So, you need to write an information security policy. And you’re totally overwhelmed.
Where do you start? What do you need? What should it entail?
You’re not alone. These are questions that we get a lot. It’s totally understandable. Planning, writing, and implementing a security policy can be seriously intimidating. If it’s poorly written or badly executed, a botched policy could cause major headaches -- and seriously harm the business.
But don’t worry. With the right knowledge and a bit of planning, you’ll be able to create a policy that will strengthen your security and your business as a whole.
Let’s define when an information security policy is -- just so we’re all on the same page.
An information security policy is essentially a set of rules that dictate how digital information should be handled in a business. Depending on the size of your business, that might sound like overkill. But it isn’t.
Every year that passes -- heck, every month that passes -- brings us new technology. Desktops. Laptops. Tablets. Smartphones. Smart watches. We’re constantly changing the way we use technology to interact with the world around us. And naturally, the way we handle data evolves, too.
An Information Security Policy forces you to think through and address all of the ways that data is handled in your business. More importantly, it outlines how you’ll keep your data safe -- even though there are thousands of ways that it could be breached.
A good information security policy sets clear, defined boundaries for how users should be using company technology. Plus, it acts as a contingency plan for how you’ll handle the situation if -- or when -- things go wrong.
That’s important, right?
If you’ve never done it before, writing an information security policy is a big undertaking.
But, there’s good news. We’re lucky enough to live in an age where unlimited information is at our fingertips. There are thousands of resources out there to make this easier. The hard part is finding them.
So we’ve decided to take the grunt work out of the picture and compile a list of our favorite information security policy resources. Below, you’ll find a list of 13 great resources to help you on your journey. We’ve included tools, articles, guides, websites -- anything that we thought might be helpful.
Once you’ve gone through these, you’ll be set up with a solid foundation and ready to write your information security policy!
We have a lot of resources listed below, and you can absolutely create your own Information Security Policy without outside help. But hiring a Virtual CISO will definitely make the process easier and will strengthen your overall cybersecurity program.
Key Elements of an Information Security Policy, The Infosec Institute
These are some of our favorite articles from blogs, magazines, and other websites scattered across the web. A lot of these are especially good for getting a more high-level overview of what goes into writing a good security policy.
Key Elements of an Information Security Policy
This guide from the InfoSec Institute outlines the key sections of an information security policy. It’s a bit of a dense read, but it contains some great information. If you’re looking for a solid overview of what your information security policy should entail, this is a good place to start. Plus, it includes some helpful examples of policy rules.
Building and Implementing an Information Security Policy
Depending on your current level of security awareness, you might already be familiar with SANS Institute (System Administration Networking Security Institute). The SANS Institute is a terrific source for security research, training, and information.
This whitepaper outlines how to design, create, and implement an information security policy. It’s particularly helpful because the writer is clearly speaking from experience and talks you through the entire process. None of it sounds scripted or overly-academic -- it’s just good, practical advice. It’s probably the oldest resource on the list, so take some of the specifics with a grain of salt. But a lot of the advice here about structuring and implementing a plan is timeless.
How to Write an Information Security Policy
This CSO Online article gives a super-helpful high-level overview of writing an information security policy. The article is a few years old now -- it was published in 2009 -- but it contains nuggets of information that are timeless. We especially liked the parts that address implementing a policy within the greater ecosystem of the business. Lots of security professionals think of writing an information security policy as putting pen to paper. But really, the process starts a lot earlier than that. It’s critical to blend security policy with the management philosophy of the organization, and this article does a good job of addressing that.
An Incremental Approach to Building an Information Security Program
This article outlines an incremental approach to rolling out an information security program. Its scope is a bit wider than just writing an information security policy itself. But, it’s important to understand how your policy will fit into a greater security strategy. This article does a good job of explaining what goes into an infosec program rollout. It includes great tidbits like how to calculate a risk score and how to handle iterative auditing. It’s geared towards educational organizations, but the information can apply to lots of different types of businesses.
Cybersecurity Preparedness Assessment, Cyber Houston
Templates, calculators, generators, analyzers -- you name it. These are some of our favorite security policy tools and templates. If you use them right, they could take a lot of the grunt work out of the process.
The FCC’s CyberPlanner is a free tool that generates customizable cybersecurity plans for small businesses. It’s a few years old (the tool was released in 2012), but it’s still applicable. In particular, this one will be helpful for very small businesses. It’s a great way to start building an information security policy if you don’t have the time or dedicated staff to work on one from scratch. Plus, it still gives you some flexibility into what you can include.
NIST’s Cybersecurity Framework is a massive collection of guidelines created to help businesses manage cybersecurity. It’s a terrific resource for organizations that are mature enough. Security leaders at Fortune 500 companies use it to help craft their security plans -- it’s serious stuff. But, be warned: this is probably overkill for small businesses looking to create a simple security policy. It’s a lot of information, and it can be dense and overwhelming even for security experts.
This might be a good tool to help strengthen an existing security policy or for people who are already pretty knowledgeable about cybersecurity issues.
Get your free Information Security Policy Template
We need to mention our free resource here. This is the same template we use to create Information Security Policies for clients. Use it to create a new Information Security Policy or revise your current one. The template includes 42 policy sections to consider and is suitable for any size of business in any industry.
As a Virtual CISO service provider, we’ve created and improved hundreds of Information Security Policies.
SANS Security Policy Templates
This is one of the most useful pages on this list. SANS has compiled a giant database of information security templates for public consumption. The list includes just about any kind of infosec document you can think of -- from remote access policies to information logging standards to your typical clean desk policy. All of these are offered as both PDF and DOC downloads. They’ll give you an excellent starting point when you’re ready to put your information security policy into creation.
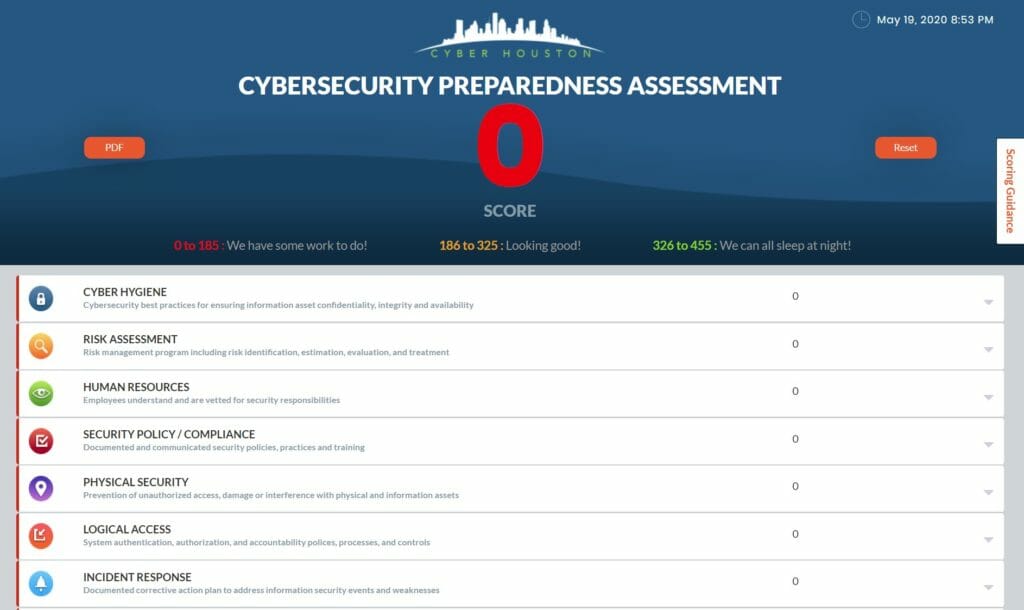
Cybersecurity Preparedness Assessment
This is a really easy-to-use tool. Either print out the PDF and fill it out by hand or use their online tool. Either way, you’ll go through the questions and calculate your score. It’s a great way to get some high level insight into your company’s cybersecurity. Some of the categories should definitely be included in your information security policy: incident response, business continuity and vendor management to name a few. This tool was created by Cyber Houston, which helps businesses in the Houston area stay safe and secure.
There are lots of websites out there that are teeming with hundreds of security articles. These resources are just too strong to leave out. Not all of these directly relate to information security policies specifically, but they all contain invaluable security knowledge. You should keep all of these in mind as you build your greater security program.
HealthIT.gov is a massive website created by the US Department of Health to help healthcare providers, patients, and IT workers make sense of PHI protection. There’s so much great information here that we probably have barely even skimmed the surface ourselves.
If you’re in the healthcare field in particular, this will be invaluable to you. But even if you aren’t, you can still learn a lot here. You may not need to be HIPAA compliant, but the security needs of non-healthcare organizations are still similar enough that many of these articles hold true regardless of industry.
CERT Enterprise Risk and Resilience
CERT has a long history of providing helpful, in-depth security resources. Unsurprisingly, they have a huge section of articles and research specifically geared towards enterprise risk and resilience The articles on this page aren’t quite as basic or high-level as some of the other items on this list. But there are still some terrific pieces of information in here. If you’re willing to wade into some denser territory, you could learn things that will help you put together a stronger security policy.
The Cybersecurity & Infrastructure Security Agency (CISA) is an excellent resource to consider when it comes to information policies for cybersecurity. As the operational lead for federal cybersecurity and the national coordinator for critical infrastructure security and resilience, CISA's mission is to reduce risk to the nation's cyber and physical infrastructure. CISA offers a wide range of resources and tools, including guidance documents, best practices, training courses, and vulnerability assessments, that can assist organizations in creating and implementing effective cybersecurity policies. By leveraging CISA's expertise, organizations can enhance their security posture and better protect their critical assets and data against cyber threats.
TechTarget: Information Security Policies, Procedures, and Guidelines
TechTarget has a whole section on information security policies, procedures, and guidelines. There are a ton of articles and resources here, so these are a few articles that may be good to start with. Just a note, you’ll have to register with a corporate email address to view these:
No matter what, writing an information security policy is going to be a big undertaking. It takes a lot of research, a lot of introspection, and a lot of collaboration from all areas of the business. Even in a perfect world, that’s not an easy task.
But hopefully, these resources have given you a jump start. With the help of guides, research, and templates, you can reach a stronger finished project. No one will be able to give you all the answers. There’s no magic, perfect template out there. But it’ll give you a jump start!
Don’t forget to request our free template! You can get it for free, here.
There are many companies out there that will gladly take your money in exchange for a 200+ page generic Information Security Policy.
This is a bad move, and we need to tell you why.
Having a big-ass policy may seem good, but a policy is worthless if no one reads, understands, or follows it.
And it will make you look really bad in an audit.
So if you’re going to hire a firm to write your policy (even us) make sure you know what you’re getting, and make sure it will work for your specific company and industry.
We specifically work with small and medium-sized businesses (fewer than 250 employees) in highly regulated industries like financial services, healthcare, and government contracting.
Our clients are happy with the results - here’s what Charlie, an Investment Advisor from FL had to say:
"Like most investment advisors, I wanted to worry less and prepare for our next audit. Other vendors offered confusing "one size fits all" solutions. Since working with Adelia, we've built a policy that we understand and can achieve! We passed our most recent audit with flying colors."
