We’re a CMMC compliance consultant that handles the heavy lifting.
We build your security program, manage your tools, and get you assessment-ready.
We’ve helped defense contractors go from zero to certification-ready
without losing their minds (or their contracts).
We implement NIST 800-171, run your security tools day-to-day, and prepare you for your C3PAO assessment. Think of us as your outsourced CMMC cybersecurity team, handling DFARS compliance, continuous monitoring, and everything in between so you can focus on winning contracts.
We hired Adelia Risk as our CMMC compliance consultant, and they delivered exactly what we needed — clear guidance, real expertise, and zero fluff.
They identified gaps, prioritized remediation, and built the documentation we actually needed (SSP, POA&M, policies, evidence collection) while keeping things practical for a real business environment.
Communication was fast, timelines were met, and every recommendation came with a clear “why” in plain English. They didn’t hand us a checklist and vanish. They stayed engaged and made sure we understood what to do next. Highly recommend.
Steven R., CMMC Client
Military Manufacturer from Michigan
We engaged Adelia Risk as our CMMC compliance consultant early in our journey, and they were incredibly patient as we went through the “discovery learning” phase.
Despite some self-induced setbacks on our end, they’ve always been available, prompt, and willing to go out of their way to help us reach compliance.
They’re more than a vendor — they’re an extension of our team. When answers aren’t immediately available, they research it and follow up with clear direction. That commitment to getting it right is what sets this CMMC compliance service apart.
Scott F., CMMC Client
Defense Contractor from Montana
You manufacture parts or provide services to the DoD, not CMMC cybersecurity.
But CMMC is getting harder to fake.
They keep your network running. But when C3PAOs ask about your cryptographic key management and FIPS 140-2 validation, they’ll point to you. When you need to prove all 110 controls are implemented, “we use Microsoft 365 GCC” isn’t enough.
Self-assessments are gone.
C3PAOs will actually test your controls. They’ll ask your employees
about incident response. They’ll
check logs. They’ll verify
encryption. Hope isn’t a strategy.
DoD contractors can’t bid without CMMC. By the time the RFP drops, you need certification in hand. Not “in progress.” Not “planned.” Complete.
China targets defense contractors specifically for CUI. You’re not flying under the radar – you’re on the target list.
Which is exactly why you’re a target.
Nation-state actors have unlimited budgets and patience. They’ll spend months in your network because defense IP is worth billions.
Why hack Lockheed when they can hack you?
You have the same CUI with a fraction of the security budget.
One breach can compromise an entire weapons program.
NSA officials report that small defense
contractors “are truly a target of nation-state
activity”
Small defense contractors need to improve CMMC cybersecurity protocols.
You’re not too small to be targeted.
You’re the soft underbelly of the defense industrial base.
We help you shore up your defenses, both to be CMMC-compliant and to reduce the risk of a devastating cyberattack.
We don’t write an SSP then disappear. We’re not a one-person shop. We provide CMMC compliance services managed by true professionals – implementing your NIST 800-171 controls, managing your security tools, and when your C3PAO shows up, we’re sitting next to you answering their questions.

You may not need a $100K security program on day one. Start down the path with some monitoring and basic controls. Add active management when you’re ready. Scale to full CMMC preparation when that contract is on the horizon. Your security partner should match your growth, not drain your R&D budget.
Most CMMC consultants hand you a 400-page SSP and a list of things for your IT team to figure out. We log into your systems and give you specifics. Your SSP matches reality because we wrote what we actually built.

We translate between NIST-speak and IT-speak. We tell your IT provider exactly what to configure: “Enable conditional access, require FIPS 140-2 validated encryption, set these specific audit log retention policies.” No more confusion. No more finger-pointing.
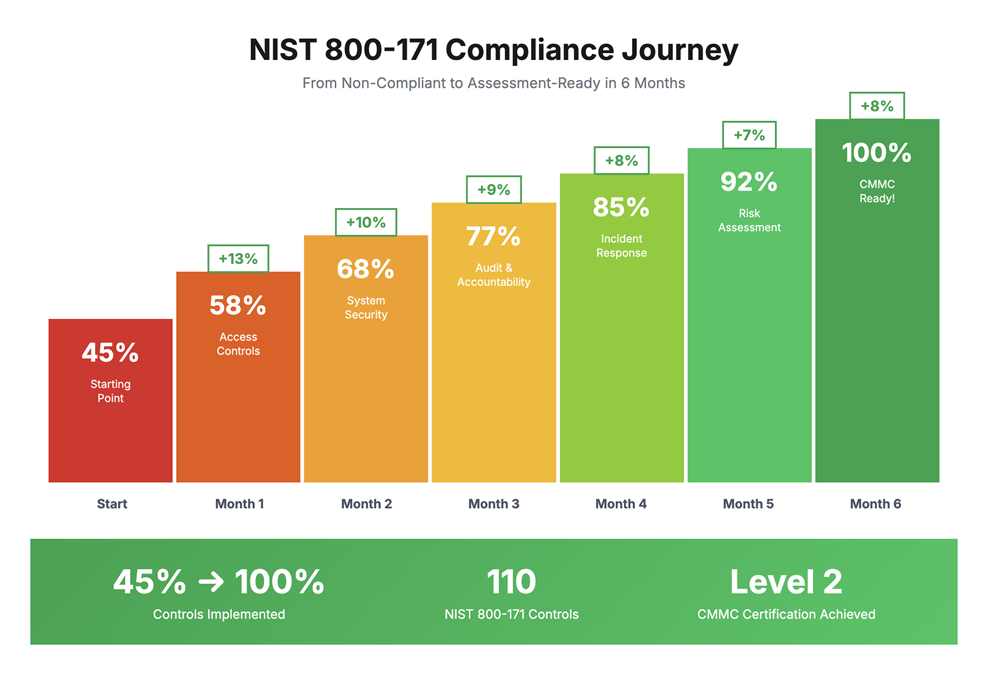
This contractor started with only 45% of NIST 800-171 controls implemented – nowhere near ready for CMMC Level 2.
Month by month, we implemented controls, configured security tools, and built their SSP.
By month 6: All 110 controls fully implemented or documented with approved POA&Ms (Plan of Action & Milestones).
Result: Passed their CMMC Level 2 assessment.
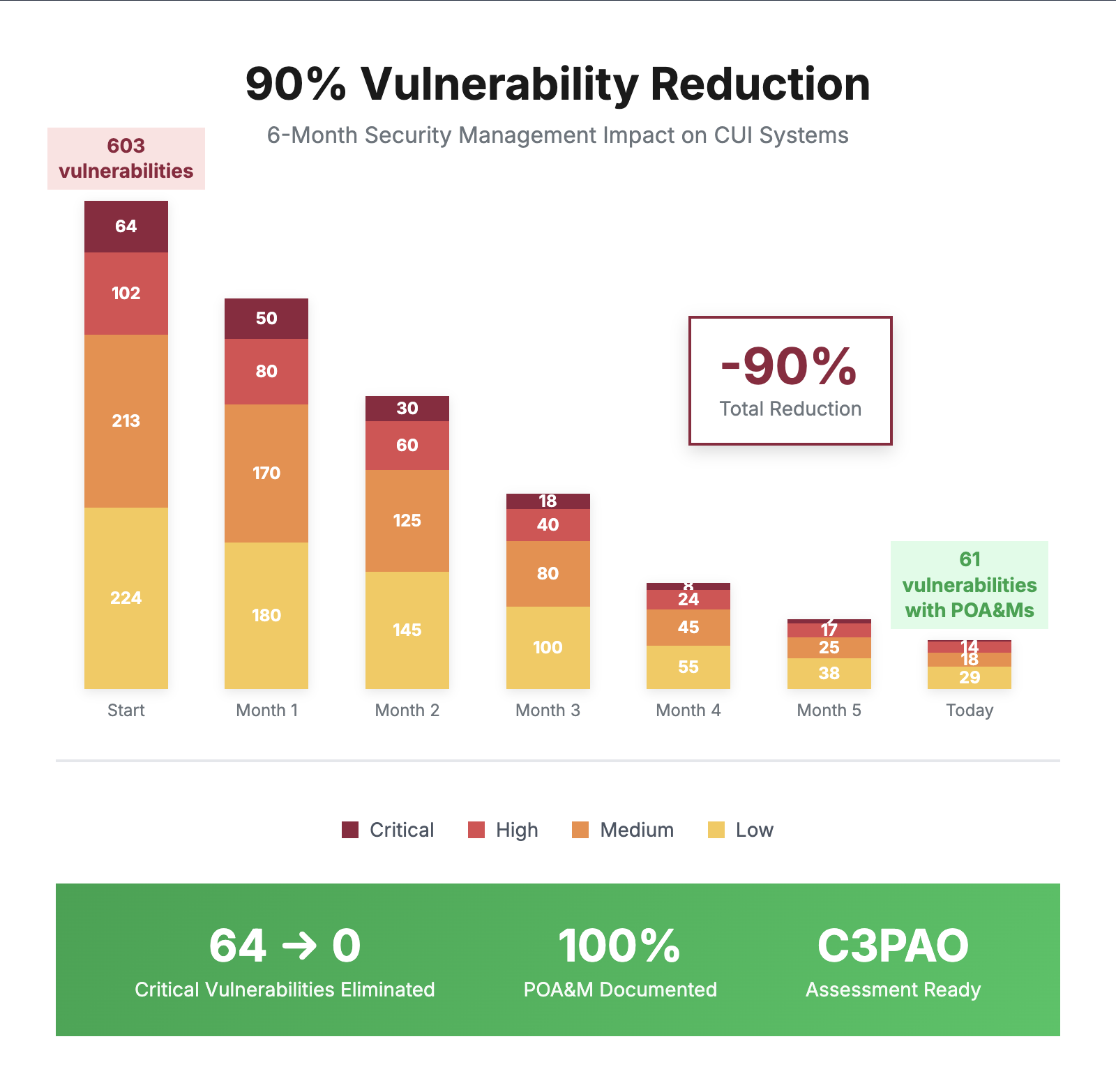
This manufacturer had 603 vulnerabilities across their network and systems handling CUI – including 64 critical ones that nation-state actors actively exploit.
Six months later: 90% eliminated. Just 2 critical vulnerabilities remain (both with documented Plan of Action & Milestones for their assessment).
This is what happens when CMMC consultant actually manages your security tools instead of just installing them.
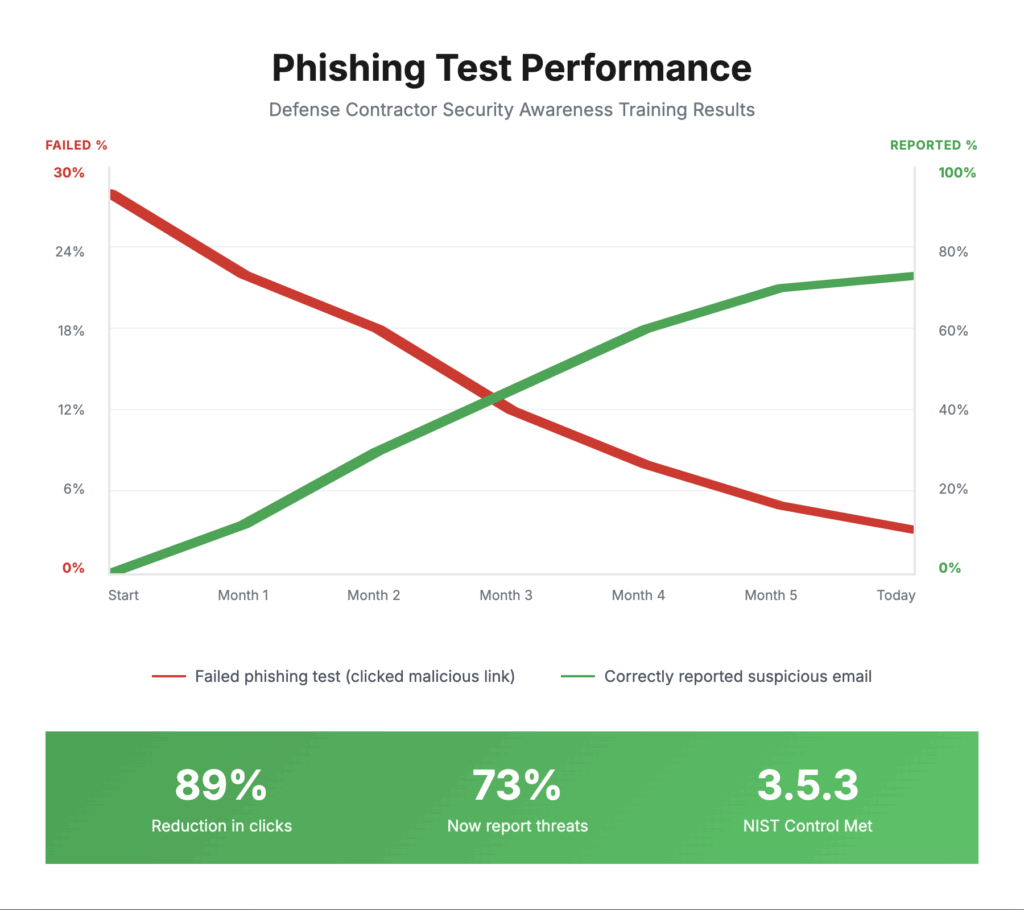
Prices range from a few hundred dollars a month for small clients to thousands a month.
Let’s book a consultation to see if we can help you.
The answer varies widely from business to business. We wrote a whole guide that can help you calculate these numbers for your own company:
CMMC Compliance Costs: A Comprehensive Breakdown For Businesses
Your IT provider keeps your systems running—that’s IT operations. But CMMC requires specialized expertise that most IT providers don’t have (and shouldn’t be expected to have). Here’s how we work together:
Your IT Provider Excels At:
Where Our CMMC Consultants Add Value:
An Example of How We Work Together:
Most IT providers actually love working with us because we make their job easier. We provide clear, technical guidance instead of vague CMMC requirements. They handle the implementation, we handle the compliance expertise.
DFARS 252.204-7012 flows down to every company touching CUI. Every single one.
The prime won’t protect you. When there’s a breach traced to your systems, they’ll find another supplier tomorrow. DoD holds them responsible, so they hold you responsible.
Plus, more primes are requiring CMMC certification from all subs before contract award. No cert = no subcontract, regardless of your relationship or past performance.
“How long until we can get certified?”
Honest timeline for small contractors who are really engaged and motivated to get over the CMMC line:
Can you go faster? Maybe, if you dedicate internal resources.
Can you go slower? Sure, but every month delays your ability to bid.
The key: Start before you need it. By the time that RFP requires CMMC, it’s too late.
Short answer: NIST 800-171 is what you implement. CMMC is how you prove it.
NIST 800-171 = The 110 security controls you must have in place to protect CUI. It’s been required by DFARS since 2017, but enforcement was basically self-attestation.
CMMC = The assessment framework that verifies you actually implemented those controls. No more self-scoring. A third-party assessor (C3PAO) will test your controls, interview your staff, and review evidence.
Think of it this way:
Most CMMC contractors claiming NIST 800-171 compliance today would fail a CMMC assessment. The controls are the same – but now someone’s actually checking.
CMMC Compliance Services for Defense Contractors Nationwide
Adelia Risk provides virtual CMMC compliance services to defense contractors anywhere in the United States. Whether you’re a machine shop in Michigan or a software developer in San Diego, NIST 800-171 requirements are the same. Our remote implementation model means you get expert CMMC support without flying in consultants or hiring local specialists who may not even exist in your area.
We work with defense contractors across all tiers – from small machine shops making single components to technology firms developing defense software. Distance doesn’t matter when we’re logging into your cloud systems and managing your security tools remotely.
It really depends on where you’re starting. If you’ve got a decent security foundation, we’re typically looking at 6-12 months to get assessment-ready. If you’re starting from scratch (no policies, no tools, no dedicated IT security), plan for 18 months and up.
The biggest factor isn’t the technical stuff, though. It’s how fast your leadership can make decisions and how willing your team is to adopt new processes. We’ve seen companies blow through this in six months because the CEO was all-in and they made it happen. We’ve also seen it drag on for two+ years because nobody wanted to change how they worked.
Short answer: check your contracts.
Longer answer:
If you only handle Federal Contract Information (FCI), which is mostly contract information, you can shoot for Level 1. This is a simple self-assessment covering 17 practices.
If you handle Controlled Unclassified Information (CUI) and/or ITAR data, you’re likely Level 2. This is where most defense contractors land. 110 practices, and most contracts will require a third-party assessment.
If you’re a Prime contractor working on really sensitive work, you may need to go for Level 3. Government-led assessment, additional controls from NIST 800-172.
TL;DR: If your contract mentions DFARS 252.204-7012, you’re almost certainly looking at Level 2. When in doubt, ask your contracting officer.
You don’t get a binary pass/fail on the spot. If the assessor finds gaps, you’ll get a report detailing what needs to be fixed. For minor issues, you may get a chance to remediate and close them out within a defined window (typically 180 days).
For significant gaps, you won’t get certified until they’re resolved—which means you can’t bid on (or keep) contracts that require that certification level.
That’s the real risk: losing contract eligibility while your certified competitors scoop up the work.
The fix? Don’t go into your assessment hoping for the best. Do a real readiness assessment first, find the gaps yourself, and close them before the C3PAO shows up.
You absolutely can do it yourself. Whether you should is a different question.
If you’ve got someone in-house who genuinely understands NIST 800-171, has time to dedicate to the project, and your leadership will actually give them authority to make changes, then go for it.
But here’s what we see in practice: most small-to-mid defense contractors don’t have that person. They’ve got an IT guy or an IT company who are already stretched thin, and CMMC becomes one more thing on the pile. Six months later, nothing’s moved.
A good CMMC consultant will accelerate the timeline, help you avoid expensive mistakes, and keep the project from stalling. We’re not here to sell you stuff you don’t need—but if your team is already maxed out, trying to DIY this usually costs more in the long run.
Ongoing. The certification is valid for three years, but you can’t just check the box and forget about it.
You’re expected to maintain continuous compliance, which means keeping your controls in place, documenting changes, and doing annual self-assessments. If you let things slide, you’ll be scrambling again when recertification comes around (or worse, if there’s an incident and someone asks for proof of compliance).
This is why we offer a managed CMMC compliance service, not just consulting. The companies that treat security as “set it and forget it” are the ones who end up losing contracts and getting in trouble under the False Claims Act.
A C3PAO (that’s the third-party assessment organization) will review your documentation, interview your team, and test your controls to make sure everything actually works the way you say it does.
Over the course of a few weeks, expect them to:
It’s not a “gotcha” exercise—they want you to pass. But they will dig into areas that look weak on paper.
Adelia Risk provides virtual CMMC compliance services to defense contractors anywhere in the United States. Whether you’re a machine shop in Michigan or a software developer in San Diego, NIST 800-171 requirements are the same. Our remote implementation model means you get expert CMMC support without flying in consultants or hiring local specialists who may not even exist in your area.
We work with defense contractors across all tiers – from small machine shops making single components to technology firms developing defense software. Distance doesn’t matter when we’re logging into your cloud systems and managing your security tools remotely.
Stop worrying about whether you’ll pass. Let us handle it.