Achieving Cybersecurity Maturity Model Certification (CMMC) compliance and adhering to NIST 800-171 standards are increasingly essential for businesses dealing with Controlled Unclassified Information (CUI). However, knowing the CMMC compliance costs often presents challenges, particularly when it comes to understanding and managing the CMMC-associated costs.
For many organizations, these long and complex compliance projects raise critical questions about feasibility and return on investment. Should you proceed with CMMC compliance, and if so, how do you navigate the financial implications effectively?
This article explores the key cost considerations of CMMC compliance, offering insights to help businesses make informed decisions and strategically plan for certification success.
What our clients say
We hired Adelia Risk as our CMMC compliance consultant, and they delivered exactly what we needed — clear guidance, real expertise, and zero fluff.
They identified gaps, prioritized remediation, and built the documentation we actually needed (SSP, POA&M, policies, evidence collection) while keeping things practical for a real business environment.
Communication was fast, timelines were met, and every recommendation came with a clear “why” in plain English. They didn’t hand us a checklist and vanish. They stayed engaged and made sure we understood what to do next. Highly recommend.
Steven R., CMMC Client
Military Manufacturer from Michigan
We engaged Adelia Risk as our CMMC compliance consultant early in our journey, and they were incredibly patient as we went through the “discovery learning” phase.
Despite some self-induced setbacks on our end, they’ve always been available, prompt, and willing to go out of their way to help us reach compliance.
They’re more than a vendor — they’re an extension of our team. When answers aren’t immediately available, they research it and follow up with clear direction. That commitment to getting it right is what sets this CMMC compliance service apart.
Scott F., CMMC Client
Defense Contractor from Montana
Let’s Start With Audits
The path to CMMC compliance involves a mix of self-driven tasks and potential outsourcing.
One of the critical steps is undergoing audits, an integral part of achieving CMMC compliance.
While final regulations are still on the horizon and only a few audits have taken place, companies that have already undertaken audits typically find themselves investing between $15,000 to $50,000.

Remember that this cost can fluctuate based on the size and complexity of your organization.
For comparison, similar audits in other sectors, such as SOC2 or HIPAA carry similar price tags.
Expert Help & Documentation
Another area that directly contributes to your CMMC compliance cost is obtaining expert help.
Although you’re not required to involve third parties to pass a CMMC audit, many companies choose to do so because of the project’s complex nature.
The most common forms of expert help fall into two categories: web-based templates and consulting.
Web-based templates are a great resource for streamlining the process, but only if you have the in-house expertise to make sense of the templates.
These online systems, like Exostar and others, provide templates and a guide for filling them out.

Depending on the size and complexity of your organization, these services can cost from $1,000 to $20,000.
Again, it’s worth noting that companies lacking a strong technical team may find it challenging to utilize these systems effectively.
Consulting
Consulting help is another common avenue pursued by organizations.
Registered Practitioners, or specialized consultants, provide their expertise for CMMC compliance.
The price for these services can vary greatly based on the level of assistance required and how extensively you wish to engage them.
Many consulting firms start with a “pre-assessment” or “gap assessment” engagement, which typically costs between $10,000 and $20,000.

Remember that this cost only covers the initial report and doesn’t include the expenses for implementing the recommended changes to reach compliance.
However, this cost is a necessary step to determine how big of a project you face to reach CMMC and NIST 800-171 compliance.
System Changes
Most of the expense of CMMC projects is changes to your technology.
There are many tech upgrades you’ll need to align your organization with CMMC standards.
System changes usually follow two strategic approaches: Full and Enclave.

The Full approach is similar to overhauling your entire operations to attain CMMC compliance.
This makes the most sense for companies that handle CUI in all areas of their business.
The Enclave approach is like creating a secure corner within your operations, isolating Controlled Unclassified Information (CUI) to a specific set of computers.
While the Enclave approach is typically cheaper, it might not be a practical solution for all businesses.
Much care must be taken to control CUI going into and leaving the enclave, and to redact CUI.
Let’s take a look at the costs of these two methods across the most common systems.
This comparison will help you figure out which approach fits your business best.
1.) Email Security
Email security is a key component in achieving CMMC compliance, as most companies have CUI in their emails.
With the Full approach, Microsoft 365 GCC or GCC High is the go-to solution.
However, be prepared for a cost increase—expect to pay 20-100% more per license, depending on your chosen plan.
You’ll also need to pay for email migration, which typically costs thousands of dollars.
If you’re considering the Enclave approach, opting for less expensive secure email services such as Preveil can be a cost-effective alternative.
This would cost around $20-30/user/month, in addition to what you’re already paying for email.

A notable advantage of this route is that no migration is needed, saving you from potential additional expenses.
2.) Secure Document Sharing
The next step is figuring out secure document sharing.
If you’re taking the Full route, your entire company becomes compliant, and tools like OneDrive and SharePoint from Microsoft 365 GCC packages can be your allies.
One challenge, though, is that the Microsoft 365 GCC plans don’t offer external sharing.
Need to share with external parties?
Consider services like Preveil or Cocoon Data.
For those choosing the Enclave route, making a smaller part of the company compliant, similar options like Preveil and Cocoon Data, costing around $15 per user per month, are available.
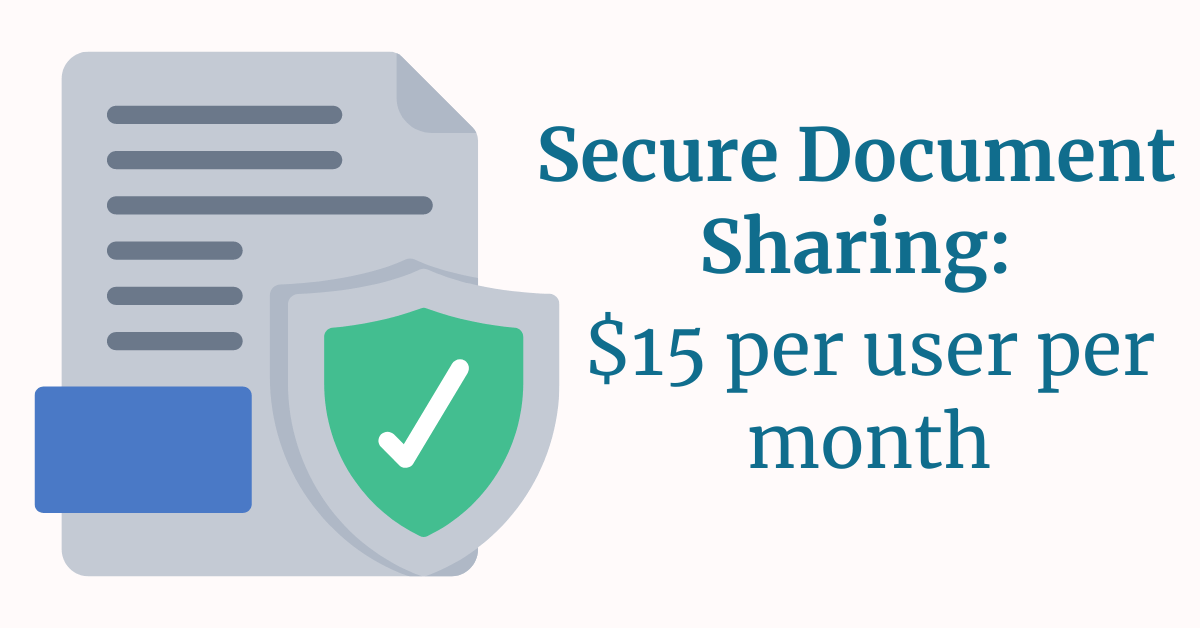
Regardless of your approach, the right tools can simplify secure document sharing, essential for keeping your data safe and helping you become certified.
3.) ERP and/or CRM Systems
This is a particular area of challenge with CMMC compliance.
Many ERP and CRM systems aren’t compatible, and the vendors are still trying to figure out their plans.
Often, you may need to upgrade or switch to a compliant version, with costs varying greatly depending on your unique requirements.
If you’re using the Enclave approach, consider concealing or eliminating CUI from your ERP or CRM system so it remains in the enclave.
This can be a solid approach if upgrading your ERP and CRM systems seems costly or complex.
4.) Firewall & Network
Firewalls and network gear are crucial parts of CMMC compliance.

They need to be up-to-date with all security features and follow strict rules about how data moves in and out of your system, as well as how remote connections are handled.
To meet CMMC standards, these systems must use encryption algorithms that are FIPS 140-2 validated.
You can check if your network equipment uses this by looking it up on a specific website.
However, getting your firewall and network gear to meet these standards can be costly.
The price often starts in the thousands of dollars.
On top of that, you’ll also have to pay your IT company to make these upgrades and changes.
While the costs might seem high, remember it’s an investment in the security of your business and a step towards certification.
5.) Computer Security
Now, let’s talk about Computer Security.
This involves protecting all the computers that can reach your special info, also known as CUI.
For this, you’ll need to find a service that can spot and respond to security threats.
Some popular ones are SentinelOne and CrowdStrike.
On top of that, you’ll also need an antivirus service to keep your computers safe from viruses and malware.
Your IT provider can suggest a good one for you.
Be ready to spend around $10 to $20 per computer each month for these services.

Remember, this is to keep your computers and the CUI they can access safe, so it’s a cost worth considering in your CMMC compliance journey.
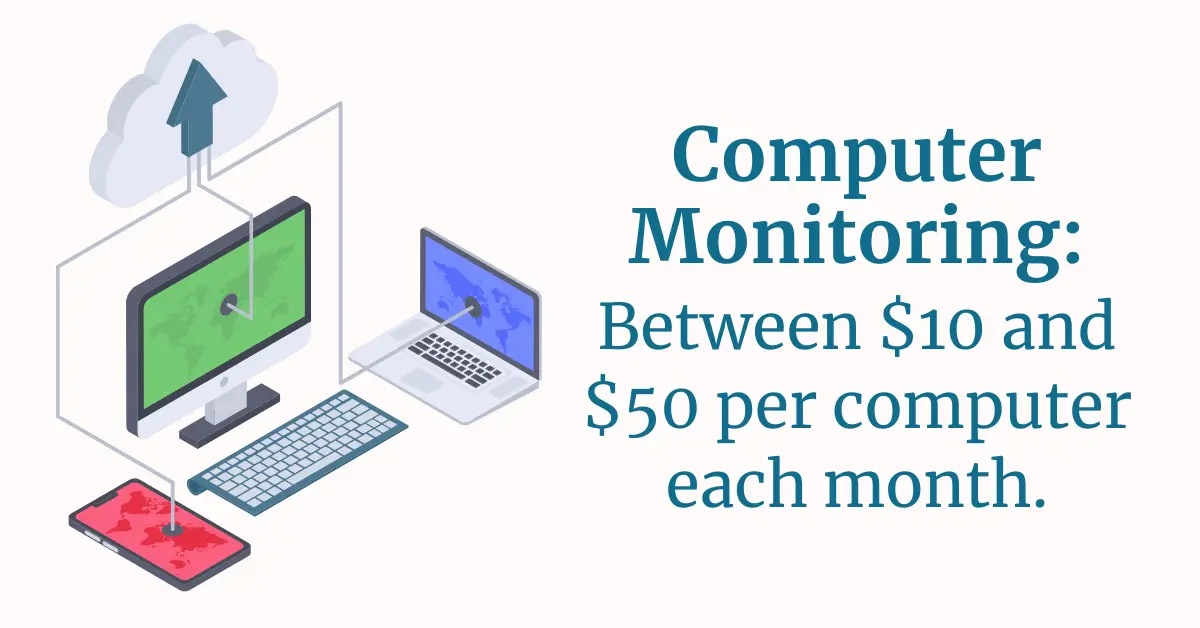
6.) Computer Monitoring
This is about keeping a close eye on your computers and your cloud space to spot any funny business.
You’ll need to join a service that does this monitoring for you.
Don’t worry if you’re not sure which one to choose, your IT provider can help you pick the right one.
How much will this cost you?
These services usually charge between $10 and $50 per computer each month. This is one of the bigger projects in CMMC, so it’s important you discuss this early with your IT vendor.
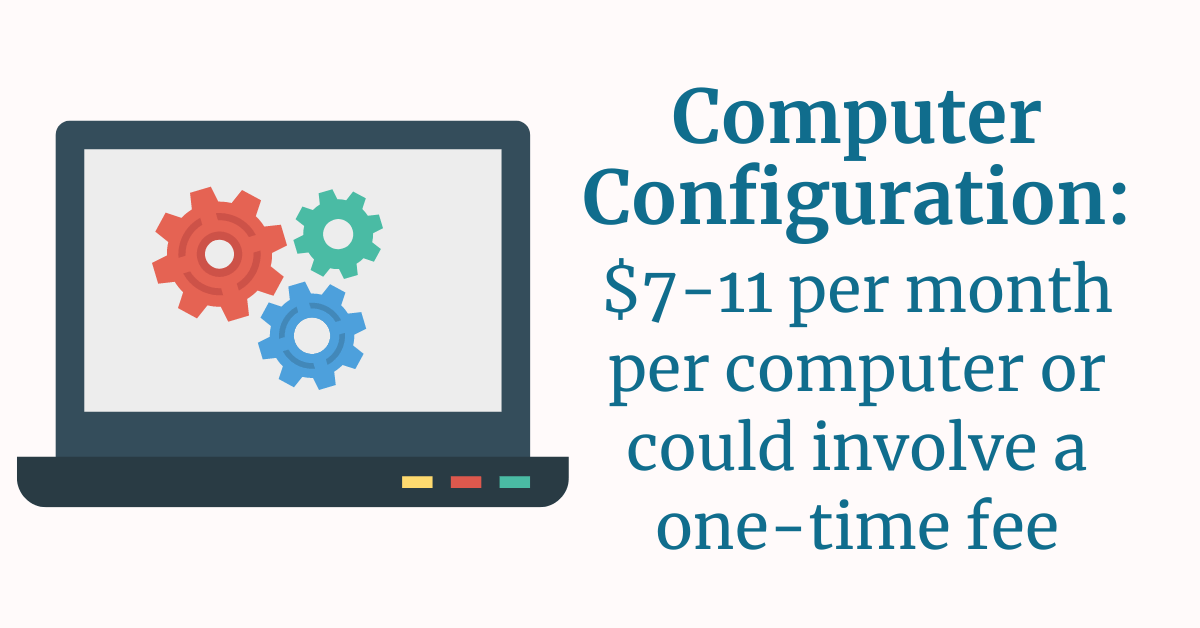
7.) Computer Configuration
Any computer that encounters your Controlled Unclassified Information (CUI) should be secured properly, often following protocols from organizations like the Center for Internet Security (CIS) or Security Technical Information Guides (STIG).
To meet these standards, your first step might be upgrading all computers to Windows Enterprise, the highest level of Windows.
This upgrade might cost between $7-11 per month per computer or could involve a one-time fee – ask your I.T. provider.
Following this, ensuring your computers align with CIS or STIG rules is essential.
This can be achieved using products like SteelCloud, although some clients report it’s fairly costly.
If you have an expert IT team, they could potentially set up the computers without SteelCloud, but beware – this a significant project requiring meticulous testing to ensure nothing goes wrong, and costs might exceed initial estimates.
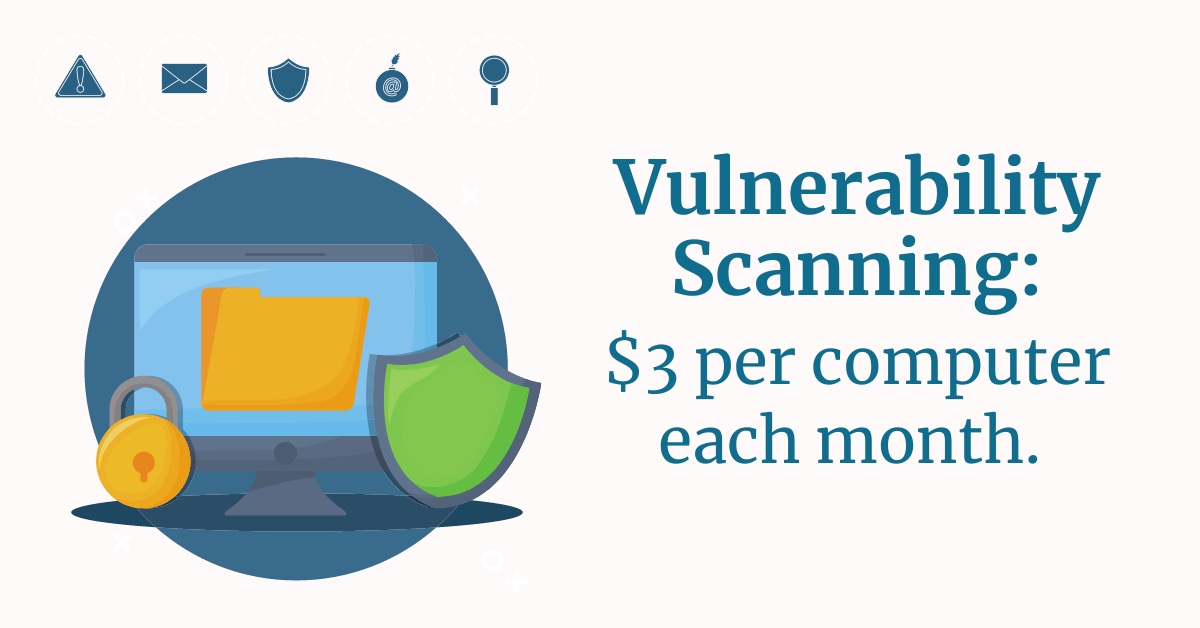
8.) Vulnerability Scanning
Vulnerability scanning is like a regular health check-up for your computer.
It searches for any weak points that could let in harmful software.
To do this scanning, you’ll need to get a service from companies such as Qualys, Rapid7, or Tenable.
The cost for these services typically starts around $3 per computer each month.
But remember, there’s usually a minimum purchase required.
So, you’ll have to account for that in your budget.
Your IT team might also offer a scanning service. But buyer beware, some cheaper services might not catch all the weak points. It’s always a good idea to test them against real computers.
9.) Wi-Fi Security
In order to enhance your Wi-Fi security to meet the requirements of CMMC compliance, several modifications are necessary.

Firstly, the practice of using a single, shared password for Wi-Fi access must be stopped.
Each user should have a unique method of connection.
It is advisable to consult your IT specialist about implementing an 802.1x system.
Further, it is essential that your Wi-Fi router sticks to specific security protocols.
In technical jargon, the router should be “FIPS 140-2 compliant”.
Should your current router fail to meet these standards, it’s best to invest in a new one that does.
The process of implementing these changes may require a significant amount of time.
Lastly, if you’re utilizing the Enclave strategy to conserve resources, it may be advisable to refrain from Wi-Fi usage entirely.
10.) Multi-factor Authentication
An important step in boosting security involves using multi-factor authentication (MFA).
For CMMC compliance, the rules around using MFA are much tighter.
If your employees have access to important information, they will need to use MFA every time they log into their computers, log into cloud services (like Microsoft 365), or connect to the network.
There are services available to help set this up.
Many businesses use Duo or Okta, and these generally cost between $3 and $9 per user each month.

However, your IT provider might also have other suggestions, so it’s always a good idea to discuss this with them.
11.) Mobile Devices
If any smartphones or tablets are intended to interact with sensitive data, such as Controlled Unclassified Information (CUI), it is necessary to establish a Mobile Device Management system.
Mobile devices, now integral to our daily routines, often facilitate our work tasks.
However, when these devices interact with significant data, additional precautions are crucial.

This is where the Mobile Device Management system becomes beneficial.
This system safeguards the information stored on your mobile devices.
Often, this service is part of your Microsoft 365 subscription, although an upgrade to a higher level may be necessary to use it.
Setting up this system, though, is not a straightforward process.
Expect to allocate between 10 and 40 hours of IT team labor for the smooth implementation of this system.
Their role includes establishing and rigorously testing the Mobile Device Management system to ensure its efficient operation.
12.) Physical Security
CMMC typically requires significant improvements to your building’s physical security.
This may include securing doors with locks or setting up surveillance cameras.
Depending on your situation, you might also need alarm systems, access gates, or even a badge system to monitor and regulate access to the building or specific sections within it.
Each organization is unique, so the security measures you need will be specific to your circumstances.
Remember the ‘Enclave’ approach? Where essential information is isolated to a limited area or select computers.
The physical security requirements for such an enclave tend to be simpler.
The focus would be primarily on securing a single room where important information is stored.
While this can simplify and potentially reduce the cost of the process, it may not be a feasible solution for all businesses.
Regardless, the ultimate goal is to secure your company’s information and meet CMMC requirements.
13.) Data Loss Prevention
If you use Microsoft 365, it’s important that your system is set up to watch for any sensitive data, like Controlled Unclassified Information (CUI), that might be leaving the company in ways it’s not supposed to.
Data Loss Prevention (DLP) is a tool that helps do just that, by watching for important information that might be leaving the company.
If your business uses Microsoft 365, you can add DLP to your current system.
Keep in mind, you might need to move up to a higher subscription level to get this tool.
After you have DLP, there is still work to do.
Getting this tool set up and tested takes time.
You should expect that your IT team will need to spend between 10 to 40 hours to make sure DLP is working the way it should be.
14.) Training & Awareness
Whenever new team member comes on board, they need to learn about the intricacies of security and CMMC.
But it doesn’t end there.
Since cybersecurity is a constantly changing field, it’s vital to keep everyone in the loop with ongoing training.
This training is usually priced around $2-5 per employee per month.

Yet, training alone is not enough.
You’ll need to keep your employees on their toes with regular phishing tests as well.
Regular phishing tests can help your team recognize and sidestep these threats, further strengthening your company’s security.
So, where can you get these services?
Well, you have options.
Companies like KnowBe4 offer such services, but you can also get them from your IT provider.
The choice depends on what fits your company best.
15.) Active Directory
Many of the CMMC requirements aren’t possible to implement without a domain.
If your team primarily operates within an office and you don’t currently have a domain, it’s definitely something to consider.
A domain (e.g. Active Directory) acts as a central hub for your computer network, providing the necessary structure for managing and controlling all computers and users securely within your organization.
Your IT company can provide a quote and guide you through the setup process.
It’s good to know that a significant part of the cost is tied to obtaining a server.
Servers allow for smooth data flow and operations.
While establishing a domain is a crucial step toward achieving CMMC compliance, it’s not a difficult one.
With the right guidance from your IT company, you’ll be well on your way to a more secure and compliant business operation.
16.) Tabletop Exercises
CMMC requires you to have a way to test your incident response plan.
This plan allows you to guide your team on what to do when a security incident, such as a cyber attack, happens.
One common and effective way to test your incident response plan is through a tabletop simulation.
This exercise helps everyone understand their roles better and lets you see how effective your current plan is, and where improvements might be needed.
But how much does a tabletop simulation cost?
The prices can vary widely.
You could expect to pay anywhere between $1,000 to $10,000, depending on the provider and the complexity of the simulation.

Chaostrack is a game-changer in preparing for cybersecurity incidents.
Our realistic simulations and interactive chatbot platform let your teams run continuous incident simulations tailored to your company’s needs.
Identify weaknesses, tighten security, and get valuable automated insights without the hassle.
Check out Chaostrack’s modern and effective approach by booking a demo here.
17.) Labeling
Under CMMC requirements, the labeling of certain assets is an essential task.
Specifically, it requires you to label computers, offices, and filing cabinets that contain Controlled Unclassified Information (CUI).
Even though it might seem like a simple step, it plays a significant role in maintaining the security of sensitive information.
By marking locations or equipment containing CUI, everyone in your organization is made aware of where this information is stored and is reminded to treat it with extra care.
This means labeling any computers, offices, and filing cabinets that hold CUI.
These labels can be easily purchased online, you can find vendors on the internet that provide labels specifically designed for CUI.
Remember, these aren’t just ordinary labels.
They serve as a constant reminder to everyone in your organization that the information contained within is valuable and needs to be protected.
So, while it’s a relatively small investment, it’s an essential part of ensuring the security of sensitive information and being one step closer to certification.
18.) Backups
Some companies discover they need to upgrade how they manage their system backups to meet CMMC standards.

The cost for this upgrade can vary a lot as it depends on your system’s configuration.
But what should your backups cover?
It’s important that they encompass both on-premise systems (the ones physically located at your business) and cloud-based systems (those that are stored online).
This way, all your important data, no matter where it is stored, is backed up and safe.
For your backups to be CMMC compliant, they must use an encryption method that complies with FIPS 140-2, a government computer security standard used to accredit cryptographic modules.
Since there’s quite a bit to consider when it comes to backups, your best bet is to speak with your IT provider.
They can give you a quote based on your specific needs and system configuration.
19.) Data Destruction
A key part of CMMC compliance is not just how we manage our data, but also how we dispose of it when it’s no longer needed.
When it comes to old hard drives and USB drives, simply throwing them in the trash isn’t an option as they may still contain sensitive information that could be recovered and misused.
Most companies choose to hire a local service provider to safely destroy old data.
It’s crucial to find a company with NAID AAA Certification.
This gives you the assurance that the company is properly trained and your data is completely destroyed.
Once data is destroyed, the company should provide you with a certificate of destruction.
This gives you peace of mind and helps document your adherence to CMMC compliance.
As for the cost, destroying old drives can range from $50 to $150 each.

However, the price can vary based on the company you choose and the specific services you need.
20.) Visitor Management Systems
Visitor management is crucial for maintaining CMMC compliance and safeguarding Controlled Unclassified Information (CUI) in your company.
Large companies can benefit from investing in a visitor management system that automates check-ins, tracks visitor presence, and restricts access to authorized areas.
This ensures proper protection for areas with CUI.
Smaller companies often rely on a logbook to control and record visitor access, but additional measures may be needed.
Consider reconfiguring office layouts, adding locked doors, or establishing separate visitor areas to prevent unauthorized access to CUI.
Regardless of your company’s size, implementing a visitor management system or taking additional measures is essential for CMMC compliance and maintaining the security of sensitive information.
21.) Remote Access
Remote access to company systems is essential, but not all remote access methods comply with CMMC requirements.
Whether using a VPN (Virtual Private Network) or a service like LogMeIn, CMMC guidelines stipulate that all remote access must meet certain requirements:
- It must be logged: This means there’s a record of who accessed the system when they accessed it, and what they did.
- It must be encrypted: Encryption is a security measure that transforms data into complex code. This process ensures that only individuals with the appropriate decryption key can access and understand the information.
- It should automatically log you out after a period of inactivity: This helps prevent unauthorized access if you accidentally leave your system logged in.
- It must be protected by multi-factor authentication: You might need a password (something you know) and a code sent to your phone (something you have), for example.
These requirements may mean that your company has to change or upgrade its current method of remote access.
That’s why it’s a good idea to speak with your IT provider.
They can tell you more about the systems they support, whether your current setup meets CMMC requirements, and how much any necessary changes might cost.
Ensuring secure remote access is a critical step in achieving CMMC compliance.
22.) Computer Encryption
If you’re dealing with Controlled Unclassified Information (CUI), CMMC compliance demands that all computers interacting with such data, whether they are servers or workstations, be encrypted.
To achieve this, many turn to encryption programs like Windows Bitlocker or macOS FileVault.

Here’s something important to note: while Bitlocker and FileVault come as part of their respective operating systems and don’t cost extra to use, they may not be compatible with all computers.
This incompatibility often occurs with older machines that were not designed with these newer encryption standards in mind.
So if your company uses older computers, you might have to consider an upgrade to newer models that support these encryption features.
To help you navigate this, reach out to your IT provider.
They’re there to guide you through this process, giving advice on the best machines for your needs that support encryption.
They can also provide insights on pricing and help you understand the cost of this essential part of achieving CMMC compliance.
Disclaimer

Before delving into the specific cost considerations, it’s important to note that CMMC is a complex regulation that is almost certainly going to be changing in the future.
Therefore, the information provided in this document serves only as general guidance and should not be considered definitive.
Following the official CMMC Assessment Guide for accurate and up-to-date information regarding compliance requirements is recommended.
Conclusion
As we wrap up, remember that achieving CMMC compliance is an investment in your company’s future.
It’s about more than just meeting regulations; it’s about taking proactive steps to protect your data, your reputation, and ultimately, your business.
Each component, from training your employees and managing visitors to system backups, computer encryption, and secure remote access, is part of your company’s cybersecurity.
Remember, cybersecurity is not a one-time thing.
It’s a continuous process that requires constant attention and improvement.
But with commitment, the right tools, and an understanding of the costs involved, you’ll be well on your way to achieving CMMC compliance and securing your company’s future in the digital age.
Stay safe, stay compliant, and continue to make smart investments in your company’s security.
Check Our Guides:
- Access Control (AC) Guide
- Audit and Accountability (AU) Guide
- Awareness and Training (AT) Guide
- Configuration Management (CM) Guide
- Identification and Authentication (IA) Guide
- Incident Response (IR) Guide
- Maintenance (MA) Guide
- Media Protection (MP) Guide
- Personnel Security (PS) Guide
- Physical Protection (PE) Guide
- Risk Assessment (RA) Guide
- Security Assessment (CA) Guide
- System and Communications Protection (SC) Guide
- System and Information Integrity (SI) Guide



