Google Workspace HIPAA compliance can be confusing. A common misconception is that simply signing a HIPAA Business Associate Agreement (BAA) with Google automatically ensures compliance.
Nothing could be further from the truth. In reality, achieving a fully HIPAA-compliant setup including HIPAA compliant email setup requires proactive steps to configure and secure your Google Workspace environment properly.
Here's the story of Ted (not his real name). Ted runs a 30-person medical practice. Last year, Ted made the smart call to move his practice over to Google Workspace, Google's paid version of Gmail. Why is this smart? Because Google Workspace is super easy to use. Google has done a ton of work to make it super secure and HIPAA-compliant.
Sadly, the company that Ted worked with to set up Google Workspace didn't know much about HIPAA. They helped Ted sign a HIPAA BAA, but that was about it. After a cyber security scare a few weeks back, Ted got nervous. Was his Google Workspace HIPAA compliant? He worried that his staff might accidentally breach PHI. That they might share something they shouldn't. Or they might click on a link that they shouldn't.
He didn't want to end up on the HIPAA "wall of shame."
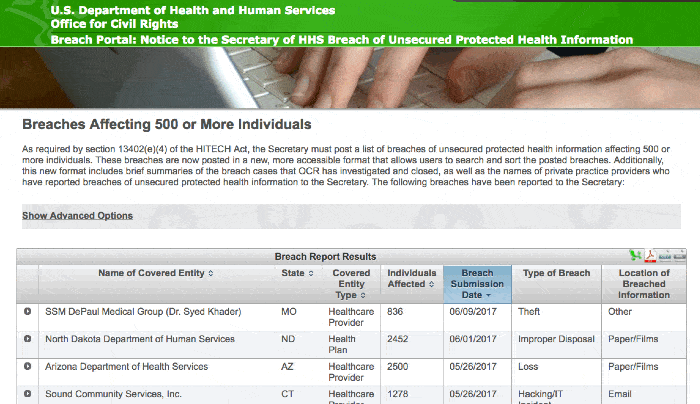
Ted made the right call. When we reviewed Google Workspace, we found a bunch of settings that weren't configured properly. Google Workspace has excellent security and can definitely be used to safely store and share PHI. But it's only secure if you set it up the right way.
Is Your Google Workspace HIPAA Compliant and Secure? Don’t Wait for a Breach, Start your cloud security journey with our comprehensive audit.. Our specialists are committed to helping your business stay safe and seamlessly achieve HIPAA compliance.

Here’s a disclaimer that many private practice “influencers” miss: signing a BAA with Google does not make your Google Workspace HIPAA compliant.
Seriously – Google CLEARLY says
“Customers are responsible for … ensuring that they use Google services in compliance with HIPAA.”
“PHI is allowed only in a subset of Google services.”
“These Google-covered services … must be configured by IT administrators to help ensure that PHI is properly protected."
So yes, Google Workspace CAN be HIPAA compliant, but it’s not compliant right out of the box.
You need to make sure your account is secure.
What our clients say
Google Workspace has hundreds of settings that you can configure. Set them up the wrong way, and you're exposing your company to a possible data breach.
Here are five of the most important settings to make sure you configure to be HIPAA compliant:
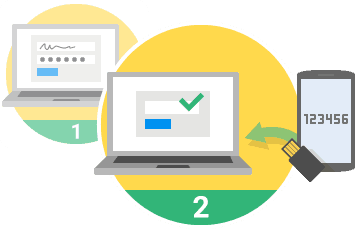 It's easier than you think for someone to steal your password. Even if your password is stolen, two-factor authentication keeps you safe.
It's easier than you think for someone to steal your password. Even if your password is stolen, two-factor authentication keeps you safe.
When you turn it on, your users will be asked to enter a six-digit code from their phone every time they log in.
The nice thing about the way Google has set up two-factor authentication is that it's smart. It bugs you every 30 days. It'll also bug you if something changes, like you log in from a new computer or a new place.
HHS specifically recommends two-factor authentication for systems that contain ePHI (like your Google Workspace).
Google is awfully smart about security. They'll tell you if a user does something weird. Like that time one of your users logged in from China an hour after being in Boston.
BUT you'll only get these notifications if you turn them on. They're turned off by default.
There are almost 20 alerting rules that you can set up out of the box and many, many more that you can turn on as custom rules. Go through each to make sure you'll get notified when something weird happens.
Google Workspace has dozens of settings that control your email security. Review every setting to make sure they're configured the right way. Specifically check for:
Did you know that you can see the password strength of your users right in the Google Workspace admin console?
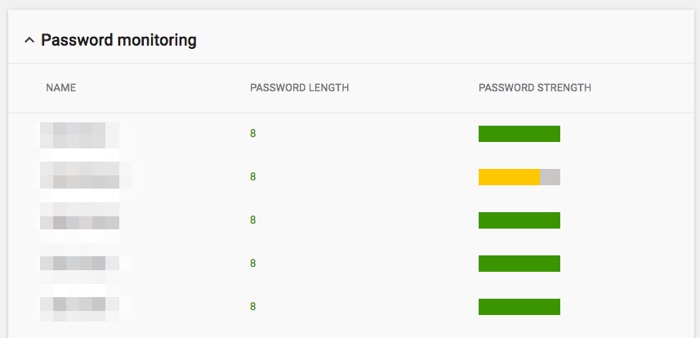
Most users have the bad habit of using a short password that they already know. This is a TERRIBLE idea for systems that handle ePHI like Google Workspace.
You can quickly and easily see which of your staff members are using passwords that are weak or too short. You can even set rules to force them to pick a longer, stronger password.
Google is very specific about which services you can use to store ePHI. As of the writing of this article, here are the services:
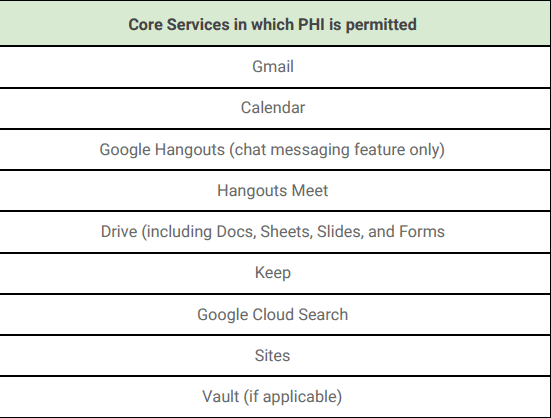
When you're setting up Google Workspace, be sure to disable unused services so your staff doesn't put ePHI in the wrong places.
Also, think hard about these 9 services that allow ePHI. Many of them aren't commonly used. If you're not going to use them, shut them down. That way, you drop the chances of accidentally exposing ePHI.
Google Workspace can be HIPAA compliant, but it's not compliant out of the box. To ensure compliance, sign a HIPAA Business Associate Agreement (BAA), enable two-factor authentication, secure email settings, set alerts, enforce strong passwords, and disable unused services.
To make Google Workspace HIPAA compliant, sign a HIPAA Business Associate Agreement (BAA) with Google, enable two-factor authentication, configure security alerts, ensure strong passwords, review email security settings, and disable unused services to protect PHI.
What our clients say

