As part of our work helping medical practices with HIPAA and cybersecurity, we get to see lots of HIPAA mistakes. It’s interesting to spot the similarities across so many different companies.
Here are nine of the most common HIPAA mistakes that we see. The scary part is we see them all the time.
Is Your Business HIPAA Compliant and Secure? Don’t Wait for a Breach, Start your cloud security journey with our comprehensive audit.. Our specialists are committed to helping your business stay safe and seamlessly achieve HIPAA compliance and encryption requirements.

This one is super easy and makes a huge difference. Encryption makes the contents of your computer unreadable unless someone has your password.
Why is this important? Because computers, especially laptops, are very easy to lose or steal. You can leave them behind at the airport or the coffee shop. They can be stolen out of your bag or out of your car if you run in to do an errand. If your unencrypted laptop is stolen and it has PHI on it, you're going to be in a world of hurt.
By way of example, check out this news story. This medical practice was fined over $2 million:
Now this doesn't just apply to laptops. Desktops and all-in-one workstations should be encrypted too. Why? Because ALL computers are attractive targets for break-ins. If someone breaks in and steals your computer, you'll be really thankful if it's encrypted.
Just having encryption turned on isn't enough. You need to also make sure that you have proof of encryption. That way, in the event of a breach or a complaint, you can prove that encryption was turned on.
Proof of encryption can be quite simple.
When you're encrypting your hard drives, take a screenshot of the screen once encryption is turned on. Save that screenshot somewhere safe, like in a filing cabinet or securely backed up to the cloud. That way, you'll always have proof that your computer is encrypted. Just make sure to keep track of the name of the computer so that you can prove which one it was.
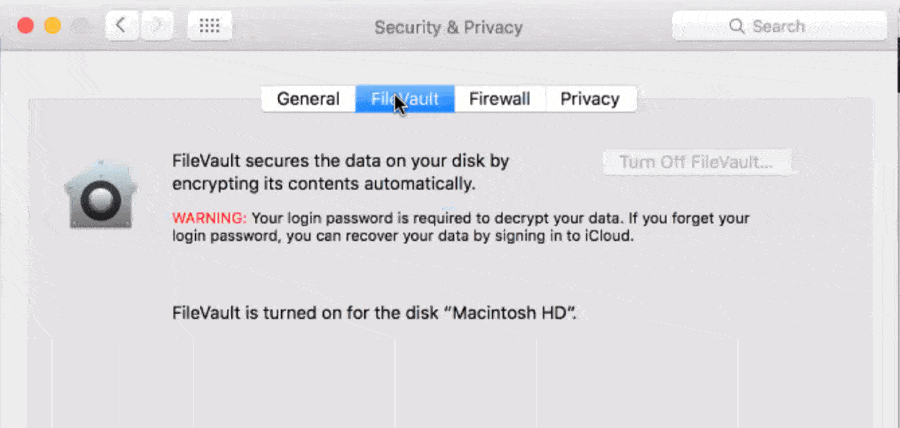
For larger companies, there are more sophisticated ways to do this. Scanning tools can log into each computer and confirm that encryption is turned on and properly configured.
We meet a lot of companies who are very proud of the fact that they have their computers backed up on a regular basis.
For small practices, the most common setup we see is a backup to an external hard drive, like a USB hard drive.
This is fantastic for a lot of reasons. A good recent backup is your best protection against ransomware.
Here's the problem though. A backup made to a highly portable USB device is just as likely to get stolen as a laptop. If that backup contains PHI and it's stolen, you're going to have a HIPAA breach on your hands.
Most backup utilities support encryption. Whether you're using the built-in utilities in your Mac or Windows machine or a third-party product, this is a very common feature. It makes this all the more unfortunate that most companies we see don't use it.

When you're setting up your backup, make sure that encryption is turned on.
Pro tip: take a screenshot to prove that encryption is turned on in case you have a lost or stolen USB drive.
Most small practices we meet have a local IT person who they call when they need help. They can help fix computers, troubleshoot internet problems, or set up a new system. Most tech folks are fully capable of tackling these items.
What they're not, though, is an expert in HIPAA or computer security. And that's a fatal assumption that most small practices make.
Most IT people can handle the basics, but they don't know the right things to do to protect medical practices.
In fact, most of the mistakes in this article were observed at companies that work with an IT person.
The liability falls on you to make sure that things are set up the right way, not your IT person.
That's one of the reasons that we started offering our services -- to make sure that we fill the gaps most IT people leave behind.
Most practices think that an antivirus program is enough. They think antivirus will protect them from attacks and breaches.
Nothing could be further from the truth.
Check out this article -- even Symantec says that "antivirus is dead." It's no longer effective at protecting computers.
This doesn't mean that antivirus is useless. Their (dramatic) point is that no single program can protect you against new types of attacks.
The problem with anti-virus is that it only does its thing after something bad shows up on your computer. And it only works if somebody else has already fallen prey to the exact same virus that you have on your computer. Unfortunately, hackers can now automatically make unique viruses for each person. This defeats antivirus.
As a company that handles PHI, you really need three layers of antivirus:
In security circles, this is called having a "layered defense." We provide all three of these layers as part of our services.
Having only one antivirus is like playing a soccer game with just a goalie. You won't last very long.
A lot of the smaller practices that we meet are using Mac computers. Macs are great -- they're user-friendly, they last a long time, and they come with great, useful programs.
However, they also get viruses. The idea of Macs being "safer" than Windows machines is a total myth.
In fact, this report shows that Mac malware has been growing massively in the past two quarters:
It's becoming a big problem. It's made even worse because most Mac users don't bother to install anti-virus.
Mac computers didn't get viruses for many years, but not because they are inherently safer. There weren't that many Macs in use, so hackers focused on the larger Windows population. Now that Macs are more common, malware authors are turning their attacks to Macs.
On both Mac and Windows machines, there are two types of user accounts that you can use for your day-to-day work.
One of them is an Administrator account. This account is the God of your machine, and it can do anything it wants. Unfortunately, this is the type of account that most people use every day.
The other type of account is called a Standard account. This type of user can do most things normally, but it is not allowed to do advanced operations on the computer.
As you can probably guess, we should all be using Standard accounts for our day-to-day work. Why? Because if a virus (or a hacker) gets on your computer, they can do whatever they want as an Administrator. They can install a program that captures every keystroke you type. They can turn on your webcam. They can steal your ePHI.
If they're on a Standard account, they will be seriously limited in what they can do.
Most practices we meet have some kind of training in place around HIPAA. They might have a policy document that employees have to sign. Or maybe a set of videos online and make their staff watch them when they're hired.
These trainings do a good job of teaching employees about HIPAA and handling PHI.
However, most of them are terrible at teaching about computers. And safe computing. And handling ePHI.
Staff members need to be trained on:
If your practice uses laptops, your staff also needs to be trained on security away from the office.
The stakes are too high just to ignore this critical aspect of working with ePHI.
Our services include both monthly computer security training and annual HIPAA compliance training.
Thankfully, we usually work with practices that have decided to do something about HIPAA and computer security.
For some, it's because they had a scare like a phishing attack or a ransomware incident.
For others, it's because they finally got around to it.
For many, it's because they're worried -- they know that hackers are targeting small businesses. They want to protect their livelihood and their reputation.

However, we do sometimes meet companies who keep putting security in the "later" pile. Or they make the mistake of assuming they're ok since nothing bad has happened yet.
HIPAA fines aren't getting any smaller. With each passing day of not doing something, the risks get higher. The risk of a nasty computer virus, opening the wrong email, or having a hacker come after your ePHI.
Ignorance is not bliss. It's irresponsible and could have some very dire consequences.
Get some free help! Check out our free 42-Point Checklist for ways to make your practice HIPAA compliant.
Have questions or feedback? Please share them in the comments below.
Like this article? Share it!
