Why Avoid Phishing?
Phishing is the #1 way that companies get hacked.
Why? Because phishing works.
Check out these terrifying stats:
- 95% of all attacks are the result of successful spearphishing
- 1.5 million new websites are created each month JUST for phishing
- 76% of businesses have been the victim of a phishing attack
- Business have lost $12 BILLION to sophisticated phishing attacks
Yikes.
Most people don’t know how to avoid phishing.
We’ve put together the best tips and techniques that you can use to avoid phishing in your business.
1) Pay attention to phishing warnings
Most modern email systems do a pretty good job at warning you about possible phishing messages.
Many people ignore these warnings. They do so at their own risk.
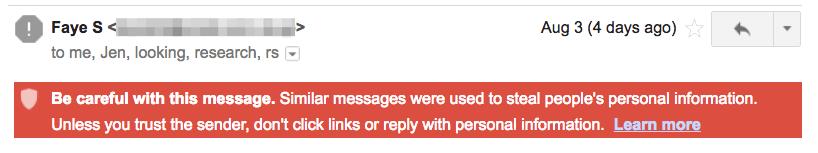
Here’s an example of Gmail’s warning:
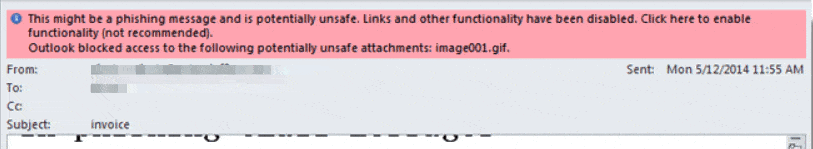
Even good ol’ Microsoft Outlook has a warning:
Lesson 1 to avoid phishing: train your staff to spot the warnings AND to pay attention to them.
2) Get a top-notch phishing scanner
Most companies use an email service, like Google Workspace or Microsoft365, that has email scanners built in.
These aren’t too bad, and can work fine for companies that don’t have a lot of sensitive data.
But most readers of our articles are in heavily regulated industries. Healthcare, financial services, manufacturing, etc.
You need a better scanner.
In fact, the best solution will use TWO scanners. The first should be from a company that focuses specifically on email security.
For the second, it’s fine to use your email providers scanner.
That way you get two levels of protection before your users even see an email.
We like and recommend a system called Proofpoint.
We’d be happy to tell you more about it during a HIPAA or SEC Cybersecurity Strategy Session.
The best email scanners will do two things…
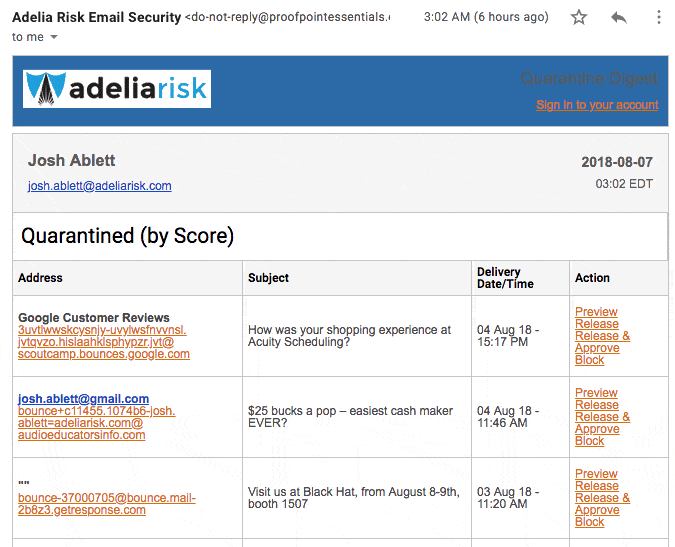
a) Each day, they’ll send you a digest of emails it blocks. You can then decide whether to keep them blocked or release them. This is WAY better than just having them dump to your Spam folder where you might miss something important.
b) Every time you get a link, the best systems will protect you.
When you click on a link, the systems will scan the destination of the link in real-time.
If the website you’re visiting is bad or new, you’ll be blocked.
Lesson 2 to avoid phishing: use a best-of-breed phishing email scanner, and teach your staff how to use it.
3) Be on high alert when an email asks you to do anything
If you’re training your staff on spotting phishing attacks, this is the SINGLE most important message you need to drive home.
You need to be on super high alert any time an email asks you to do any of the following:
a) Click a link
b) Open an attachment
c) Update personal information, like usernames or passwords
d) Transfer money or pay an invoice
e) Reply to an email (or trick you into replying to an email)
f) Sign a document (Docusign phishing attacks are incredibly effective)
By the way, it doesn’t matter who the sender is. We’ll talk more about this later, but you should be suspicious even if the email appears to come from your boss or a colleague.
Lesson 3 to avoid phishing: be on super high alert any time an email asks you to do something.
4) Go to the site, don’t click the link
If you get an email that appears to come from a service you use, stop.
Don’t click that link.
Instead, head over to the site directly and log in.
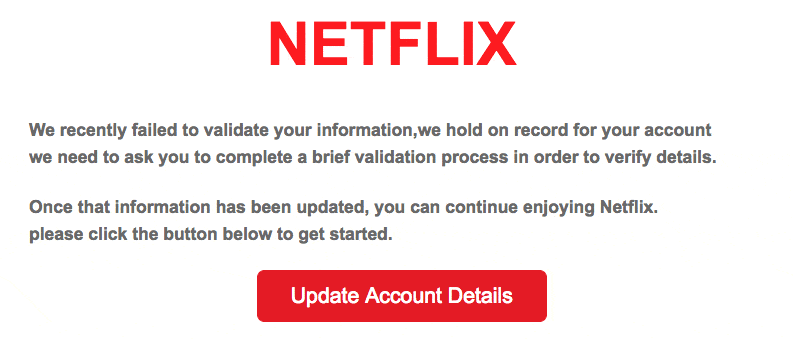
For example, see the “Netflix” message above? Clicking the link would have taken me to a phishing site.
But if I go to www.netflix.com and log in directly, I’m safe and sound.
And when I log in, their site is smart enough to tell me if I need to “update my account details” or not.
Here’s another example, even worse:
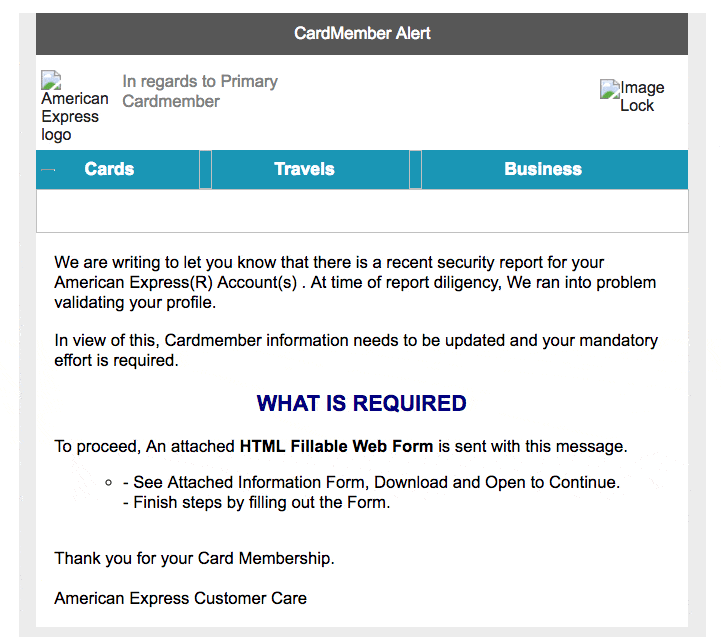
If I really think my Amex account needs attention, you’d better believe that I’m going straight to www.americanexpress.com.
Lesson 4 to avoid phishing: never click links for major services. Go straight to the site and log in.
5) Find the REAL sender
It is INCREDIBLY easy to make an email appear like it comes from any email address.
Don’t believe me? Try this: http://www.deadfake.com/Send.aspx
It’s a site that lets you send an email and make it appear like it comes from someone else. Give it a try. Just don’t do anything stupid.
For risky emails (#3, above), first check who REALLY sent your email.
How do you do this? Depends on what you’re using as an email client.
In Gmail, click this little arrow:
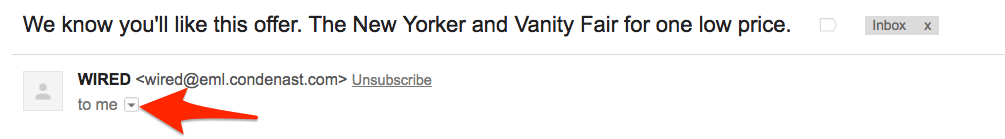
In Outlook, you can follow these step-by-step instructions.
For Outlook.com, you can follow these instructions.
The key thing here – don’t just assume that the email address that you first see on your screen is the correct one.
Here’s an example — in my inbox, this email appears to come from my friend Jim:
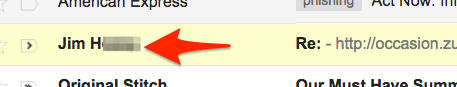
But when I click into it, it’s not from Jim at all…
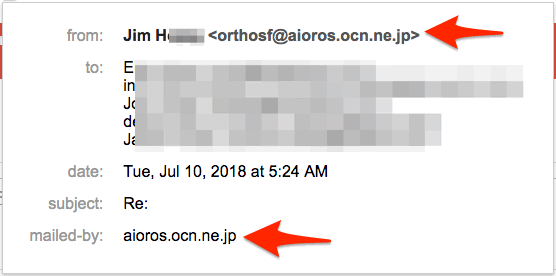
Lesson 5 to avoid phishing: You’ll have to click down deeper to see the REAL sender.
6) Watch out for Copycat domains
The first trick hackers do? They’ll send the email from a domain that looks similar to the company’s domain.
Here’s an example:

“aep.com” has nothing to do with American Express, but it sure sounds like it does!
Here are a few other examples — hacker sites on the left, legit sites on the right…
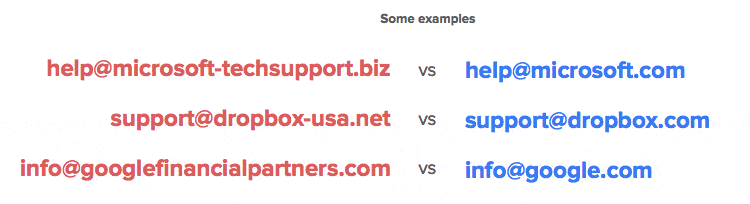
They might also try to use free email services, like this:
- microsoft.support@outlook.com
- dropbox-support@yahoo.com
- googlesupport@gmail.com
Lesson 6 to avoid phishing: check the sender and look out for copycat domains.
7) Watch out for Typosquatting
Remember how I said that hackers were registering 1.5 million phishing sites per month?
Here’s why.
Hackers use a trick called “typosquatting” to try to trick you into clicking on a link.
It’s easier to show than explain. Here are some examples from excellent cybersecurity company Anomali:
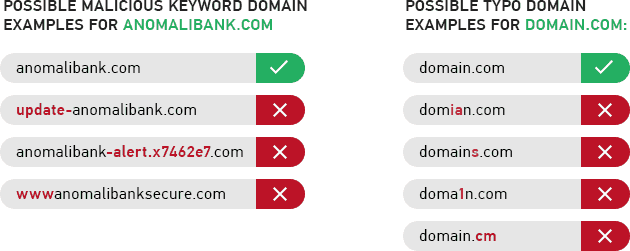
Lesson 7 to avoid phishing: train your team to watch out for typosquatting.
8) The Link Hover
Does your risky email have a link in it?
Here’s what you need to do.
Every single email program and web browser out there has a way that you can see where a link goes before you click on it.
All you have to do is hover your mouse over a link, but DON’T click on it.
First, let me show you how this works on a web page. This is an article we wrote recently about Wannacry ransomware. See the link on the page?
If I hover my mouse over the link, the destination pops up in the lower left-hand corner. Take a look…
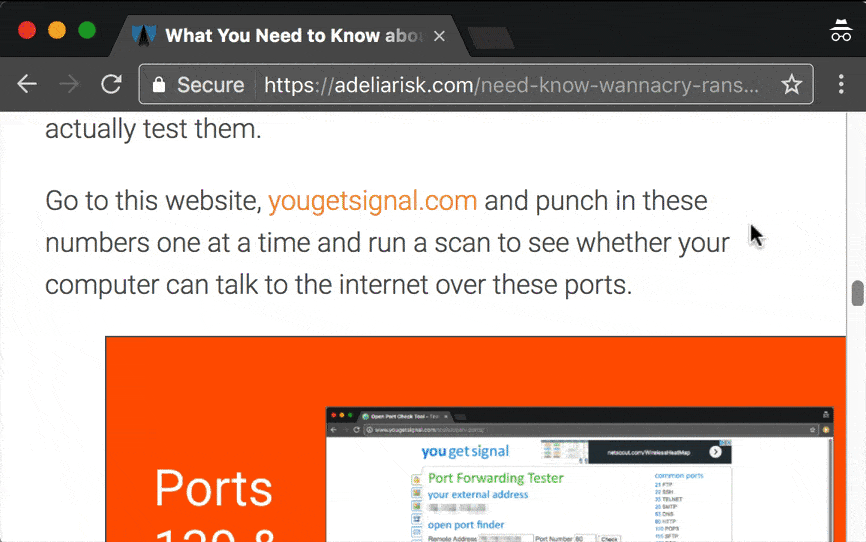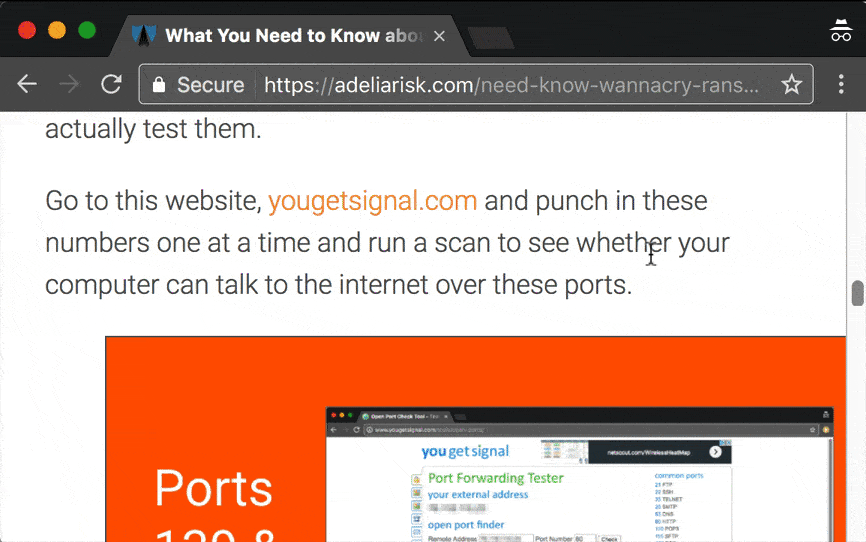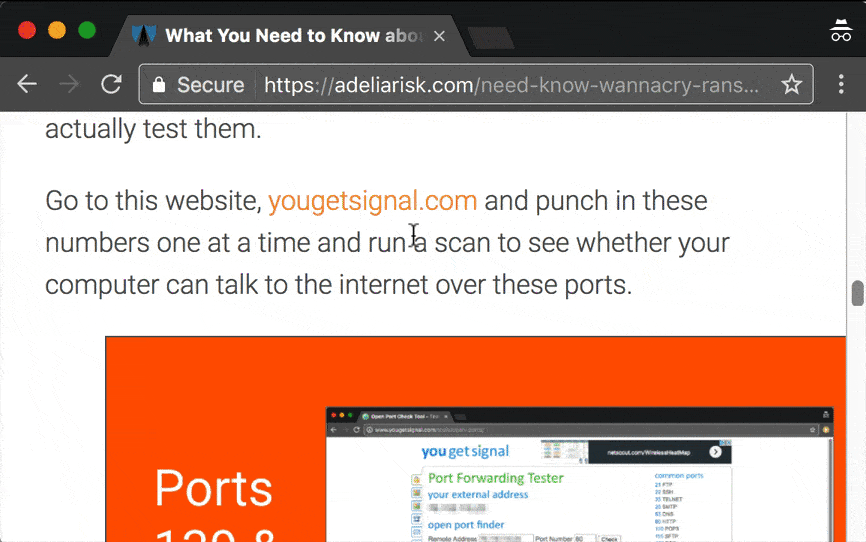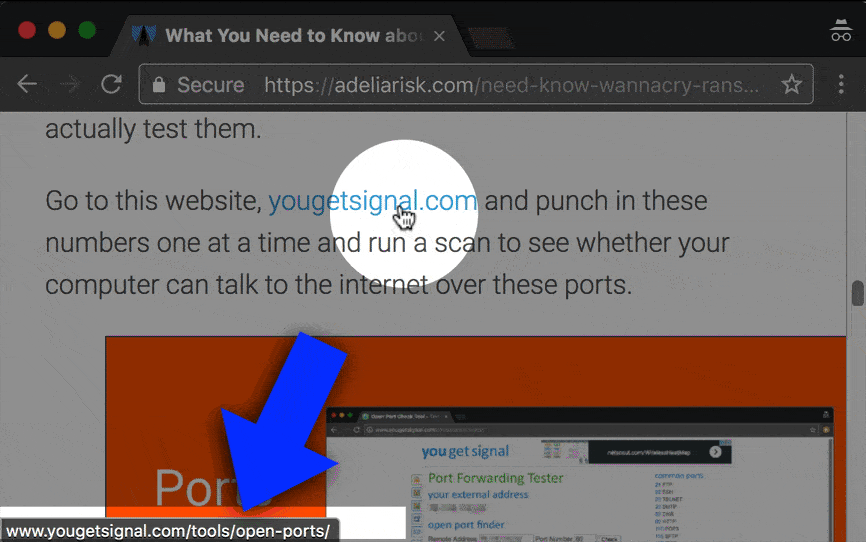
The location of the hover is going to vary based on what program and what browser you’re using.
Most of them are in the corner or will create a pop-up right on your screen.
After you do the hover, you’ll be able to see whether the link brings you to a legit site or a site that you don’t recognize.
Lesson 8 to avoid phishing: hover before you click.