They may be trying to steal 10 million dollars from you, but that doesn’t mean they have to be rude.
Last year, a company was hit with ransomware. Nothing unusual there.
But what makes this fascinating, and helps us to understand just how sophisticated these companies are, is the fantastic level of customer support the hackers provided.
The victim was directed to an online chat site, just like you would see if you reached out to Apple, Amazon, or a thousand other companies.
It couldn’t have begun more cordially.
The greeting came in a neat text bubble--a slicker look than you’d find on most corporate websites. The “Support” agent had an avatar: no skulls, no Guy Fawkes mask, no black hoodie, just a friendly J.J. Abrams-looking cartoon with glasses and a neat getup.
It was the kind of customer service experience corporate America strives for. Which only made the situation all the more surreal.
“Hello?” the victim replied, unsure.
The victim in this case was CWT Global, a travel management company. The kind of company that combines billion-dollar revenues with suspiciously little publicly available information online. A perfect target for ransomware, you’d have to say. The kind of target that justifies the ransom Mr. Support was about to ask for.
10 million dollars.
As a helpful reminder, the website featured a countdown clock. It was already running.
At 00:00:00, the ransom demand would expire. All 30,000 CWT computers would be locked up forever, and all of the company’s most sensitive data would be released onto the darknet, to be food for the sharks.
But Support wanted CWT to know that there was no reason to panic; everything was going to be fine, we’re all friends here.
How in the hell are you supposed to handle a situation like this?
When we ask, many business owners and executives say: “Simple. We’ll call IT.”
But if this is the first call you’re having with your IT, it’s already too late.
The sad fact is that all ransomware is preventable. The companies who have their act together don’t have to pay the ransom.
But guess what … if you waited until you’re hit to have that conversation, your hands are tied.
The only card you’ve got left is to negotiate down from lots and lots of money to just...lots of money.
The point here isn’t to learn how to negotiate with terrorists. It’s that these conversations should never have to occur in the first place.
None of these hackers are unique. They’re not new. They’re not nation states; they’re usually young guys from Eastern Europe and Russia. They’re not pulling off Mission Impossible stunts and exploiting secret, hidden holes in corporate networks, no--they’ve got mediocre malware, and the same strategies we’ve been seeing for years now, easily preventable with even moderately competent IT security.
If you get to this point, you’ve failed. A basic attack with an obvious solution occurred anyway, either by way of bad IT or bad management.
Knowing that? It’s almost worse than having to pay the money itself.
CWT Global ended up handing their attackers 4.5 million dollars in Bitcoin. If I were them, I’d have paid an extra 4.5 million just to avoid the embarrassment of what happened next.
You see, after striking their deal, Mr. Support decided to offer some final words of wisdom.
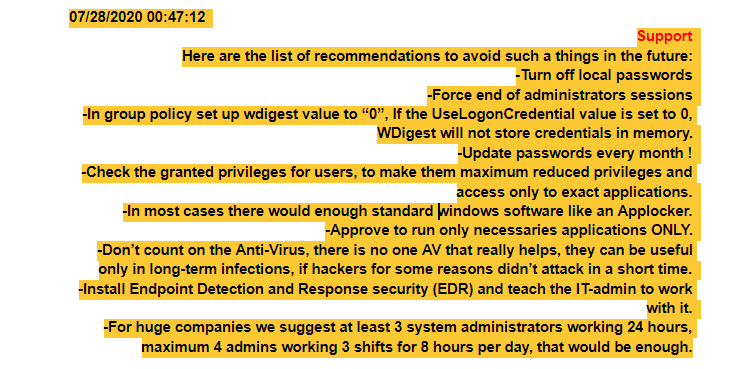
Poor grammar, wonderful advice. Maybe, if companies continue to ignore experts, they’ll at least listen to their extorters.
This is the most shocking part of this whole exchange. The polite hackers are actually giving you tips on how to prevent ransomware!
While we might not agree with all of the recommendations on their list (and we definitely see some missing), companies of all sizes should start having conversations about ransomware with their IT groups today.
We at Adelia Risk put together an article on how to build a Ransomware Playbook that can help you with these discussions.
Otherwise, you might end up like this poor small business owner, as reported by Cyberscoop--someone simply didn’t have the means to meet an international crime syndicate’s demands:
[. . .]
The attackers weren’t buying it. They wanted $100,000, and they weren’t going to relent. “We can’t do anything for you in this case,” they explained. “Sorry. The amount is insufficient in our business model.”
The victim finally agreed to scrounge up a few hundred more dollars, somehow. The attackers replied:
“Pity.”
