them from getting in without permission.
It's a great way to safeguard important information and should be put in place without delay.
It's important to use SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) to check if emails are real.
These tools confirm that the sender is actually who they say they are, which makes it hard for hackers to fake HR messages.
This makes it easier for employees to tell if an email is legit and also stops phishing attempts from causing problems.
It's important to have security rules that can change to keep up with the ever-changing threat landscape.

When you update the security rules for HR, it helps them stay good at stopping new types of attacks.
Working together with both HR and IT teams makes sure your security rules stay strong and always stay current.
Think about using email systems that have advanced technology and machine learning.
These systems can spot strange or weird HR-related email patterns and tell you about them.
Using tech to find these emails helps companies deal with phishing dangers.
Doing so will lower the chances of attacks and keep HR information safe.
If possible, make sure your notifications that actually come from HR look the same.
That way, a hacker who is posing as your HR team likely won’t match the branding. This gives your employees a visual cue that something is unusual.
In short, HR phishing emails expose the ongoing threat to businesses.
Especially for employees in the workplace.
These cybercriminals like to play with people's feelings.
This leads to creating distress, confusion, panic, or excitement to trap their victims.
One in three users fall to such scams, so it's vital to fortify defenses to keep your business safe and running.
