Wire fraud is a huge problem for Registered Investment Advisors. Every day, criminals trick firms like yours into wiring funds out of client OR firm accounts. What is the SEC Cybersecurity Guidance on wire fraud? And what are the best practices to stop wire fraud in firms today?
It’s critical that your staff identify these attacks BEFORE a wire is sent. Wires move money so quickly that it’s unlikely you’ll be able to get the funds back after they’re sent.
SEC Cybersecurity Guidance on Wire Fraud
The formal SEC cybersecurity guidance does not offer specific guidance on how to avoid or respond to wire fraud.
However, the SEC provides a lot of guidance on wire fraud via some other areas of published guidance. Two examples…
- The “Report of Investigation Pursuant to Section 21(a) of the Securities Exchange Act of 1934 Regarding Certain Cyber-Related Frauds Perpetrated Against Public Companies and Related Internal Accounting Controls Requirements” focuses on public companies. You should still read it, though. The lessons learned from the school of hard knocks apply to your firm too.
- The “Identity Theft Red Flags Rules” cover how to spot an identity theft attack.
If you have any questions about which of these apply to your firm, consult with a qualified compliance attorney.
Best Practices for Stopping Wire Fraud
The SEC guidance is a great start. We meet many firms, though, who aren't sure if they're doing all the right things.
To level the playing field, we want to share some of the best practices that we’ve observed.
First Layer of Defense: Train Your Staff to spot Wire Fraud
It can be tricky to spot a scam. Here are some tips to use in building your policies and training your staff:
- ANY email that’s asking you to wire money to a new location should make your Spidey-sense tingle.
- It doesn’t matter whether it appears to come from a client, a vendor, or even from someone inside your company.
- If the email is asking you to send to a foreign destination, be even more suspicious. That doesn’t mean domestic destinations are safe, though.
- Many (but not all) of these scams will have bad grammar or spelling mistakes. That’s a red flag.
- DON’T BE FOOLED if the email has a signature like “Sent from my iPhone - please excuse spelling mistakes.” This is a very effective way that they’re trying to trick you into excusing bad grammar or poor spelling.
- Many of these scams will make one of these pleas:
- urgency (“I need this wire right away or I’ll lose this real estate deal”),
- confidentiality (“please don’t tell my partner about this” or “this is a confidential merger”), or
- hardship (“Help, I lost my wallet while traveling”)
If an email appears to come from a client (or a vendor, or your boss), it DOESN’T mean that it’s legit.
Which brings us to our next point…
Second Layer of Defense: Technology to Stop Wire Fraud
The two most common ways that criminals will try to trick your clients (or vendors/boss):
- Steal their email account password. It's tough to spot these. The email looks VERY legitimate.
- Spoof their email address. "Spoof" means "send an email that looks like it comes from your client." These are easier to spot (more on this later).
The SEC Cybersecurity Guidance doesn't get to this level of detail, but here’s a checklist you can use with your IT team to lower the risk of spoofed emails getting through:
- Secure Email Gateway: Every email should be scanned by a “secure email gateway”. These are services that scan every single email before it comes to your inbox. The better ones have gotten very good at identifying scam emails.
- External Sender Notification: your email can be configured to warn you when an email comes from outside your company. Most of the time you won't need it. But it's a huge win if you get an email that might be from your CEO, and that message pops up. It will show you that it's actually someone trying to trick you. Here's an example:
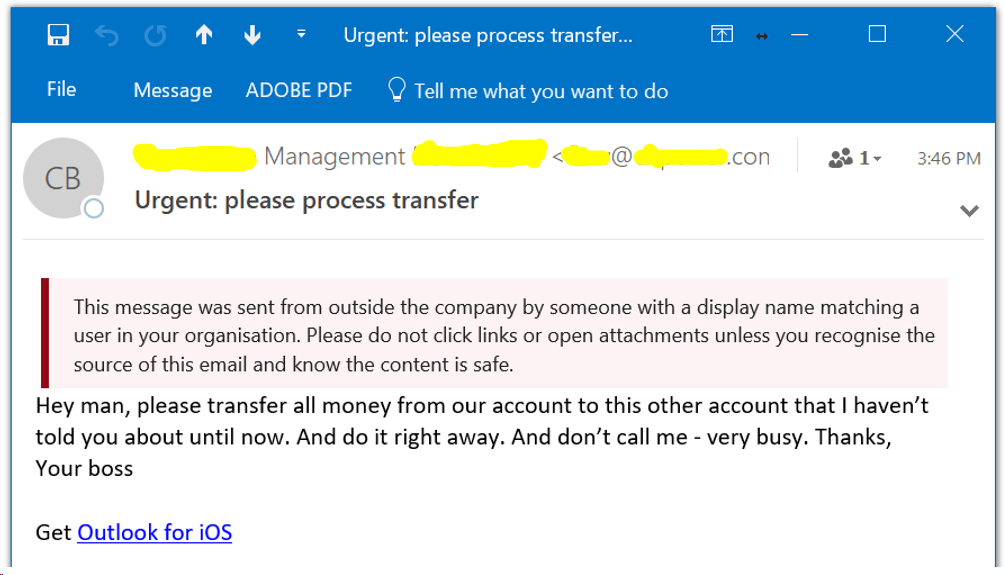 Funny example courtesy of https://gcits.com/knowledge-base/warn-users-external-email-arrives-display-name-someone-organisation/
Funny example courtesy of https://gcits.com/knowledge-base/warn-users-external-email-arrives-display-name-someone-organisation/
- Spoofing Defense: security experts have built three ways to block spoofed emails. At a bare minimum, you need to have SPF properly configured. If possible, you should also have DKIM and DMARC set up properly. Your IT team knows what these terms mean. If you're curious, though, here’s a helpful overview that describes how SPF, DKIM, and DMARC work.
We make sure these are set up the right way for clients of our SEC Cybersecurity Service.
Here’s the problem, though.
None of these technical solutions are 100% accurate. They’re only one line of defense. That’s why you need to focus on training your team to spot these attacks.
Third Layer of Defense: Spotting a Spoofed Email
It’s ridiculously easy for an attacker to set up a new website with a domain that can fool almost anyone.
How easy? It takes about 5 minutes and $10.
Since they’re trying to steal hundreds of thousands of dollars (at least), this time and expense is nothing.
You need to train your staff to spot emails that look legit, but aren’t.
Here’s a great article and infographic that shows six of the common tricks hackers use:
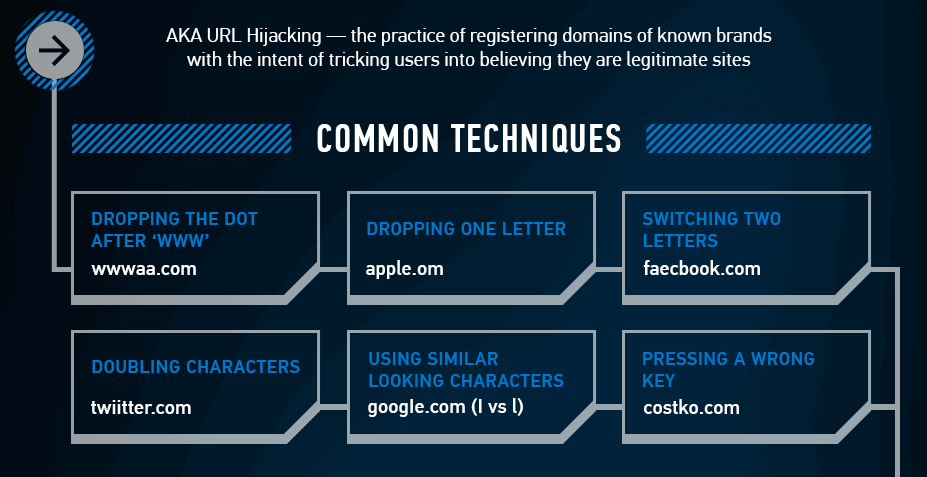
When you get a wire request, carefully examine the sender’s email address.
Don’t know how? Ask your IT person. They can show you where to see the ACTUAL sender based on your email system.
These tips to spot a spoofed email are a good start. They won't do much, though, if someone hacks your client's (or vendor's or boss's) email account.
That’s why you need…
Fourth Layer of Defense: Wire Transfer Verification Procedures
Your final step is to do everything you can to verify that the person who asked for the wire is legit. Here's where these best practices probably converge with the SEC Cybersecurity Guidance, specifically your Identity Theft Red Flags program.
Here’s where it gets tricky, though. If your client has had their email hacked, it’s quite possible that the hacker has their:
- Social Security Number
- Date of Birth
- Brokerage Account Numbers
- Mother’s maiden name
- Phone numbers
- And much more
If they can’t find them in email, they’ll just buy them off the black market, as reported to CNBC by security firm Radware.

In some cases, attackers have even redirected mobile phone numbers so inbound calls go to them. Remember -- there’s a lot of money at stake, so attackers take months setting it all up.
Here are some tips to have a good wire verification process (it'd be good to review your process with a compliance attorney to make sure it's compliant with SEC cybersecurity guidance):
1) Call the client to confirm the wire.
- NEVER call a phone number provided in the email. Insist on calling the client at a phone number you already have on file.
- NEVER text to confirm a wire. You have no idea who’s on the other end, phone numbers can be redirected, and texting probably isn’t set up to be compliant.
- Make sure to contact the ACTUAL person who initiated the wire. Some accounts are owned by multiple people (e.g., trusts). Make sure you’re contacting the person who will have first-hand knowledge of the wire.
- Consider sending a confirmation email to the email address ON FILE for the person initiating the wire. This will work if the attacker is spoofing their email, but not if the attacker has stolen their password.
2) Verify the client is who they say they are, and that they requested the wire.
- It’s a good idea to ask for at least TWO pieces of information.
- The best way to verify is to ask something that would be very hard for an attacker to know or get. For example, ask where you had lunch the last time, or the name of a common acquaintance. Find something only you and your client would know. It might sound very Jason Bourne, but remember -- a lot of money is at stake.
- If you don’t have details like this, you might need to resort to more common security questions. Examples include last four of social security number, date of birth, mother’s maiden name, etc.
- Some (but not all) firms won’t send a wire to a new destination without a form signed by the customer. This is a great verification step, but some thought needs to be given to how an attacker would get around it. Is the form delivered via email? What would stop an attacker from simply filling out the form and emailing it back? Is anyone actually comparing the signatures for validity?
- Some larger financial services companies are starting to require a PIN code. Clients must provide the PIN verbally to authorize a transaction. Again, this isn’t bulletproof, but it’s something to consider.
3) Follow a clear approval process
- Keep a log or shared notebook detailing the steps you took to verify the wire. This will help both for compliance reasons and to figure out what happens if an issue happens later.
- Many firms have a process in which large wires (e.g., >$50k) to a new destination need to be approved by a second person. Often times, this falls to the Chief Compliance Officer. Two heads are better than one.
But Wait - You’re Not Done Yet
If you realize that an email you received was an attempt to commit wire fraud, you have more work to do. If you're in compliance with the SEC cybersecurity guidance, you already have a documented Incident Response plan. Time to exercise it.
Here are some steps to consider as part of your incident response plan. Do these regardless of whether the scam was successful or not:
- If you fall for a scam, time is of the essence. You’re basically in a race to get the funds back before the criminal (very quickly) moves them to another account. As soon as you realize that something isn't right, escalate and pull your incident team together.
- You should report all scams (whether successful or not) to:
- Your company’s cybersecurity manager and Chief Compliance Officer
- Your IT team or IT provider
- Your secure email gateway vendor (so they can use the email to possibly tighten their rules)
- The fraud team at your brokerage or custodian
- You might be tempted to reply to the scammer, or to “string them along.” While it may be fun, don’t do this. You run the risk of making them angry, and they might start targeting your firm.
- Some (but not all) cybersecurity insurance policies offer coverage if an attack leads to money theft. Check with your insurance broker to see if you’re covered.
Pro Tip: Have this conversation before you’re attacked!
- Even if you were quick enough to catch it, you may have a very real problem on your hands. A client (or vendor or senior leadership) has had their account compromised. Make sure to give these people strong direction on steps they can take to avoid this problem in the future, like:
- Two-factor authentication
- Strong, unique passwords across sites
- Good antivirus on their computers
- Keeping up to date on security patches
SEC Cybersecurity Guidance: Compliance Makes Sense.
Can you or can’t you?
Some firms have the time and expertise to address all of this in-house. If you’re trying to build your own SEC Cybersecurity guidance plan, we hope you’ve found this guide to be helpful.
If you don’t have the time to build your wire fraud plan properly, or if you want to leverage the help of experts, we can help.
 Funny example courtesy of https://gcits.com/knowledge-base/warn-users-external-email-arrives-display-name-someone-organisation/
Funny example courtesy of https://gcits.com/knowledge-base/warn-users-external-email-arrives-display-name-someone-organisation/
