We've received a lot of questions about CMMC for MSPs. If you’re an MSP, you’ve probably been hearing about CMMC and NIST certification from current and prospective clients. It’s been a confusing couple of years as the DoD tries to solidify and communicate their CMMC program.
Government contractors will need to comply, but what about you? Does your MSP need to comply on some level as well? This article will explore some common questions we’ve received about CMMC and MSPs.
The US Department of Defense will require all vendors to have a cybersecurity maturity audit. Based on this audit, they will be assigned a rating from CMMC Level 1 to Level 5.
Starting next year, DoD RFP’s will state “you must be CMMC level X.” This is a gamechanger. If your client isn’t compliant by award time, they will lose the business.
No, but they’re similar. Your clients were supposed to comply with NIST 800-171 in 2017, and are technically in breach of contract if they don’t. However, most companies ignored it, so the CMMC was created to add enforcement teeth.
In November 2020, the DoD came out with the Interim Rule. This requires companies to perform a NIST 800-171 self assessment, fill out some documentation, and upload a score into the DoD’s SPRS system.
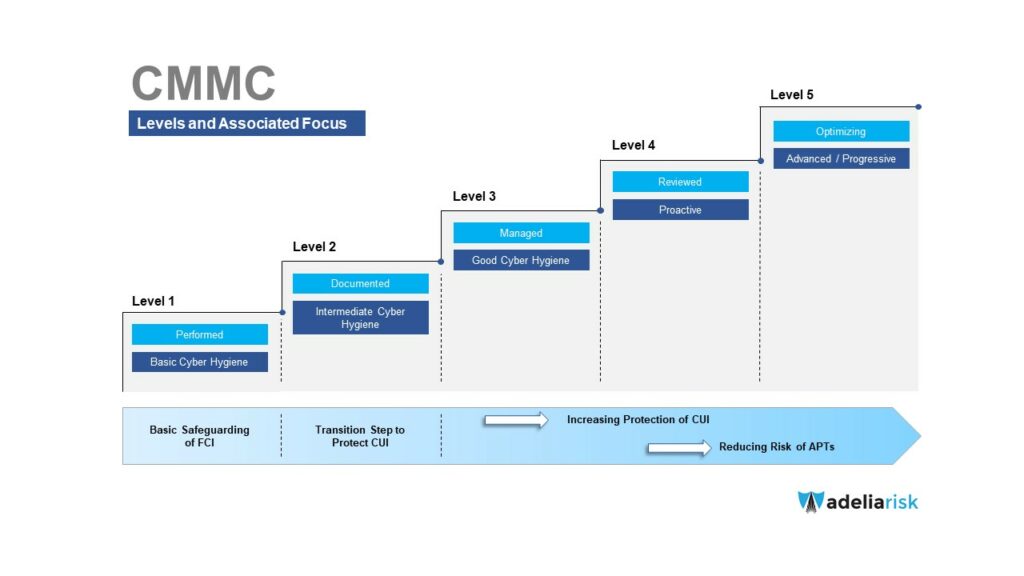
No. It takes, on average, 6-18 months to become compliant and the auditors are looking for processes to be in place at least 6 months before the audit. The DoD starts placing CMMC requirements in RFP’s in 2023. Keep in mind that over 300,000 businesses need to become compliant, and your client will be competing for resources to help. If they care about their DoD contracts, they should NOT wait. If they handle CUI, they will be required to get assessed at level 2.
If your client sells to the DoD (either directly or indirectly), they’re already being asked if they will be CMMC compliant and whether they have uploaded their self-assessment to SPRS. Take these surveys seriously. Use them to start the conversation about timing and budget.
This is the first conversation that you should have. CMMC compliance is not cheap, and often includes big IT projects. As their trusted advisor, you should have an honest conversation about whether their DoD business justifies the expense.
Based on our experiences, we estimate about half the time clients decide to bail on the whole CMMC process once they realize how expensive and time consuming the project is. We have a five-person firm who's going to be spending $50k when all is said and done (not with us -- on the whole project), and that's on top of a lot of person-hours for the client and the MSP. So hopefully before you spend a lot of time going down this path, you've had the "are you sure you really want to do this" convo with your clients.
Here are the typical phases of a NIST 800-171 and CMMC project:
This really depends on your client’s maturity, but these can be big projects for MSPs. Here are projects we typically see companies doing to comply with CMMC:
Each project is unique, but this should give you a sense of the size and scope of a typical CMMC project.
This depends on how well your client has stayed on top of IT and cybersecurity improvements.
There are three components to a typical CMMC project:
As you can see by the numbers involved here, it’s important to have an early conversation with your client to determine whether a CMMC project is worth it for their future business.
Adelia Risk’s CISO, Josh Ablett, is a CMMC Practitioner, and recently asked a group of CMMC practitioners this question. The answers he got back were "probably" and, more insightfully, "why would you risk it?" Since there are so many open questions still, we think a lot of companies are taking the most conservative route for all things related to CMMC -- like using the DoD's STIG for computer build standards instead of CIS, using only endpoint protection products that are FedRamp listed, etc. There's nothing that says you must do these things, but it makes it a lot more likely that you'll pass an audit without any hassle.
Some other MSP partners are taking a wait-and-see approach. They're continuing to work with the client for the time being, but recognize that they might lose the client once CMMC audits go live, since it's the right thing to do for the client (and if they don't want to make the internal investment themselves). As part of those discussions, we've talked about stripping out RMM and remote access tools (and just doing attended remote access, like via Zoom, for support), but we think everyone agrees that this approach runs some risk that a cranky auditor will fail them.
Another thing to consider -- sometimes the right answer for a company is to create a secure enclave for handling sensitive data, especially if they're using crappy old ERPs that are insecure. There's a lot that goes into figuring out if this is the right decision for the client, but in that case the MSP could probably continue to work with the main company and take a different approach to the enclave.
MSPs ask us about CMMC compliance, but they also ask about other security frameworks and auditing procedures, like SOC2. Does it make sense for your MSP to get a SOC2 or work towards CMMC compliance?
As with many things, there is no super clear answer on what to do.
On the SOC2 side, the answer is a little simpler - are you losing deals because you don't have SOC2 compliance, against competitors who do? Then, yeah, it makes sense to get a SOC2.
On the CMMC side, there is no clear guidance for MSPs – hence why we put together this article, to hopefully provide some clarity.
Every single thing in CMMC are things that MSPs should be doing, and in our experience in interacting with 60-70 MSPs is that most of them aren't. So yes, there's the business decision of "should we or shouldn't we comply with CMMC" to get more CMMC clients, but then there's also the moral imperative and legal risk for MSPs to be doing as much around their own internal cybersecurity as their clients think they are.
Our advice to MSPs, then, is that they should start working on implementing the technical control and process changes to support frameworks like CMMC or SOC2 as soon as possible. All of the documentation (and therefore a lot of the cost) can wait until there's more clarity about what's required, but in my experience it takes companies 6-24 months to just get everything in place, and by waiting they run the risk of losing business.
CMMC stuff feels like tedious compliance measures, but all of it is great information security practices. So beyond the investment for revenue, it's also an investment in making your core MSP safer.
In general, if you want to strengthen the internal security at your MSP, pursuing a SOC2 makes the most sense. The willingness to have an independent auditor come in and audit your stuff is what matters. If you are a CMMC client-heavy MSP, then pursuing CMMC and SOC2 may make the most sense.
We’ve worked with MSPs and government contractors for over 10 years on NIST and CMMC projects. Our CISO is a CMMC Registered Practitioner and can help you avoid high consulting fees with our Virtual CISO program.
