CMMC and NIST 800-171. Every day we receive emails and phone calls from companies that need help with compliance. Preparing for CMMC certification is a huge undertaking, and you should start preparing NOW if you haven't already.
The NIST 800-171 deadline was December 31, 2017, and CMMC is rolling out now. If you’re a government contractor, you’re probably familiar with NIST 800-171. But what about CMMC? It’s in the process of being created but will be the new standard for future Department of Defense (DoD) contracts. Both NIST 800-171 and CMMC pertain to information security processes and standards.
This article will be updated as more information becomes available.
According to the National Archives and Records Administration (NARA), Controlled Unclassified Information (CUI) is:
...information that requires safeguarding or dissemination controls pursuant to and consistent with applicable law, regulations, and government-wide policies but is not classified under Executive Order 13526 or the Atomic Energy Act, as amended.
What does that actually mean? CUI is information created or owned by the US government and needs to be protected due to a law, regulation or government-wide policy. Instead of using designations like “For Official Use Only” or “Sensitive But Unclassified”, the designation CUI is used instead.
The CUI Registry contains information about the categories and subcategories of CUI. It specifically states what is considered CUI and how to properly mark the information.
NIST 800-171 was developed by the National Institute of Standards and Technology (NIST) to provide standards of protecting CUI. NIST 800-171 contains 109 specific things that you, as a government contractor, must do to help protect the United States against cybersecurity attacks. The deadline for compliance with NIST 800-171 was December 31, 2017.
Hackers want to learn what you sell to the government (and in what amounts) to gain intelligence about US government activity and military plans. By implementing NIST 800-171, the DoD was trying to make it harder for cyber attackers.
NIST 800-171 contains a long list of security requirements. This can be quite overwhelming for small firms. There are 109 specific task items within these 14 control families:

If you’re a government contractor and need access to CUI, you must follow the security procedures outlined in NIST 800-171 and verify compliance. Your customers should have audited your compliance with NIST 800-171.
You need to prove that your computers are protected against hackers, that your staff knows how to handle confidential government data and that your team knows how to spot a cyber attack AND how to handle it responsibly. And, most importantly, you need to protect your revenue by proving that you were open and transparent when you said “yes, we comply with NIST 800-171.”
The Cybersecurity Maturity Model Certification (CMMC) is in the process of being created. It contains 17 capability domains and 5 levels of cybersecurity maturity. CMMC will serve as a verification method to ensure compliance with certain cybersecurity practices to protect CUI.
The Department of Defense (DoD) is planning to shift to the CMMC framework to create a unified cybersecurity standard for DoD contracts. According to The Office of the Under Secretary of Defense for Acquisition and Sustainment (OUSD(A&S)), “security is foundational to acquisition and should not be traded along with cost, schedule and performance moving forward”.
Basically, too many contractors didn’t comply with NIST 800-171 before (or after) the deadline, so the CMMC is a reaction to that. Contractors will need a valid CMMC certification (of a certain level) to bid or win a DoD contract. Allowing firms to self-certify their compliance with NIST 800-171 is not working, so they’re moving towards a third-party audit process with CMMC.
The Interim Rule solidifies that CMMC will be the new framework for DoD contracts moving forward. Contractors are required to report a self-assessment score based on NIST 800-171.
You should upload your score now if you haven’t done so already.
There are 17 capability domains within CMMC, many of which you’ll recognize from the NIST 800-171 control families. Domains designated with * are not included with NIST 800-171.

There are 5 maturity levels. Higher CMMC levels means higher restrictions and advanced cybersecurity protections. Hot
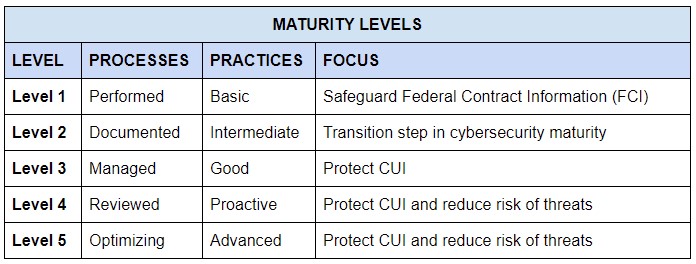
Your company will need to achieve a certain maturity level depending on what type of information (whether that’s FCI or CUI) your company needs to protect.
*Note for MSPs: Only a very small percentage of government contractors will be over Level 3. You shouldn't need any full-time staff to be added (like a full-time security person) for Levels 1-3. It will still be a lot of work if your clients don't have anything in place, but you don't need to go crazy on monitoring and staffing. If your client isn't very large, then you probably don't need to worry about Level 4 or 5.
17 Total Practices
Level 1 Organizations focus on protecting Federal Contact Information (FCI) and need to follow the basic safeguarding requirements.
71 Total Practices
Level 2 Organizations need to establish and document practices and policies. Level 2 includes some NIST 800-171 requirements and only a subset of practices concern CUI protection.
130 Total Practices
Level 3 Organizations focus on protecting CUI and must follow all of the security requirements in NIST 800-171 plus additional practices.
156 Total Practices
Level 4 Organizations work to protect CUI from Advanced Persistent Threats (APTs). In addition to following
171 Total Practices
Level 5 Organizations need to standardize and optimize processes across their organization, since you’ll be protecting CUI from APTs.
Nov 2020: DFARS Interim Rule became effective. CMMC will be phased in over the next 5 years.
2021: 15 contracts anticipated to have CMMC requirements*
2022: 75 contracts
2023: 250 contracts
2024: 325 contracts
2025: 475 contracts
Until 2025: the Office of the Under Secretary of Defense for Acquisition and Sustainment must approve the inclusion of the CMMC requirement in any solicitation.
*estimated targets listed under FAQ #26: https://www.acq.osd.mil/cmmc/faq.html
So how do you receive your CMMC Level? Your organization will need to be certified. There won’t be an option for self-certification.
The Cybersecurity Maturity Model Certification Accreditation Body (CMMC-AB) is a non-profit, independent organization overseeing CMMC Third Party Assessment Organizations (C3PAOs) and individual assessors.
The CMMC-AB’s website indicates that the CMMC is still being finalized, so there are currently no complete standards to follow (yet) and no training for assessors (yet).
CMMC-AB Registered Practitioners (CMMC-AB RP) provide advice, consulting and recommendations to clients regarding CMMC. They receive training and assist with implementing programs that align with CMMC standards.
Adelia Risk’s CISO Josh Ablett is a CMMC-AB RP, and specializes in CMMC Level 3 Certification. We've helped clients with cybersecurity since 2010 and with NIST 800-171/CMMC since 2017. We offer a tried-and-true, repeatable process to find your gaps, build a plan, and work with you to get where you need to go. Learn more: https://adeliarisk.com/virtual-ciso-service/
Even without a complete standard to follow, your organization can get started on a self-assessment by utilizing the most current CMMC Model. Assessing your organization against NIST 800-171 would also be wise.
Near the end of this article you’ll find a sample compliance checklist and direct links to NIST 800-171. We cannot stress enough that if you are a government contractor and want to continue working as a government contractor you need to be prepared for a CMMC audit. The best way to prepare for the CMMC audit is to comply with NIST 800-171 ASAP. Then, once CMMC is fully finalized you won’t have an overwhelming amount of work to do.
Adelia Risk can assess your business and identify gaps with NIST 800-171. We help you demonstrate compliance at the lowest possible cost. Learn more: https://adeliarisk.com/virtual-ciso-service/
As we’ve explained, there are similarities between NIST 800-171 and CMMC. Both regulations pertain to cybersecurity standards and protecting CUI. Here are some major differences:
Complying with NIST 800-171 is very close to achieving CMMC Level 3. This means there are two “lower” levels of CMMC, which essentially scales down the cybersecurity requirements for smaller organizations. This also means there are two “higher” levels of CMMC, which include additional practices and standards.
Not really, but it's a great place to start! If you're aiming for CMMC Levels 3-5 you should definitely work on getting compliant with NIST 800-171, since those levels contain the standards of NIST.
Adelia Risk can assess your business and identify gaps with NIST 800-171. We help you demonstrate compliance at the lowest possible cost. Learn more https://adeliarisk.com/virtual-ciso-service/
Small firms, this section is for you! You may be wondering about the overall cost for compliance. For the clients we work with (even small ones), it's usually at least in the tens of thousands of dollars between the audit, the documentation, and all of the technology fixes required. It's definitely worth asking "are you sure you want to keep doing business with the DoD" before you go too far down the path.
In terms of getting your arms around cost, here's what we typically see small companies need to do to get there (this isn't a complete list, just some of the big things):
And the list goes on. That's not meant to be exhaustive, and during your gap assessment you might find good reasons why some of these aren't necessary. Check out the 21 Most Common CMMC Technology Projects.
Securing the DoD Supply Chain: Experts discuss CMMC’s impact on suppliers: video featuring DoD CISO Katie Arrington
CMMC Model: Overview briefing, current Model and Appendices
CMMC Accreditation Body Website
CMMC Audit Preparation - Community Resources
NIST 800-171 v2 - use for self-assessment before a CMMC audit
National Checklist Program Repository - NIST 800-171 security checklists
The deadline for NIST 800-171 has long since passed. Whether you self-certified your organization or put it off, you can’t do that for much longer. CMMC encompasses NIST 800-171 and there won’t be an option for self-certification. If you have contracts with the DoD, you will be audited by the CMMC-AB. So it’s best to prepare sooner than later if you want to continue with government contracts.
Use NIST 800-171 and the current model of the CMMC to start preparing for your CMMC audit.
Adelia Risk can assess your business and identify gaps with NIST 800-171. We help you demonstrate compliance at the lowest possible cost. Our CISO Josh Ablett is a CMMC-AB Registered Practitioner and specializes in CMMC Level 3 Certification. Learn more: https://adeliarisk.com/virtual-ciso-service/
Have questions or feedback? Please share them in the comments below.
Like this article? Share it!
